Practice Free 300-740 Exam Online Questions
The main goal of implementing secure domains within the SAFE framework is to:
- A . Increase operational efficiency
- B . Enhance the flexibility of network configurations
- C . Improve security by creating defined areas of trust
- D . Simplify the user authentication process
Network protocol blocking, such as FTP and BitTorrent, is crucial for:
- A . Enhancing the performance of cloud applications
- B . Preventing data exfiltration and limiting malware spread
- C . Allowing unrestricted data transfer
- D . Simplifying network configuration
Direct-internet-access for trusted business applications is beneficial for:
- A . Reducing latency and improving access to cloud resources
- B . Increasing security risks by exposing applications to the internet
- C . Simplifying the network architecture
- D . Enhancing the user experience by providing quicker access
Cisco Secure Workload is used for:
- A . Increasing the workload on servers
- B . Enforcing security policies within application workloads
- C . Reducing application functionality
- D . Encrypting email communications
The main advantage of implementing user and device authentication via identity certificates is:
- A . The reduction in the need for physical security controls
- B . The elimination of passwords for all users
- C . The increase in the speed of network connections
- D . The provision of a secure method to verify identities
Response automation tools help in:
- A . Slowing down the detection of malware
- B . Quickly isolating infected devices from the network
- C . Increasing the number of false positives
- D . Complicating incident response procedures
The use of a reverse proxy in cloud security is important for:
- A . Only logging HTTP/HTTPS traffic
- B . Providing an additional layer of abstraction and control to ensure the security of backend servers
- C . Directly exposing application servers to the internet
- D . Simplifying the network by removing the need for firewalls
In the context of threat response, "reinstantiate" primarily means:
- A . Maintaining the compromised state for forensic analysis
- B . Permanently disabling compromised accounts
- C . Ignoring the incident after containment
- D . Restoring services or applications to their operational state after a security incident
A recent InfraGard news release indicates the need to establish a risk ranking for all on-premises and cloud services. The ACME Corporation already performs risk assessments for on-premises services and has applied a risk ranking to them. However, the cloud services that were used lack risk rankings.
What Cisco Umbrella function should be used to meet the requirement?
- A . Secure Internet Gateway
- B . Domain Name Server Filtering
- C . URL Categorization by Talos
- D . App Discovery
Refer to the exhibit.
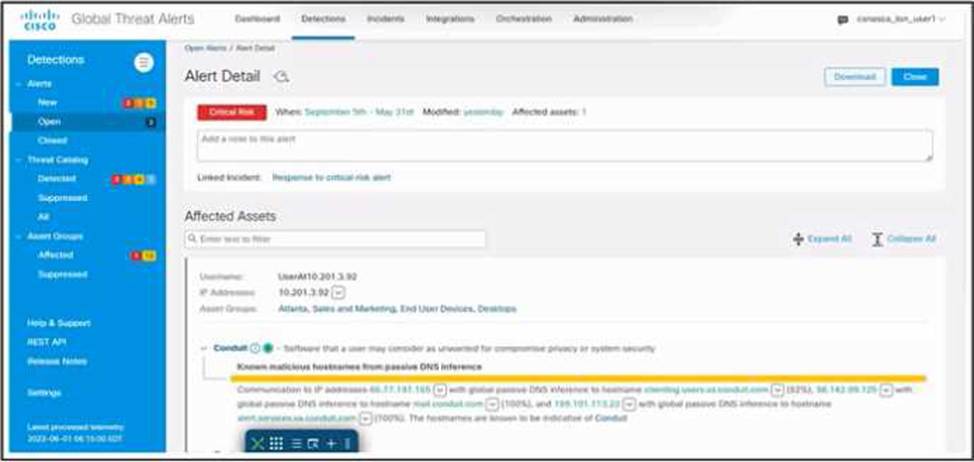
An engineer is investigating the critical alert received in Cisco Secure Network Analytics. The engineer confirms that the incident is valid.
Which two actions must be taken? (Choose two.)
- A . Inform the incident management team.
- B . Block IP address 66.77.197.165
- C . Uninstall the Conduit software.
- D . Shut down the host.
- E . Quarantine the host
