Practice Free 350-501 Exam Online Questions
Refer to the exhibit:
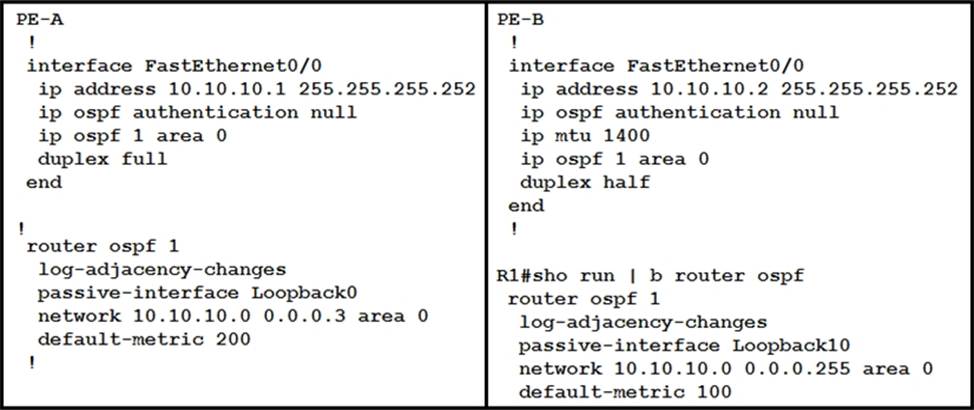
Which configuration prevents the OSPF neighbor from establishing?
- A . mtu
- B . duplex
- C . network statement
- D . default-metric
A
Explanation:
The OSPF neighbor relationship is not establishing due to a mismatch in MTU (Maximum Transmission Unit) settings on the interfaces of PE-A and PE-B routers. On PE-A, there is no MTU configuration under the interface FastEthernet0/0, which means it is using the default MTU setting. However, on PE-B, the MTU is explicitly set to 1400 bytes with “ip mtu 1400” command under interface FastEthernet0/0. OSPF requires that both ends of a point-to-point link have matching MTU sizes to form a neighbor relationship; otherwise, OSPF adjacency will not be established.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR) – Cisco SPCOR Resources
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services.
For which reason do you make this decision?
- A . It enables you to choose whether to separate or centralize each individual service.
- B . It is easier to manage a system in which services are mixed
- C . It requires only one edge router
- D . It enables EGP and IGP to operate independently
D
Explanation:
The full separation model for Internet access and MPLS L3VPN services is chosen to enable EGP (Exterior Gateway Protocol) and IGP (Interior Gateway Protocol) to operate independently. In this model, the internet access and MPLS L3VPN services are fully separated, ensuring that the two networks do not interfere with each other’s operation. This separation enhances network security, performance, and manageability.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies source documents or study guide
Refer to the exhibit:
![]()
What is the URL used for with REST API?
- A . It is used to contact a URL filter to determine the efficacy of a web address
- B . It is used to send a TACACS+ authentication request to a server
- C . It is used to send a message to the APIC to perform an operation on a managed object or class operator
- D . It is used to initiate an FTP session to save a running configuration of a device.
C
Explanation:
The URL in the exhibit is used with REST API to send a message to the APIC (Application Policy Infrastructure Controller) to perform an operation on a managed object or class operator. In Cisco’s ACI (Application Centric Infrastructure), REST API requests are used for managing, configuring, and retrieving data from the APIC. The URL structure typically includes the IP address of the APIC and specific paths that refer to objects or classes within the ACI fabric.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies source documents or study guide
What causes multicast traffic to permanently stay on the shared tree and not switch to the source tree?
- A . The SPT threshold is set to infinity.
- B . The RP IP address is configured incorrectly.
- C . The RP announcements are being filtered.
- D . SSM range is being used.
A
Explanation:
The SPT threshold set to infinity causes multicast traffic to permanently stay on the shared tree and not switch to the source tree. In multicast routing, the Shortest Path Tree (SPT) threshold determines when a router should switch from receiving multicast traffic on the shared tree to receiving it on a source tree. Setting the SPT threshold to infinity means that the router will always receive multicast traffic on the shared tree
Refer to the exhibit.
