Practice Free 350-901 Exam Online Questions
Refer to the exhibits which show the documentation associated with the create port object API call in Cisco Firepower Threat Defense, and a cURL command.
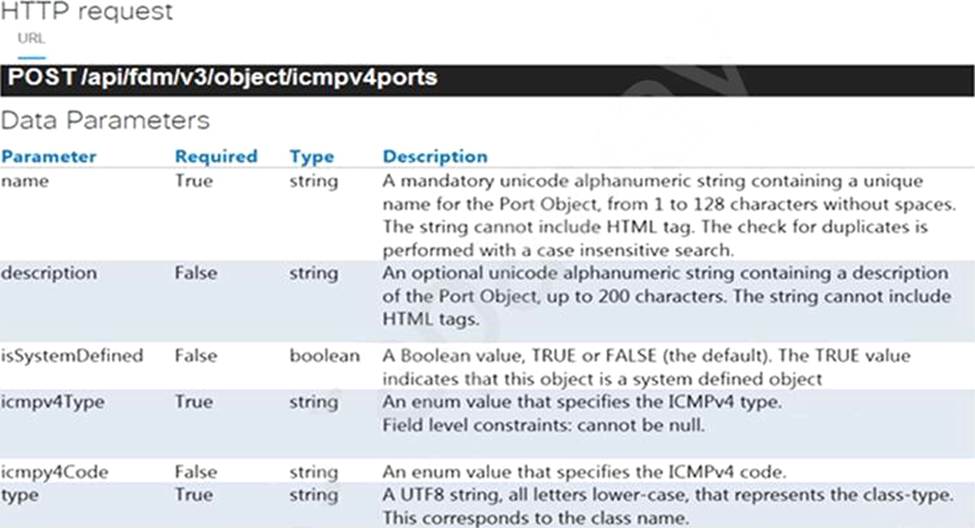
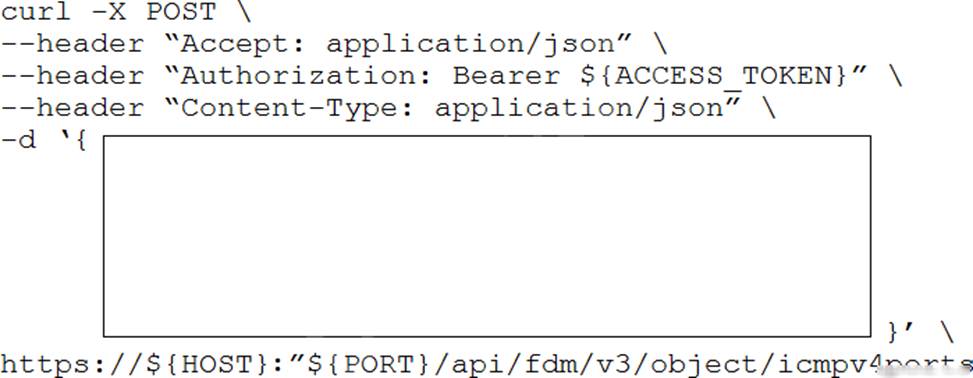
Which data payload completes the cURL command to run the API call?
- A . "icmpv4Type": "ANY", "name": "string", "type": "icmpv4portobject"
- B . "description": "This is an ICMP Echo", "icmpv4Code": "8", "icmpv4Type": "Echo", "is System Defined": true, "name": "ICMP Echo", "version": "2.2"
- C . "description": "string", "icmpv4Code": "ANY_IPV4", "icmpv4Type": "ANY", "id": "string", "is System Defined": "string", "name": "string", "type": "icmpv4portobject", "version": "string"
- D . "description": "string", "icmpv4Code": "ANY_IPV4", "icmpv4Type": null, "is System Defined": true, "name": "string", "type": "icmpv4portobject"
Refer to the exhibit.
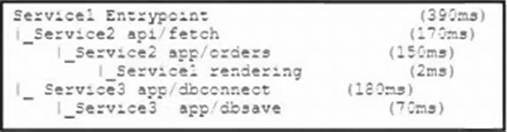
A microservices application is monitored by using distributed tracing. The tracing application output represents the parent-child relationships and the total time that it took to execute each task.
