Practice Free 300-740 Exam Online Questions
What are key considerations when implementing an integrated cloud security architecture?
- A . Ensuring compatibility between different cloud services
- B . Centralizing all data storage on-premises
- C . Implementing consistent security policies across environments
- D . Leveraging zero-trust principles
SAML and OIDC are both standards used for:
- A . Encrypting data on a device
- B . Web filtering
- C . User and device authentication in single sign-on scenarios
- D . Physical security of devices
Which of the following is true about multifactor authentication for devices?
- A . It only applies to mobile devices
- B . It makes devices easier to hack
- C . It can include something you know, something you have, and something you are
- D . It decreases security by simplifying access
Which of the following is a use case for visibility and assurance automation?
- A . Reducing the accuracy of threat detection
- B . Decreasing the speed of security operations
- C . Increasing manual intervention in security processes
- D . Automating the response to security incidents
Refer to the exhibit.
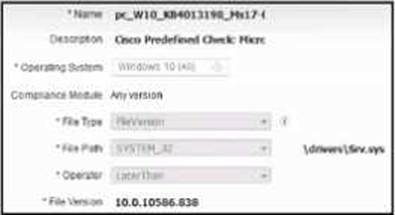
A security engineer must configure a posture policy in Cisco ISE to ensure that employee laptops have a critical patch for WannaCry installed before they can access the network.
Which posture condition must the engineer configure?
- A . Patch Management Condition
- B . File Condition
- C . Anti-Virus Condition
- D . Anti-Malware Condition
Implementing endpoint posture policies is crucial for:
- A . Decreasing network traffic
- B . Allowing all devices to access network resources without checks
- C . Ensuring devices comply with security standards before accessing the network
- D . Making the network accessible without a password
To allow users a seamless and secure login experience across multiple applications, many organizations configure _________ using an identity provider connection.
- A . VPNs
- B . firewalls
- C . SAML/SSO
- D . antivirus software
Cloud security attack tactics often include:
- A . Social media marketing strategies
- B . Exploiting misconfigured cloud storage
- C . Enhancing cloud service offerings
- D . Physical security breaches
The primary goal of direct-internet-access policies for trusted business applications is to:
- A . Completely bypass all security measures for speed
- B . Balance security and performance by allowing direct access under strict security controls
- C . Isolate the business application from the internet
- D . Eliminate the need for any form of web security
Refer to the exhibit.
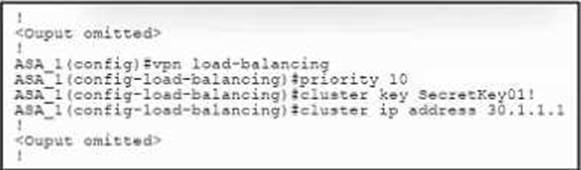
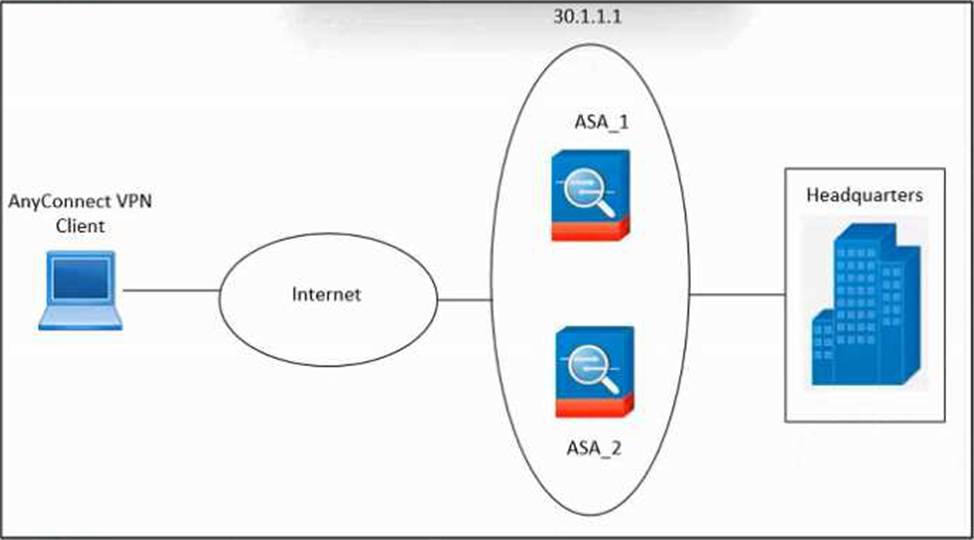
An engineer must configure VPN load balancing across two Cisco ASA. The indicated configuration was applied to each firewall; however, the load-balancing encryption scheme fails to work.
Which two commands must be run on each firewall to meet the requirements? (Choose two.)
- A . cluster port 9024
- B . crypto ikev1 policy 1
- C . hash sha-256
- D . encryption aes 256
- E . cluster encryption
