Practice Free 350-501 Exam Online Questions
Refer to the exhibit.
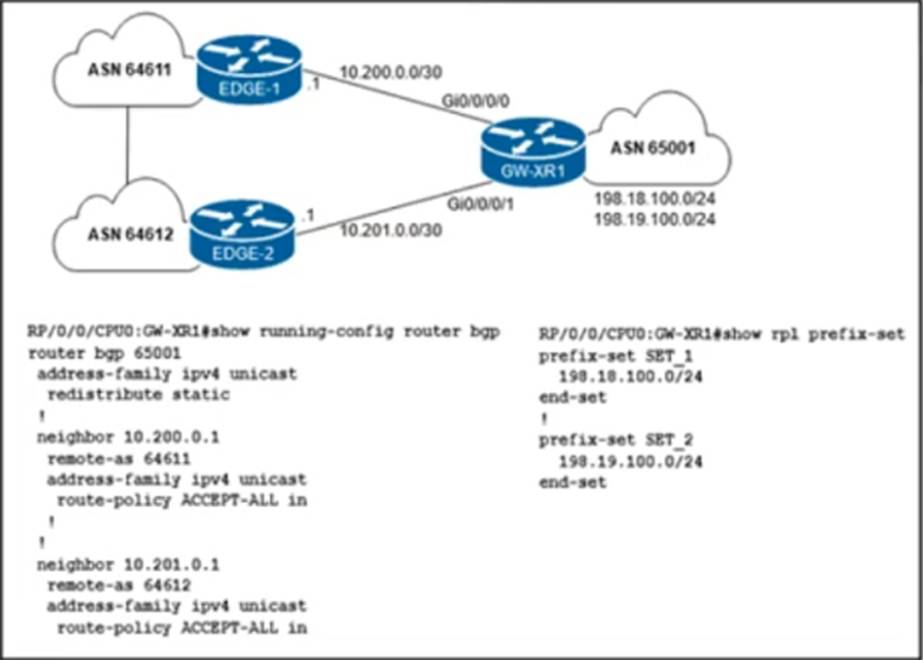
The network engineer who manages ASN 65001 must configure a BGP routing policy on GW-XR1 with these requirements:
• Advertise locally-originated routes and /24 prefixes assigned within the 198.18.0.0/15 range. All other prefixes must be dropped.
• Reachability to 198.18.100.0/24 must be preferred via the EDGE-1 connection.
