Practice Free 350-501 Exam Online Questions
Refer to the exhibit.
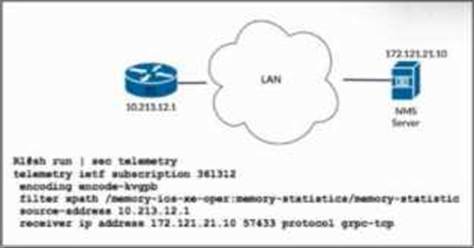
The network administrator is configuring memory telemetry on router R1. Only kvGPB encoding and gRPC protocol based on RFC 7540 should be used. Updates should be sent every two seconds.
Which two commands must the administrator apply to complete the task? (Choose two.)
- A . stream native
- B . stream yang-notif-native
- C . update-policy periodic 200
- D . update-policy periodic 2
- E . stream yang-push
Refer to the exhibit.

A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?
- A . Implement targeted LDP sessions between directly connected routers and between routers that are one hop away.
- B . Implement LDP session protection between each directly connected LDP neighbor.
- C . Implement LDP sync between routers that are directly connected to each business division.
- D . Implement targeted LDP sessions between routers that are directly connected to each business division.
Which fact must a network engineer consider when planning to deploy RSVP-TE FRR?
- A . The FRR backup tunnel reserves the total bandwidth of all protected tunnels
- B . FRR protects MPLS LDP and RSVP-TE LSPs.
- C . PLR prefers FRR NHOP backup tunnels over NNHOP tunnels.
- D . PLR prefers FRR NNHOP backup tunnels over NHOP tunnels.
C
Explanation:
RSVP-TE Fast Reroute (FRR) is a mechanism that provides protection switching for MPLS TE LSPs. The Point of Local Repair (PLR) will prefer to use a next-hop (NHOP) backup tunnel over a next-next-hop (NNHOP) backup tunnel when both are available. This preference is due to the fact that NHOP backup tunnels can provide faster rerouting around the failure point, minimizing traffic disruption and packet loss.
Reference: The information is based on the RSVP-TE FRR deployment considerations from the Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR) course materials.
Refer to the exhibit:

A network engineer is implementing QoS services.
Which two statements about the QoS-group keyword on Cisco IOS XR 3re true? (Choose two )
- A . The QoS group numbering corresponds to priority level
- B . QoS group marking occurs on the ingress
- C . It marks packets for end to end QoS pokey enforcement across the network
- D . QoS group can be used in fabric QoS policy as a match criteria
- E . It cannot be used with priority traffic class
B, D
Explanation:
The QoS-group keyword on Cisco IOS XR is used for marking packets on the ingress of the device. This allows for internal handling and is not transmitted across the network. It can be used in fabric QoS policy as a match criteria to apply specific policies based on the QoS group marking.
Reference: = Implementing and Operating Cisco Service Provider Network Core Technologies course materials.
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network.
Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
- A . Carriage of full internet routes in a VPN, in the case of internet access VPNS
- B . Internet routing through global routing on a PE router.
- C . Internet access routing as another VPN in the ISP network.
- D . Internet access through leaking of internet routed from the global table into the L3VPN VRF
- E . Internet access for global routing via a separate interface in a VRF
B, D
Explanation:
Option B: Internet routing through global routing on a PE router means that the PE router performs global routing for internet traffic. This allows the PE router to handle both L3VPN traffic and internet traffic.
Option D: Leaking internet routes from the global table into the L3VPN VRF allows the L3VPN customers to access the internet via the same MPLS backbone. The PE router imports internet routes into the L3VPN VRF, enabling internet access for VPN customers.
Refer to the exhibit:
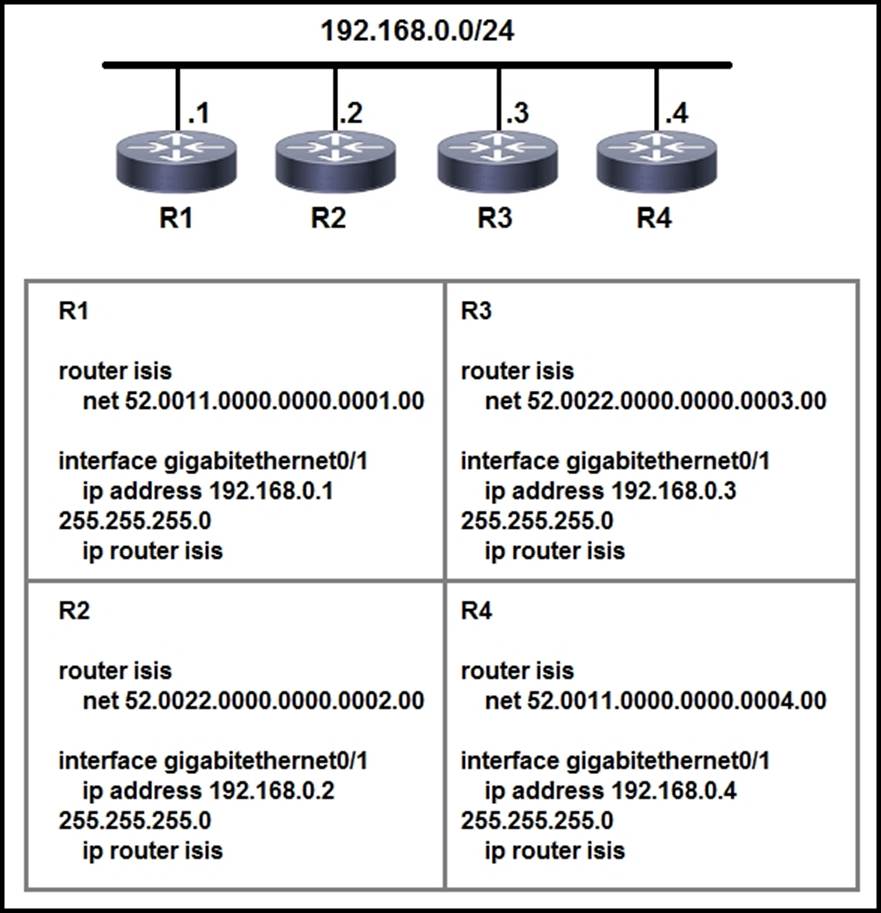
Which two statements about the ISIS topology are true? (Choose two.)