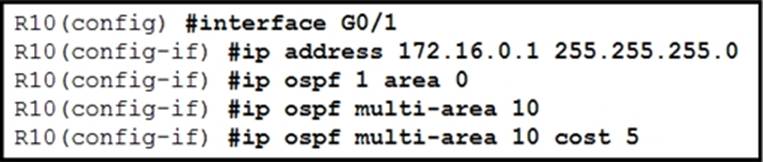
A network engineer Is implementing OSPF multiarea.
Which command on interface G0/1 resolves adjacency Issues in the new area?
- A . Ip ospf network broadcast
- B . Ip ospf network non-broadcast
- C . Ip ospf network polnt-to-multlpoint
- D . Ip ospf network point-to-point
D
Explanation:
In the context of OSPF multiarea implementation, adjacency issues can arise due to network type mismatches or area boundary discrepancies. The command “ip ospf network point-to-point” is used on interface G0/1 to specify the OSPF network type as point-to-point. This configuration facilitates OSPF neighbor establishment over a direct connection between two routers, eliminating the need for a designated router (DR) or backup designated router (BDR), and resolving adjacency issues in the new area.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies source documents or study guide
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_ospf/configuration/xe-16/iro-xe-16-book/iro-multi-area-adj-xe.html
A network operator needs to implement PIM-SSM multicast configuration on customer’s network so that users in different domains are able to access and stream live traffic.
Which two actions must the engineer perform on the network to make the streaming work? (Choose two.)
- A . Configure at least one MSDP peer on the network
- B . Enable IGMP version 2 at the interface lever.
- C . Enable PIM sparse mode on the device.
- D . Enable IGMP version 3 at the interface level.
- E . Enable PM dense mode on the device.
C, D
Explanation:
Remember that SSM is an extension of IP multicast where datagram traffic is forwarded only from explicitly joined multicast sources to receivers. It creates source-specific multicast distribution trees without shared trees.
Reference: Cisco PIM-SSM Configuration Example
Cisco IP Multicast: PIM Configuration Guide
Refer to the exhibit.
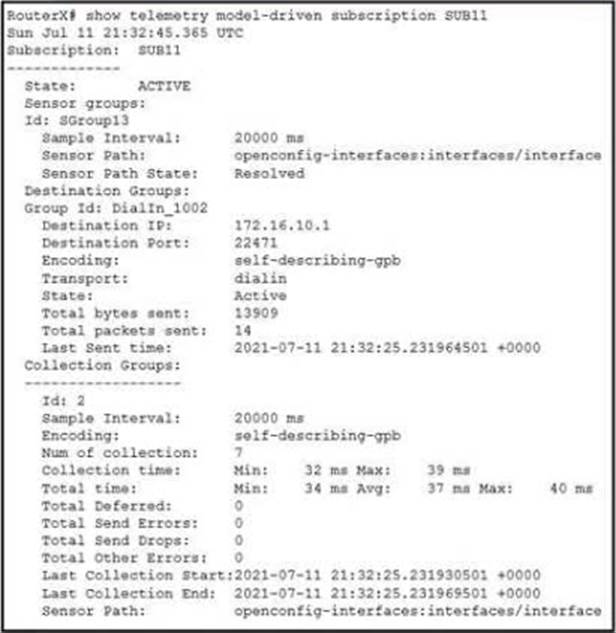
An engineer ran this show telemetry command to view subscription SUB11 on RouterX. The engineer then decided that RouterY should provide the same output lor sensor group SGroup13 as RouterX. The engineer cannot access RouterX to copy its configuration No access lists on the router block user access.
Which configuration must the engineer apply on RouterY to provide the same output from the show telemetry command?
- A . RouterY(config)# telemetry model-driven
RouterY(config-model-driven)# subscription SUB11
RouterY(config-model-driven-subs)# sensor-group-id SGroup13 sample-interval 20000
RouterY(config-model-driven-subs)# destination-id DGroup1 - B . RouterY(config)# telemetry model-driven
RouterY(config-model-driven)# subscription SGroup13
RouterY(config-model-driven-subs)# sensor-group-id SGroup13 sample-interval 20000 - C . RouterY(config)# telemetry model-driven
RouterY(config-model-driven)# destination-group SUB11
RouterY(config-model-driven-dest)# address family ipv4 172.16.10.1 port 22471
RouterY(config-model-driven-dest-addr)# encoding self-describing-gpb
RouterY(config-model-driven-dest-addr)# protocol tcp - D . RouterY(config)# telemetry model-driven
RouterY(config-model-driven)# sensor-group SGroup13
RouterY(config-model-driven-snsr-grp)# sensor-path opencong-interfaces:interfaces/interface
Which action occurs during the traceback phase of the six-phase approach to service provider security?