• Reachability to 198.19.100.0/24 must be preferred via the EDGE-2 connection.
Which configuration must the network engineer implement on GW-XR1?
A)

B)
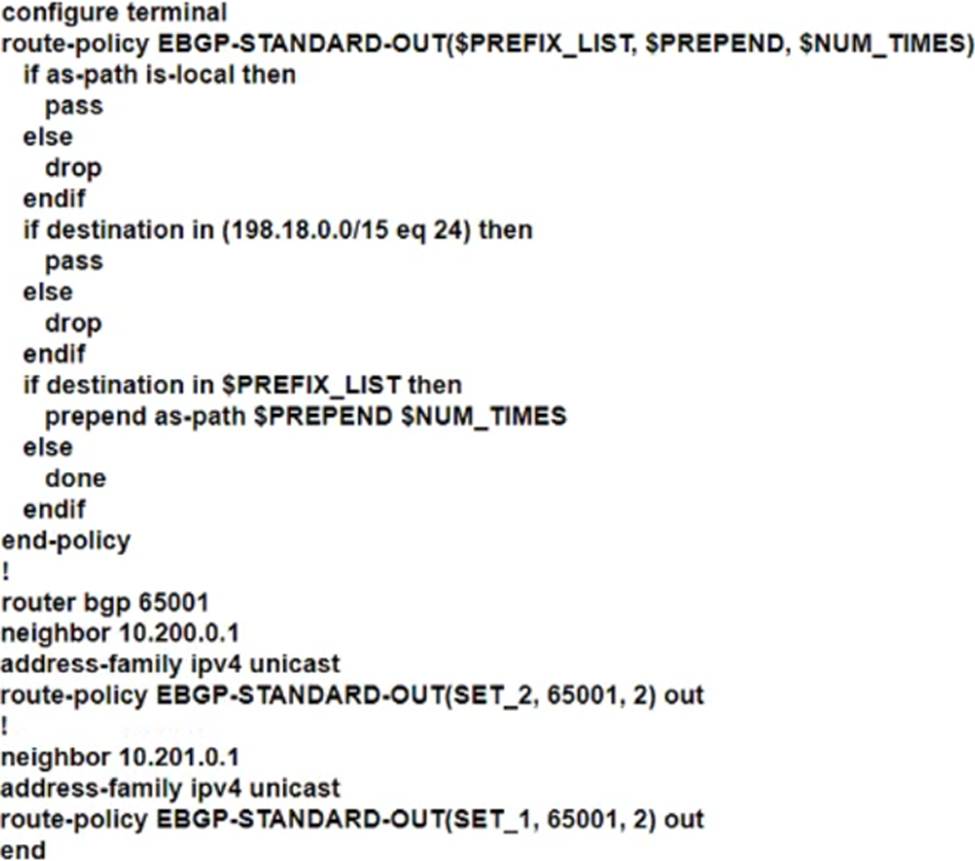
C)
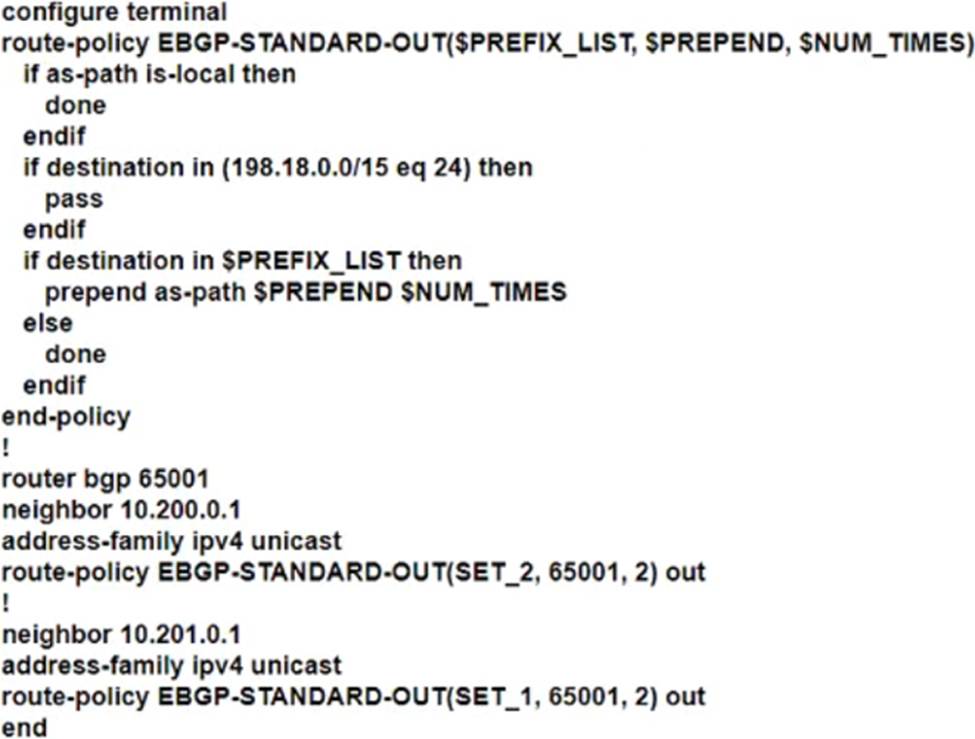
D)

- A . Option A
- B . Option B
- C . Option C
- D . Option D
B
Explanation:
https://community.cisco.com/t5/mpls/cisco-xr-rpl-destination-vs-destination-prefix/td-p/4587693
Refer to the exhibit.

