Practice Free 350-401 Exam Online Questions
What is one characteristic of Cisco SD-Access networks?
- A . Devices are assigned to virtual networks based on their VLAN membership.
- B . Scalable group tags are used for macrosegmentatlon.
- C . Virtual networks are used for microsegmentation.
- D . All traffic is Layer 3 within the fabric.
In which forms can Cisco Catalyst SD-WAN routers be deployed at the perimeter of a site to provide SD-WAN services?
- A . virtualized instances
- B . hardware, software, cloud, and virtualized instances
- C . hardware, virtualized. and cloud instances
- D . hardware and virtualized instances
Which function is performed by vSmart in the Cisco Catalyst SD-WAN architecture?
- A . facilitation of NAT detection and traversal
- B . redistribution between OMP and other routing protocols
- C . distribution of IPsec keys
- D . execution of localized policies
An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication.
Which profile must the engineer edit to achieve this requirement?
- A . RF
- B . WLAN
- C . Policy
- D . Flex
What are two characteristics of a directional antenna? (Choose two.)
- A . high gain
- B . receive signals equally from all directions
- C . commonly used to cover large areas
- D . provides the most focused and narrow beam width
- E . low gain
Refer to the exhibit.
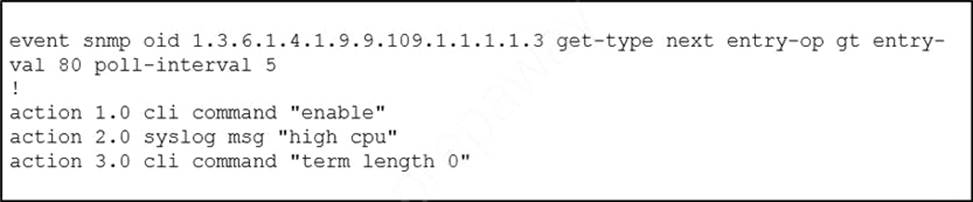
An engineer must create a script that appends the output of the show process cpu sorted command to a file.
- A . action 4.0 syslog command "show process cpu sorted | append flash:high-cpu-file"
- B . action 4.0 cli command "show process cpu sorted | append flash:high-cpu-file"
- C . action 4.0 ens-event "show process cpu sorted | append flash:high-cpu-file"
- D . action 4.0 publish-event "show process cpu sorted | append flash:high-cpu-file"
Which technology collects location information through data packets received by the APs instead of using mobile device probes?
- A . detect and locate
- B . FastLocate
- C . hyperlocation
- D . RF fingerprinting
Which AP mode analyzes the spectrum to detect sources of interference?
- A . Monitor
- B . Rogue detector
- C . SE-Connect
- D . Sniffer
Which device makes the decision for a wireless client to roam?
- A . wireless client
- B . Wireless LAN controller
- C . access point
- D . WCS location server
What occurs during a Layer 2 inter-controller roam?
- A . A new security context is applied for each controller to which the client is associated, but the IP address remains the same.
- B . The client must be associated to a new controller where a new IP address and security context are applied.
- C . The client retains the same IP address and security context.
- D . The client is marked as foreign in the database of each new controller to which it is connected.
