Practice Free 350-901 Exam Online Questions
AppGigabitEthernet interface is used as data port for a container on a Cisco Catalyst 9000 Series Switch.
Which two interface configuration options should be used? (Choose two.)
- A . trunk interface
- B . bridged virtual interface
- C . SPAN port
- D . management interface
- E . subinterface
Refer to the exhibit.
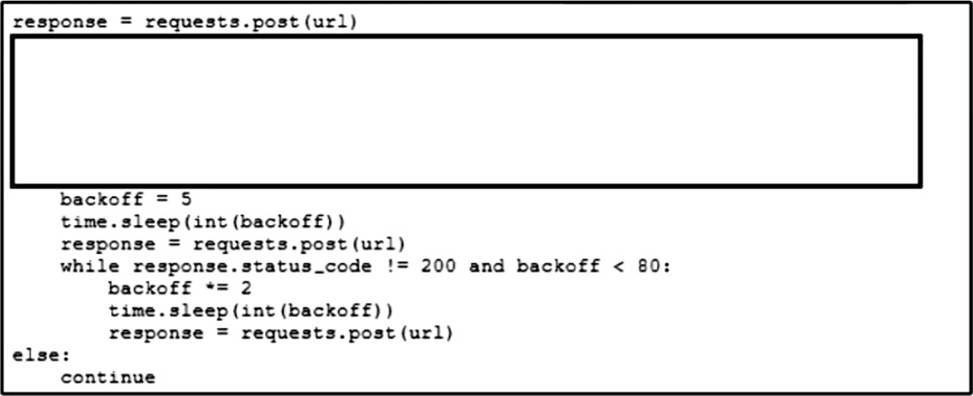
An engineer needs to implement REST API error handling when a timeout or rate limit scenario is present.
Which code snippet must be placed into the blank in the code to complete the API request?
A)
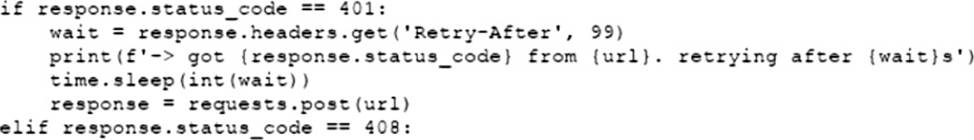
B)
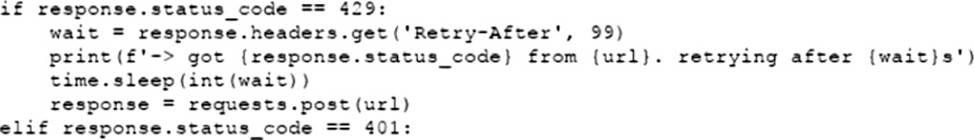
C)
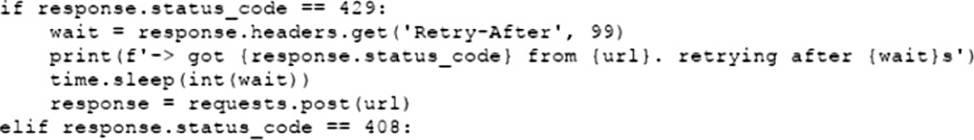
D)
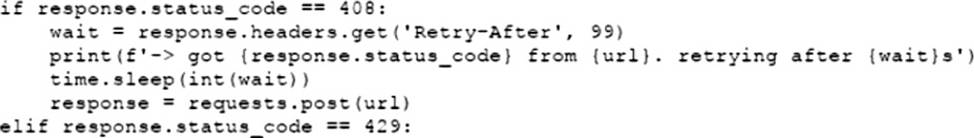
- A . Option A
- B . Option B
- C . Option C
- D . Option D
DRAG DROP
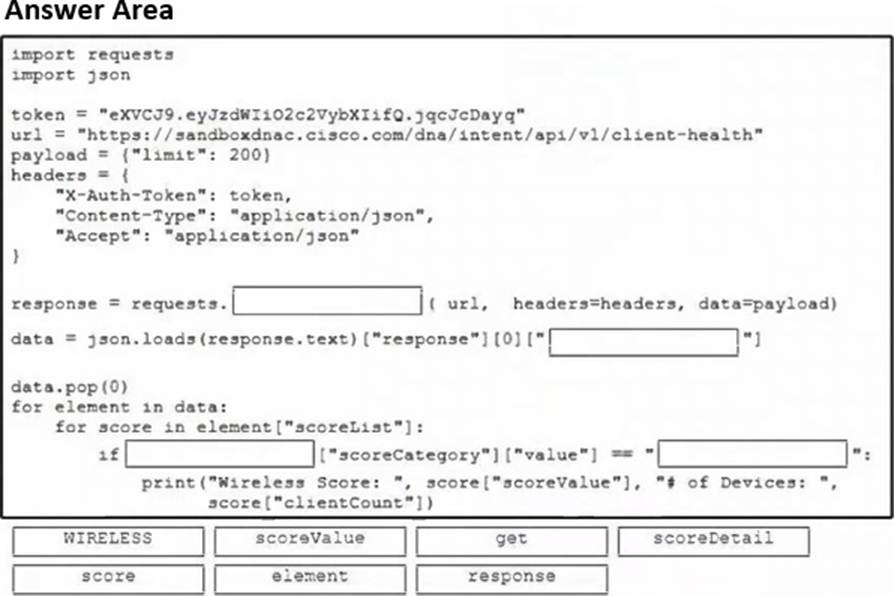
Refer to the exhibit.