An engineer is configuring path selection on router R1 for two ASNs as shown.
Which additional task must the engineer perform on Router 1 so that all outbound traffic utilizes the link between R1 and R3 to reach ASN 4567?
- A . Configure a low weigh! on the peer to ASN 4567.
- B . Configure a high weight on the peer to ASN 4567.
- C . Configure an AS path prepend on the peer to ASN 4567.
- D . Configure a high med on the peer to ASN 4567.
B
Explanation:
: In Cisco’s path selection process, the weight attribute is the first criterion for selecting a path. It is a Cisco-specific
parameter, local to the router, and it is not propagated in routing updates. The path with the highest weight is preferred. Therefore, configuring a high weight on the peer to ASN 4567 will make Router R1 prefer this path for all outbound traffic directed towards ASN 4567.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR) – Cisco SPCOR Training & Certification
What are two characteristics of MPLS TE turrets? (Choose two)
- A . They require EIGRP to be running in the core.
- B . They use RSVP to provide bandwidth for the tunnel.
- C . They are run over Ethernet cores only.
- D . The headend and tailend routes of the tunnel must have a BGP relationship
- E . They are unidirectional
B, E
Explanation:
MPLS TE tunnels are designed to optimize the flow of network traffic by mapping it onto specific paths based on resource requirements. Two key characteristics of MPLS TE tunnels are:
RSVP for Bandwidth Reservation: MPLS TE tunnels use the Resource Reservation Protocol (RSVP) to reserve the necessary bandwidth for the tunnel, ensuring that the required resources are available for the data that will flow through it12.
Unidirectional Flow: These tunnels are unidirectional, meaning they are established from a source to a destination and do not inherently support traffic in the reverse direction. This is because each MPLS TE tunnel is associated with a label-switched path (LSP) that is specifically set up for traffic flowing in one direction
A service provider is in the process of implementing Unified MPLS on an enterprise network with many nodes. After the migration, several new customers will be added to the environment. RFC 3107 is used to build BGP LSPs across the domains.
Which action must the networking team take to reduce the full-mesh requirement for IBGP?
- A . Implement route reflectors on all ABRs.
- B . Implement a confederation with the network segmented according to business units.
- C . Implement route reflectors on all P routers.
- D . Implement a confederation with each ABR serving as a gateway between secondary AS numbers.
Refer to the exhibit.
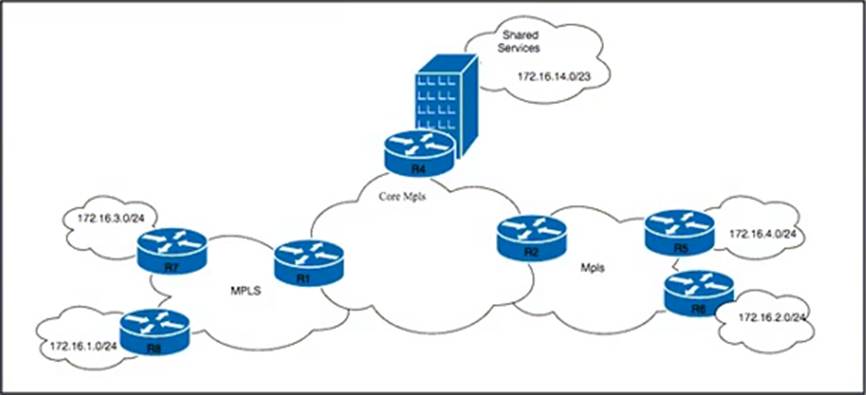
The ISP is implementing a new hosting-as-a-service solution for its business customers. Service accessibility must be unique and separate for each customer. The network architect must ensure that multiple paths toward the hosting-as-a-service solution are always available. Basic protection against traffic black-holing on the MPLS network is required in case of link failure.
Which two actions must the engineering team perform to meet the requirements? (Choose two.)