Which application task has the highest impact on the total transaction completion time?
- A . Service1 Entrypoint
- B . Service3 app/dbconnect
- C . Service2 app/orders
- D . Service2 api/fetch
A developer has updated an application to fix a bug with the ID abcd12a123b2c3456. The updated application has been installed on a Cisco Catalyst 9300 series switch.
Which command will enable the application called titan03?
- A . app-hosting activate appid titan03
- B . app-hosting start appid titan03
- C . app-hosting run re-start appid titan03 upfx
- D . app-hosting install appid titan03 package usbflash:titan03.tar
Refer to the exhibit.
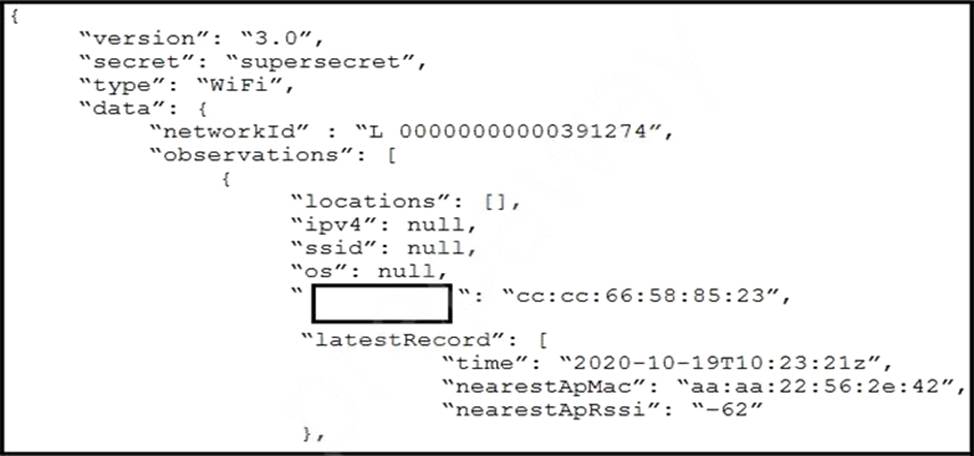
The JSON response is received from the Meraki location API.
Which parameter is missing?
- A . apMac
- B . clientMac
- C . clientId
- D . accesspoint
DRAG DROP
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to execute a REST API call to query all the NTP policy names and print the name of each policy. Not all options are used.
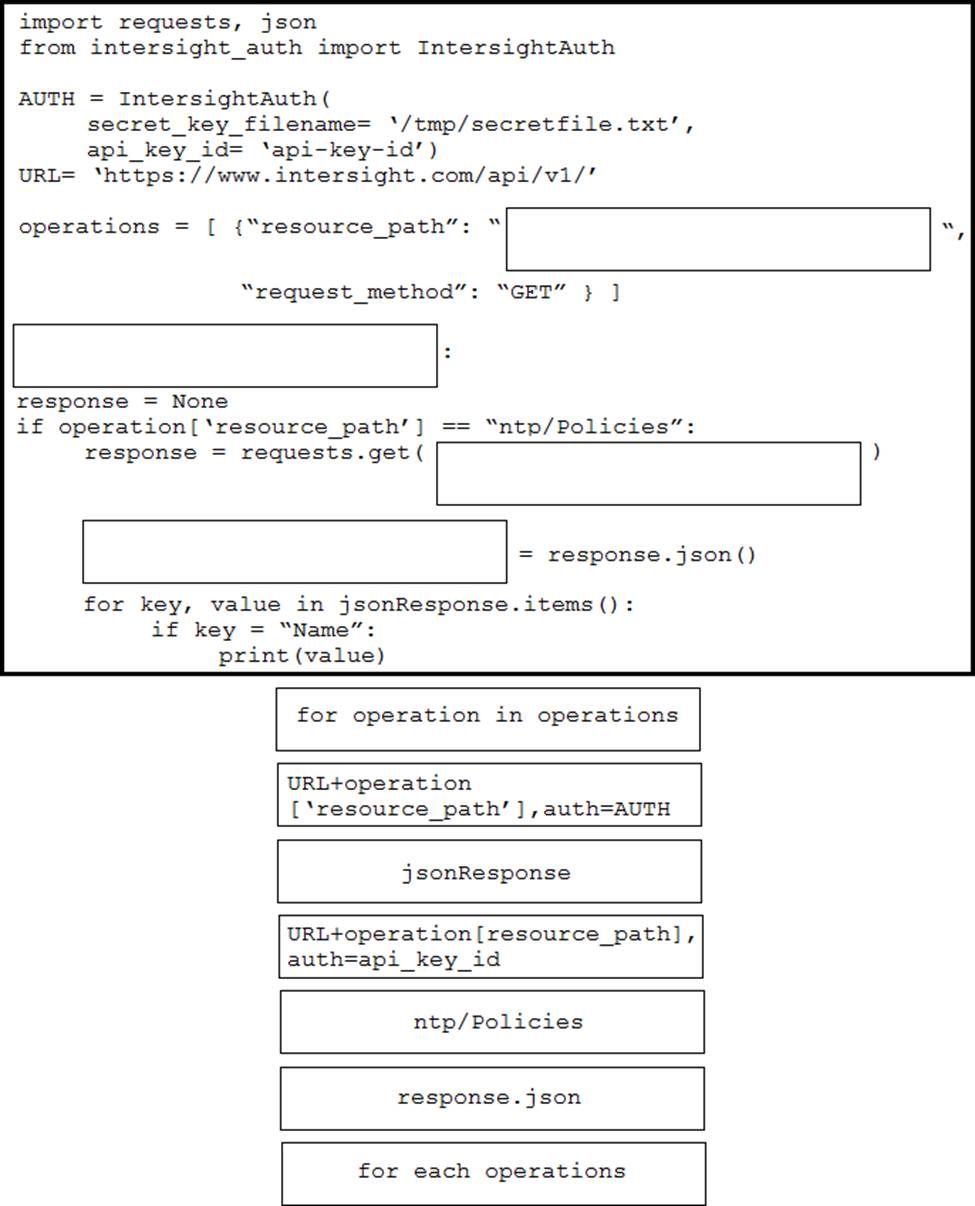
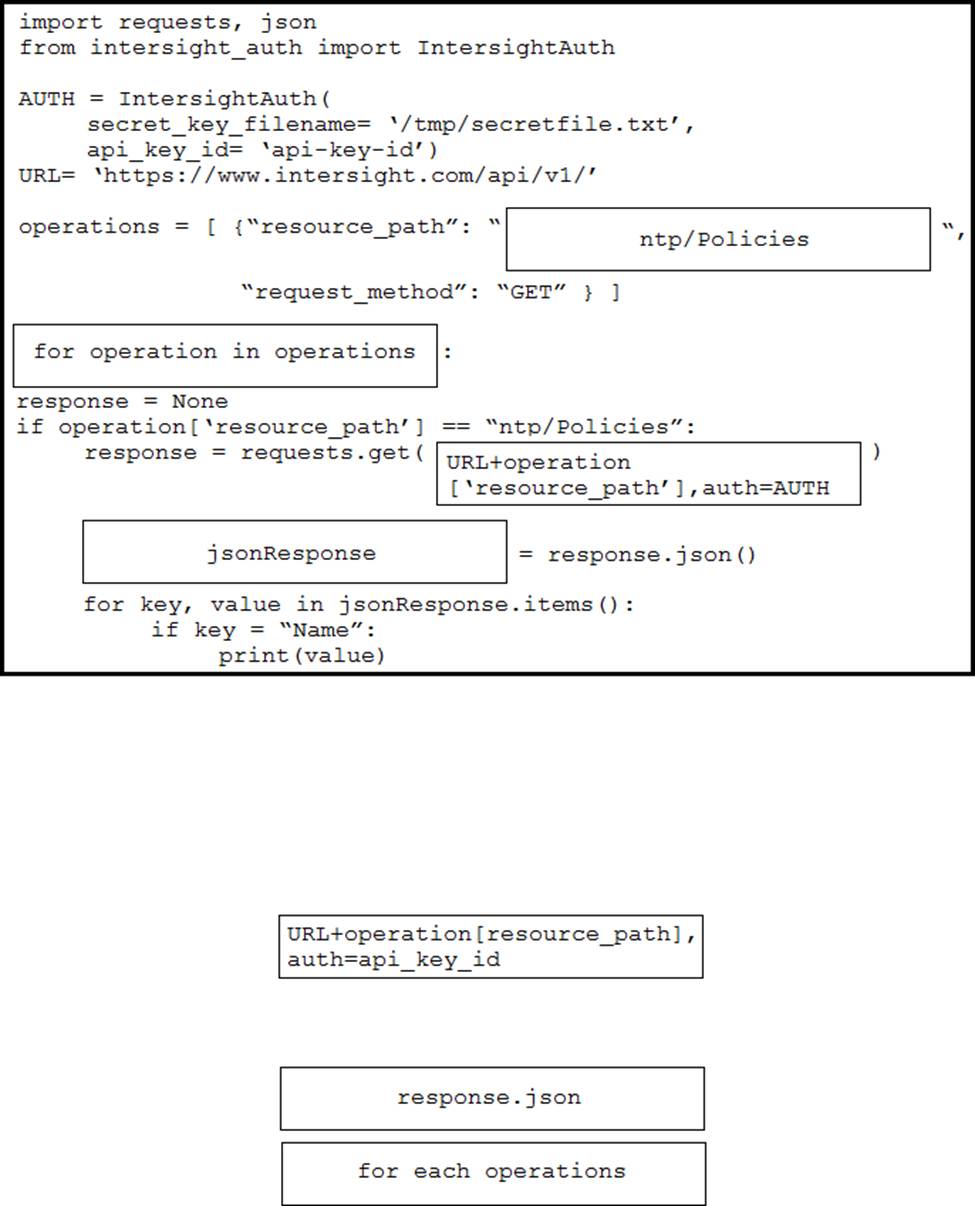