- A . Trace action occur flows from the stacked sections of the network toward the network edges
- B . Detect unusual activity or behavior and activate appropriate measures after an alert is raised.
- C . Review the whole attack-handling process
- D . Mitigate the attack that flows using various mechanisms.
A
Explanation:
During the traceback phase of the six-phase approach to service provider security, the action that occurs is tracing the attack flows from the attacked sections of the network toward the network edges. This phase entails identifying the source of the attack by analyzing the path that the attack traffic has taken through the network.
Refer to the exhibit.
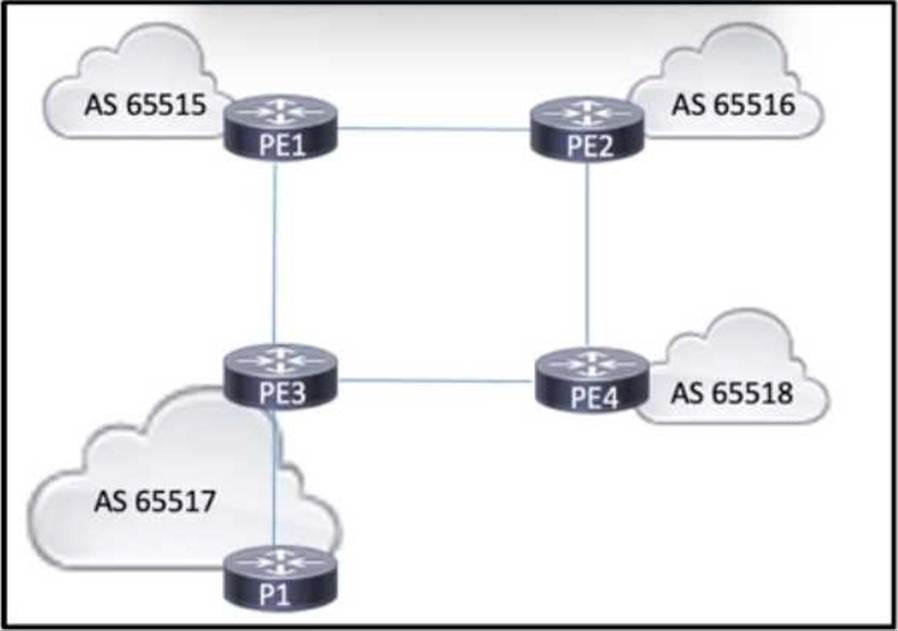
AS 65517 is running OSPF within the core. BGP is running between all four autonomous systems, interconnecting several ISPs that provide intranet and extranet services. All of the PE routers are connected, and eBGP peering relationships have been established. A network engineer also configured an iBGP peering between PE3 and P1, and the peering is up. However, P1 cannot reach routes outside of AS 65517.
Which action must the engineer take so that P1 reaches external routes?)
- A . Synchronize BGP and OSPF with AS 65517.
- B . Add the next-hop-self attribute under the BGP neighbor configuration for P1 on PE3.
- C . Install route targets on all PE routers under the VRF configuration for intranet services.
The networking team must create a golden configuration to monitor and discover network devices, and also support the capability to configure network devices in the future. Not all devices on the network are capable of gRPC or REST-API calls. The solution should use a username and password, and data in transit should be highly secured. The modern NMS system has been configured with IP address 172.14.15.1, and the snmp-server view iso included command has already been added to the template.
Which two commands should the team add to the configuration template to enable SNMPv3 on network devices? (Choose two.)
- A . snmp-server user Cisco group v3 auth md5 Cisco123 authpriv aes 192 Cisco1234
- B . snmp-server group v3 authnopriv ro
- C . snmp-server user Cisco group v3 auth sha Cisco123 priv aes 256 Cisco1234
- D . snmp-server user Cisco group v3 auth she-aes Cisco123 authnopriv aes 128 Cisco1234
- E . snmp-server group v3 priv read view