- A . Create the hosting-as-a-service VRF on router R4 and configure It with the route target both 65123:88 command.
- B . Configure the fast-reroute per-prefix command for the IS-IS protocol in the MPLS network and enable the BGP route-reflector feature on R2.
- C . Enable the VRF-Lite feature on router R4 and enable BGP address-family VPNv4.
- D . Configure the mpls Idp sync command in the MPLS network with the BGP additional-paths receive and additional-paths send options.
- E . Configure the fast-hello command under the IS-IS routing protocol with the BGP multipath 2 option enabled.
B, D
Explanation:
To ensure multiple paths toward the hosting-as-a-service solution and basic protection against traffic black-holing in case of link failure, the engineering team should:
B. Configure the fast-reroute per-prefix command for the IS-IS protocol in the MPLS network. This action enables fast reroute, which is a mechanism to quickly switch over to a backup path in case the primary path fails, without waiting for the routing protocol to converge.
D. Configure the mpls ldp sync command in the MPLS network with the BGP additional-paths receive and additional-paths send options. MPLS LDP (Label Distribution Protocol) synchronization ensures that a label-switched path (LSP) is not used for forwarding traffic until all routers along the path have signaled that they have label information for that LSP. The BGP additional-paths feature allows for the advertisement of multiple paths for the same prefix, providing path diversity and redundancy.
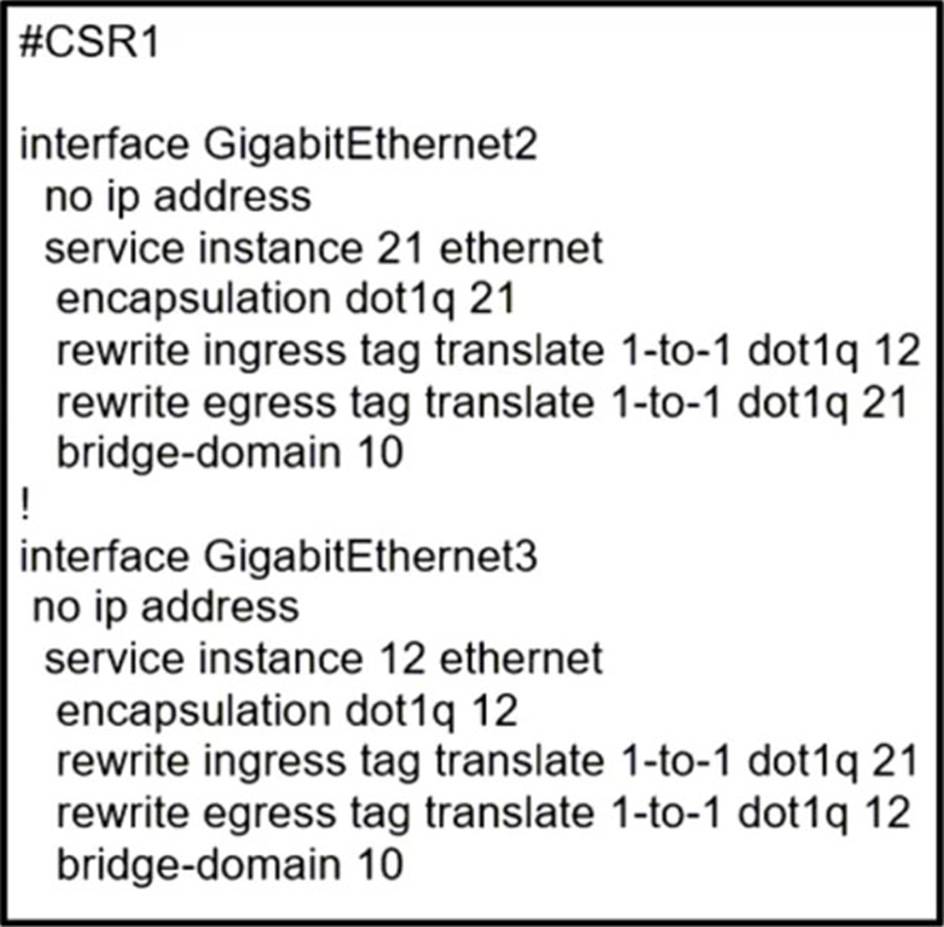
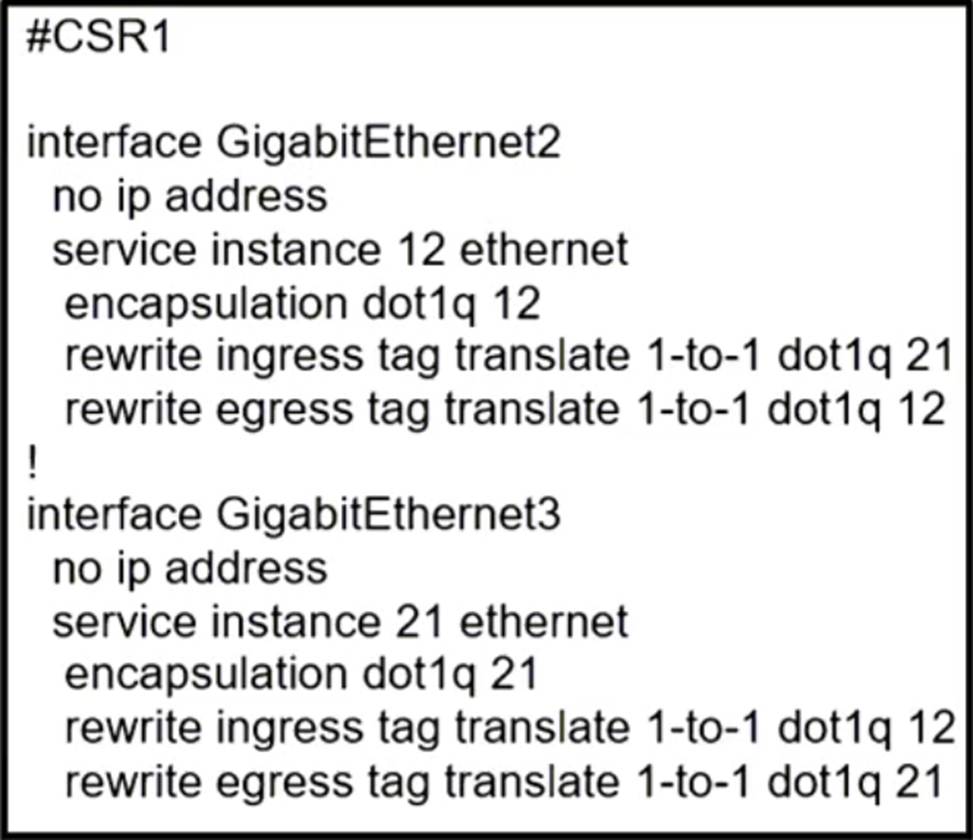
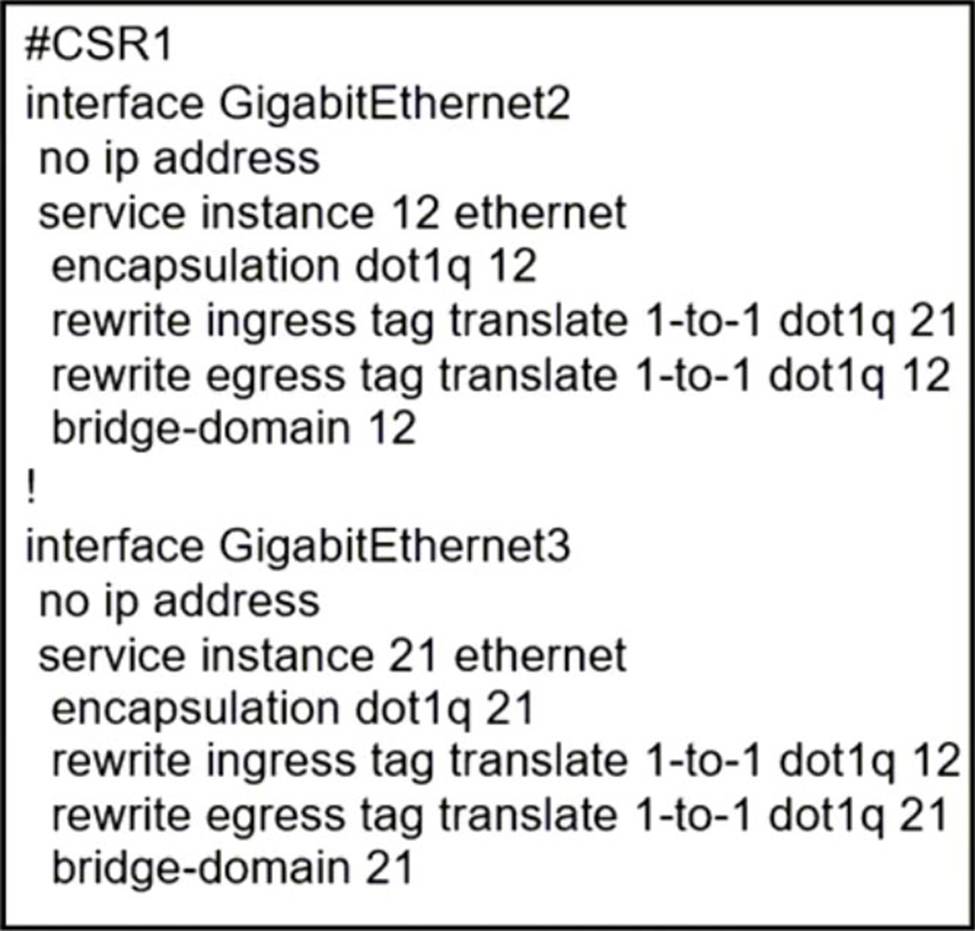
Refer to the exhibit.
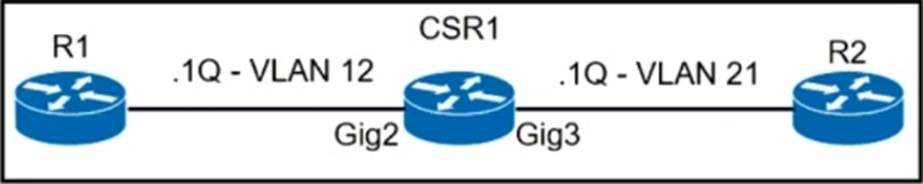
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively.
Which configurator accomplishes this task?
A)
B)
C)
D)

- A . Option A
- B . Option B
- C . Option C
- D . Option D
C
Explanation:
The configuration in Option C correctly sets up the interfaces for VLAN tag translation. On interface GigabitEthernet2, the command rewrite ingress tag translate 1-to-1 dot1q 21 changes the incoming VLAN tag from 12 to 21. Conversely, on interface GigabitEthernet3, the command rewrite egress tag translate 1-to-1 dot1q 12 changes the outgoing VLAN tag from 21 to 12. This setup ensures that traffic flowing from R1 to R2 and vice versa has the correct VLAN tags as required.
Reference: This explanation is based on the concepts outlined in the Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR v1.0) course
Refer to the exhibit.

Which show command should be implemented to display per-interface statistics about uRPF drops and suppressed drops?
- A . show ip traffic
- B . showip interface
- C . show cef interface
- D . show ip interface brief
C
Explanation:
The “show cef interface” command is used to display per-interface statistics about Unicast Reverse Path Forwarding (uRPF) drops and suppressed drops. uRPF is a feature that helps to mitigate problems caused by IP address spoofing, and the “show cef interface” command provides detailed information on the interfaces where uRPF is applied, including drop statistics.