Which action enhances end-user privacy when an application is built that collects and processes the location data from devices?
- A . Use the network device serial number to encrypt the MAC address for each device.
- B . Salt the MAC address for each device.
- C . Implement an algorithmic information theoretic loss to the MAC address for each device.
- D . Pepper the MAC address for each device.
Which scenario is an example of the pseudonymization of sensitive data that meets GDPR requirements?
- A . implementing X-Forwarded-For at the frontend of a web app to enable the source IP addresses of headers to change
- B . separating the sensitive data into its own dedicated, secured data store and using tokens in its place.
- C . encrypting sensitive data at rest by using native cloud services and data in transit by using SSL/TLS transport.
- D . leveraging an application load balancer at the frontend of a web app for SSL/TLS decryption to inspect data in transit.
A developer is developing a microservices code to manage REST API errors.
Which two approaches must the developer take to manage the HTTP 429 "Too Many Requests" status code in the microservices code? (Choose two.)
- A . Implement subsequent retry with the same interval window.
- B . Resend the request immediately without implementing a wait time.
- C . Consecutive retries should truncate exponential backup.
- D . Throw an exception in the application code.
- E . Return errors in the response code.
What are two principles according to the build, release, run principle of the twelve-factor app methodology? (Choose two.)
- A . Code changes are able to be made at runtime.
- B . Separation between the build, release, and run phases.
- C . Releases should have a unique identifier.
- D . Existing releases are able to be mutated after creation.
- E . Release stage is responsible for compilation of assets and binaries.
Applications sometimes store configuration as constants in the code, which is a violation of the strict separation of configuration from code.
Where should application configuration be stored?
- A . environment variables
- B . YAML files
- C . Python libraries
- D . Dockerfiles
- E . INI files