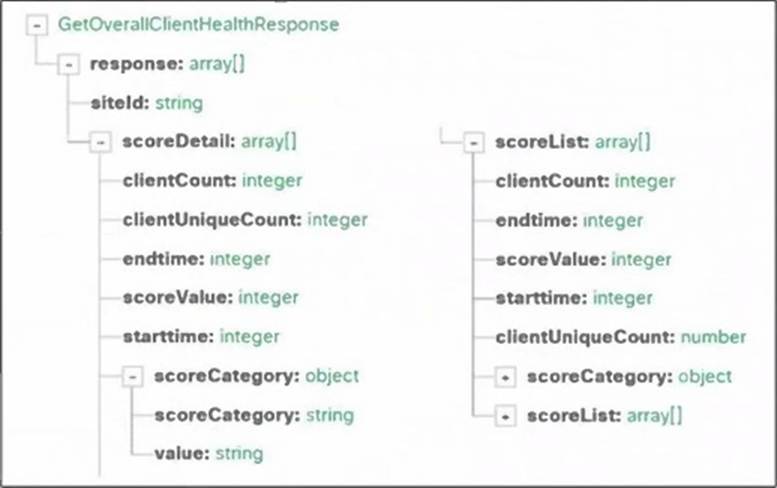
Drag and drop the code snippets from the bottom onto the blanks in the script to print only wireless device health information. Not all options are used.

Which method of addressing data privacy concerns should be considered during the development process of an application?
- A . Set X-Frame-Options: DENY in the header.
- B . Deny all requests on the web application firewall.
- C . Ensure that data is encrypted at rest.
- D . Ensure that a firewall runs on the server.
A developer creates an application for a Cisco Catalyst 9000 switch in a Docker container.
Which action must be taken to host the application on the switch?
- A . Export the application as a TAR file and import the file to the switch.
- B . Connect the switch to Cisco DNA Center and push the application through the platform.
- C . Use the Cisco IOxClient tool to export the application to a ZIP file and push the file to the switch.
- D . Copy the application code to a NETCONF file and upload the file to the switch.
Refer to the exhibit.
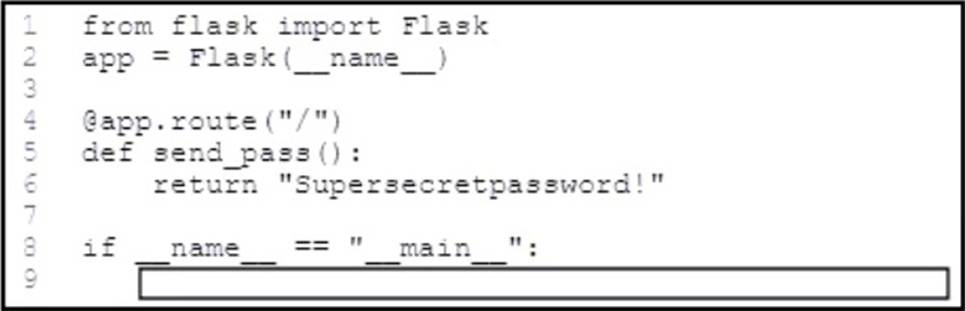
An application uses an API in Python using the Flask framework, which will be used to send sensitive data. The data must be secured while in transit.
Which code snippet must be placed in the blank in the code to meet this requirement?
