Practice Free 300-740 Exam Online Questions
To implement user and device trust in web applications, SAML authentication configures _________ for secure access.
- A . identity certificates
- B . SAML assertions
- C . password policies
- D . biometric data
Determine cloud platform security policies based on application connectivity requirements might involve:
- A . Selecting appropriate cloud service models (IaaS, PaaS, SaaS)
- B . Implementing network peering
- C . Configuring firewalls and access lists
- D . Avoiding the use of security groups and ACLs
OIDC (OpenID Connect) is primarily utilized for:
- A . Increasing network latency
- B . Authenticating users via an identity provider
- C . Disconnecting user sessions
- D . Monitoring user activities
Enforcing application policy at the network security edge is crucial for:
- A . Allowing all applications to bypass security checks
- B . Ensuring only authorized applications can access network resources
- C . Decreasing the overall security of the network
- D . Ignoring the security posture of accessing devices
Cisco Secure Cloud Insights aids in cloud security by:
- A . Offering visibility into cloud assets for improved governance and risk management
- B . Simplifying attack vectors for easier exploitation
- C . Focusing on non-cloud assets
- D . Decreasing the granularity of cloud asset monitoring
Refer to the exhibit.
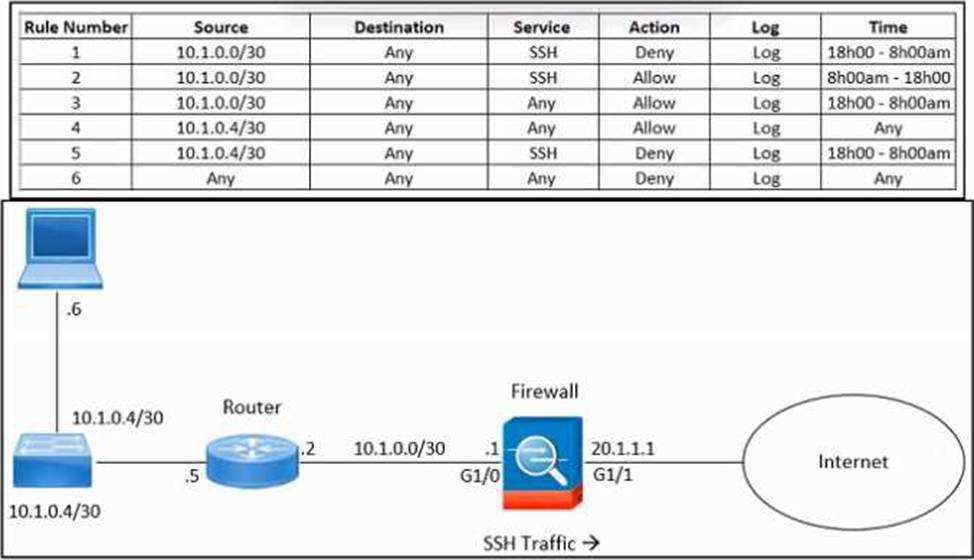
An engineer must troubleshoot an issue with excessive SSH traffic leaving the internal network between the hours of 18:00 and 08:00. The engineer applies a policy to the Cisco ASA firewall to block outbound SSH during the indicated hours; however, the issue persists.
What should be done to meet the requirement?
- A . Change the time of rule 2.
- B . Delete rule 4
- C . Delete rule 3
- D . Change the time of rule 5
Refer to the exhibit.
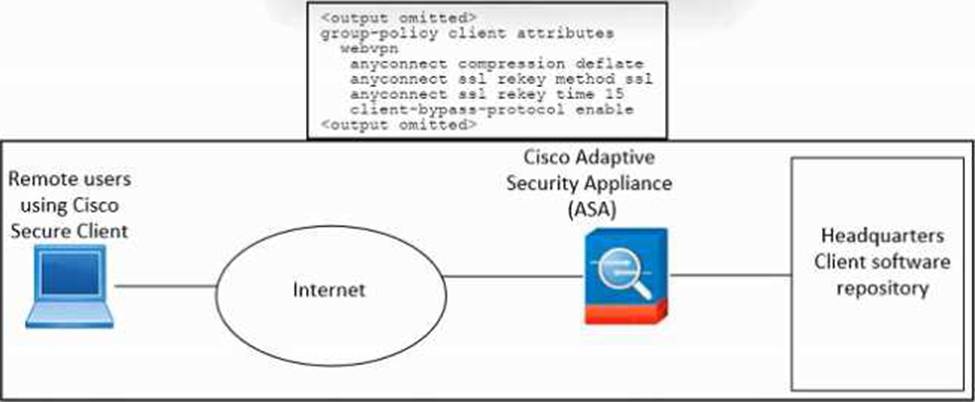
An engineer must configure Cisco ASA so that the Secure Client deployment is removed when the user laptop disconnects from the VPN. The indicated configuration was applied to the Cisco ASA firewall.
Which command must be run to meet the requirement?
- A . client-bypass-protocol enable
- B . anyconnect keep-installer none
- C . anyconnect firewall-rule client-interface
- D . client-bypass-protocol disable
The SAFE Key structure is designed to:
- A . Unlock encrypted data
- B . Guide the deployment of network devices
- C . Organize security measures within the network architecture
- D . Create a single sign-on experience for users
What does SAML/SSO stand for and what is its purpose?
- A . Single Access Markup Language / Single Sign-On, to simplify logins across different systems
- B . Security Assertion Markup Language / Single Sign-On, to simplify logins across different systems
- C . Secure Access Markup Language / Secure Sign-On, to increase login complexity
- D . Security Assertion Markup Language / Secure Sign-Out, to secure logouts across systems
Which attack mitigation must be in place to prevent an attacker from authenticating to a service using a brute force attack?
- A . Forced password change every 6 months
- B . Use of a 100 ms delay between each authentication
- C . Use of a password manager
- D . Use of multifactor authentication for all accounts
