Practice Free 300-740 Exam Online Questions
DRAG DROP
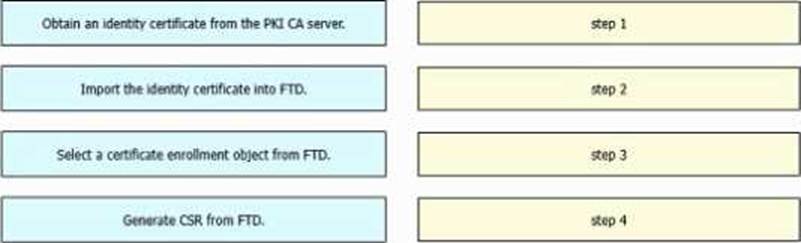
An engineer must configure certificate-based authentication in a cloud-delivered Cisco Secure Firewall Management Center. Drag and drop the steps from left to right to manually enroll certificates on a Cisco Secure Firewall Threat Defense Virtual device.

Which of the following are benefits of implementing cloud security policies for hybrid and multicloud environments?
- A . Enhanced agility and scalability
- B . Increased complexity in management
- C . Improved compliance with regulatory requirements
- D . Enhanced data sovereignty and privacy
Automated response actions based on telemetry reports can include:
- A . Blocking IP addresses associated with malicious activity
- B . Unconditionally trusting all internal network traffic
- C . Decreasing the sensitivity of intrusion detection systems
- D . Removing all forms of access control
Which web application firewall deployment in the Cisco Secure DDoS protects against application layer and volumetric attacks?
- A . Hybrid
- B . On-demand
- C . Always-on
- D . Active/passive
When determining security policies for application enforcement, which of the following is a key consideration?
- A . The popularity of the application among users
- B . The sensitivity of the data being accessed or stored by the application
- C . The color scheme of the application interface
- D . The programming language used to develop the application
Security audit reports are crucial for:
- A . Eliminating the need for security policies
- B . Promoting a false sense of security
- C . Reducing the overall security budget
- D . Identifying compliance gaps and areas lacking sufficient security controls
Cisco Secure Cloud Insights is designed to:
- A . Ignore cloud resources for simplified management
- B . Reduce the effectiveness of cloud security posture management
- C . Focus only on physical data center assets
- D . Provide visibility into cloud assets and their relationships for security purposes
Refer to the exhibit.
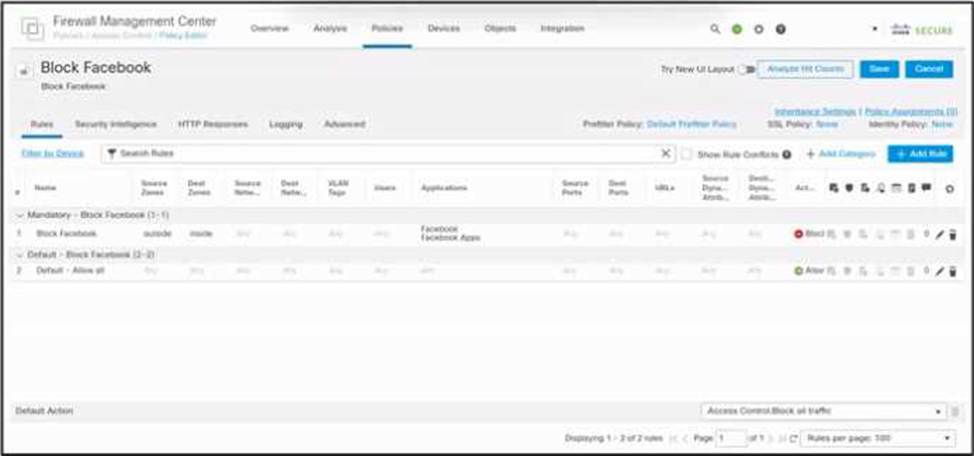
An engineer must block internal users from accessing Facebook and Facebook Apps. All other access must be allowed. The indicated policy was created in Cisco Secure Firewall Management Center and deployed to the internet edge firewall; however, users still can access Facebook.
Which two actions must be taken to meet the requirement? (Choose two.)
- A . Set Destination Zones to outside for rule 2.
- B . Set Source Zones to inside for rule 2.
- C . Set Applications to Facebook and Facebook Apps for rule 2.
- D . Set Destination Zones to outside for rule 1.
- E . Set Source Zones to inside for rule 1.
Refer to the exhibit.
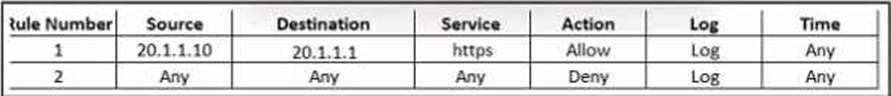
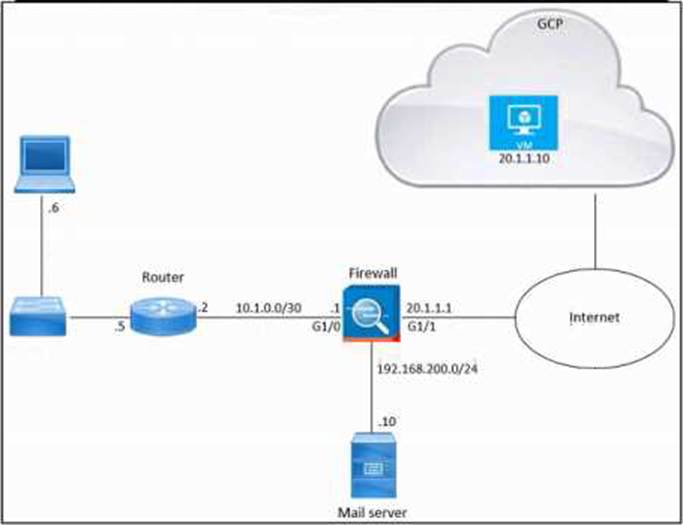
An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server.
Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
- A . Set IP address 192.168.200.10 as the destination in rule 1.
- B . Move up rule 2.
- C . Set IP address 20.1.1.1 as the source in rule 1.
- D . Configure a NAT rule.
- E . Configure a security group.
Network security in the Cisco Security Reference Architecture is divided into which two areas?
- A . Cloud-based and on-premises
- B . Internal and external
- C . Wired and wireless
- D . Physical and virtual