- A . app.run(ssl_context=(None))
- B . app.run(ssl_context=(‘cert.key’, ‘key.pem’))
- C . app.run(ssl_context=(‘cert.pem’, ‘key.pem’))
- D . app.run(ssl_context=(‘cert.pem’))
C
Community vote distribution
C (100%)
A developer is adding a user experience improvement to an application and is working on a fork. The developer must push a new branch named ‘devcorexpv4g4h1h1y1r5l3w1t4’ to the remote repository named ‘PRODdevcorv01h1t2d1w5i6j4a5b’. The local branch must be updated to include any new changes that were pushed to the remote repository from other developers.
Which Git command must be used?
- A . git reset -f
- B . git fetch -f
- C . git merge –all
- D . git pull –all
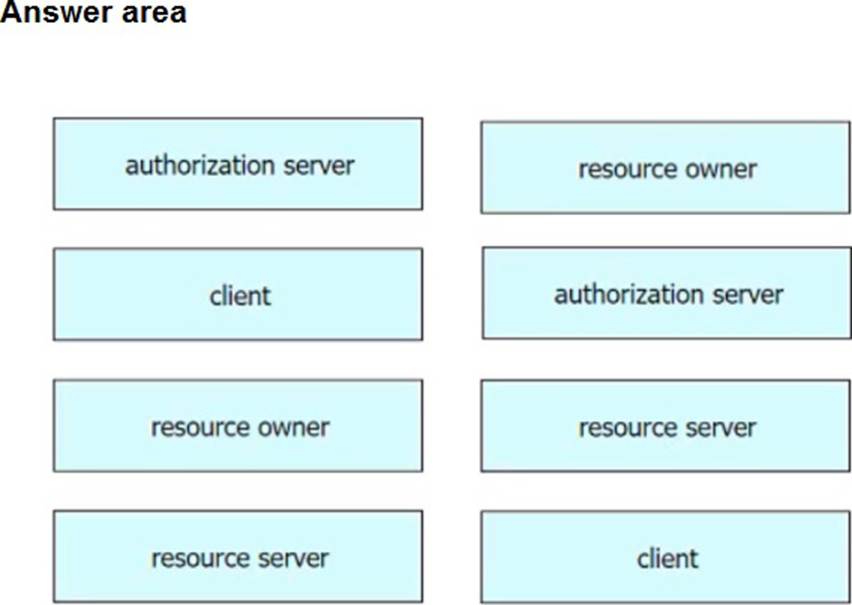
DRAG DROP
Refer to the exhibit.
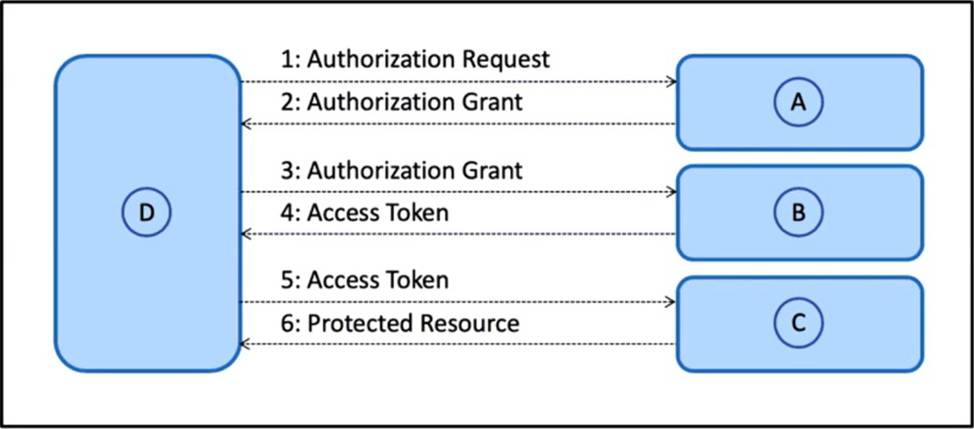
Drag and drop the components from the Oauth2 authorization protocol flow on the left onto the letter that matches the location in the exhibit.

Which solution is used to manage automatic dependencies on a Cisco NCS device using Cisco IOS XR Software?
- A . peer code reviews
- B . CI/CD pipelines
- C . flexible packaging
- D . automated deployments
An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
- A . Update the base image of the containers.
- B . Test the execution of the application with another cloud services platform.
- C . Increase the number of containers running per service.
- D . Add consistent “try/catch(exception)” clauses to the code.