- A . All four routers are operating as Level 1 routers only.
- B . All four routers are operating as Level 2 routers only.
- C . All four routers are operating as Level 1-2 routers.
- D . R1 and R2 are Level 2 neighbors.
- E . R1 and R4 are Level 2 neighbors
C, D
Explanation:
The ISIS topology exhibit indicates that all four routers are configured as Level 1-2 routers, which means they can operate in both Level 1 and Level 2 IS-IS areas. This is evident from the net addresses that show a mix of area addresses, allowing for intra-area (Level 1) and inter-area (Level 2) routing. Additionally, R1 and R2 are Level 2 neighbors because they have different area addresses, allowing them to form Level 2 adjacencies and route between different areas.
Reference: = Implementing and Operating Cisco Service Provider Network Core Technologies course materials.
Refer to the exhibit.
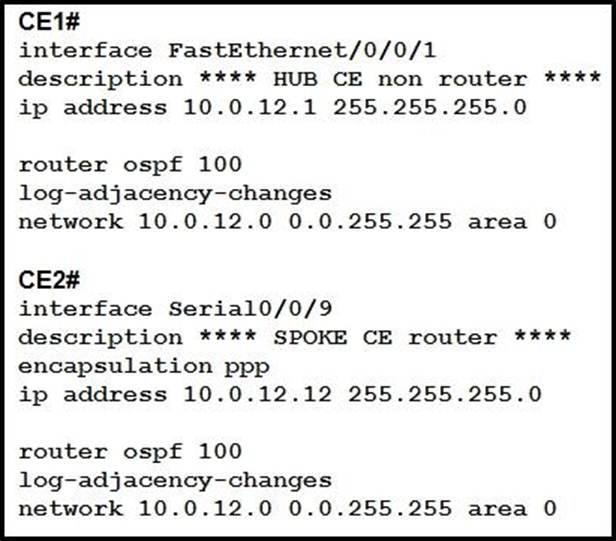
A network engineer is configuring customer edge routers to finalize a L2VPN over MPLS deployment Assume that the AToM L2VPN service that connects the two CEs is configured correctly on the service provider network.
Which action causes the solution to fail?
- A . A loopback with a /32 IP address has not been used
- B . OSPF does not work with L2VPN services
- C . The xconnect statement has not been defined
- D . The routing protocol network types are not compatible
C
Explanation:
In the context of configuring L2VPN over MPLS, the xconnect statement is essential. It specifies the peer router and virtual circuit ID, creating the connection between two customer edge routers over the service provider’s MPLS network. Without the xconnect statement, there’s no association between the attachment circuits and pseudowire, leading to the failure of the L2VPN service.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR) – Cisco SPCOR Training & Certification
Which function does RSVP perform in a Cisco MPLS TE environment?
- A . It establishes targeted LDP sessions between neighbors that are directly connected.
- B . It signals to LDP protocol along the path that a Cisco MPLS TE will be configured.
- C . It reserves bandwidth for LDP sessions between routers participating in a Cisco MPLS TE.
- D . It reserves the bandwidth along the path between the head-end and tail-end router.
A network team has failed to implement IS-IS Mult topology.
What is the reason for it?
- A . The router did not support VRFs.
- B . The routing process did not support extended metrics.
- C . The router did not have Cisco Discovery Protocol and Cisco Express Forwarding disabled.
- D . The routing process supported Level 1 only.
B
Explanation:
The failure to implement IS-IS Mult topology can be attributed to the routing process not supporting extended metrics. Extended metrics are necessary for Mult topology routing because they allow for the definition of multiple topologies within the same routing protocol, each with its own set of metrics and paths1.
Reference: Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR) source documents or study guide
A regional company is planning to bolster the security of their LAN infrastructure by implementing advanced encryption techniques between their core switch and their distribution switch. The solution must leverage hardware-accelerated encryption capabilities to transparently encrypt all traffic between the two switches at the data-link layer to safeguard against unauthorized access. However, it is important for the solution to have minimal impact on network performance and latency.
Which action must the engineer take to meet the requirements?
- A . Deploy an IPsec tunnel with MD5 hashing between the two switches.
- B . Enable SSL VPN with SHA-256 encryption on all interfaces on both switches.
- C . Enable L2TP with RSA encryption on both switches.
- D . Implement MACsec with AES-256 encryption on both switches.
