Practice Free 300-740 Exam Online Questions
Utilizing response automation can significantly reduce the time to _________ to incidents, thereby minimizing potential damage.
- A . escalate
- B . respond
- C . contribute
- D . neglect
An administrator must deploy an endpoint posture policy for all users. The organization wants to have all endpoints checked against antimalware definitions and operating system updates and ensure that the correct Secure Client modules are installed properly.
How must the administrator meet the requirements?
- A . Configure the WLC to provide local posture services, and configure Cisco ISE to receive the compliance verification from the WLC to be used in an authorization policy.
- B . Create an ASA Firewall posture policy, upload the Secure Client images to the NAD, and create a local client provisioning portal.
- C . Create the required posture policy within Cisco ISE, configure redirection on the NAD, and ensure that the client provisioning policy is correct.
- D . Identify the antimalware being used, create an endpoint script to ensure that it is updated, and send the update log to Cisco ISE for processing.
Implementing _________ via identity certificates is a secure method to verify the identities of users and devices accessing network resources.
- A . network segmentation
- B . endpoint protection
- C . data encryption
- D . user and device authentication
When determining security policies for network security edge to enforce application policy, which of the following considerations are important?
- A . The ability to inspect encrypted traffic
- B . The need to implement a simple, one-size-fits-all policy
- C . The integration of threat intelligence for real-time decision making
- D . The use of static rules that do not adapt to changing threat landscapes
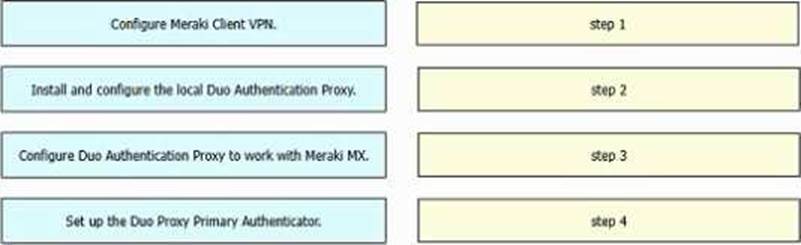
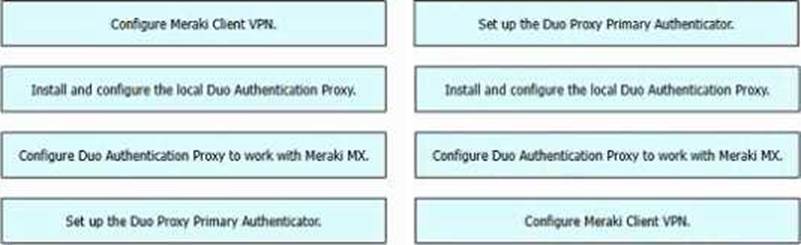
DRAG DROP
Drag and drop the tasks from the left into order on the right to implement adding Duo multifactor authentication to Meraki Client VPN login.
An administrator received an incident report indicating suspicious activity of a user using a corporate device. The manager requested that the credentials of user [email protected] be reset and synced via the Active Directory. Removing the account should be avoided and used for further investigation on data leak.
Which configuration must the administrator apply on the Duo Admin Panel?
- A . Delete the user in the Users tab option and sync it with the domain controller.
- B . Quarantine the user from all the policies on the Policies tab, including associated devices.
- C . Request the password change on the Device tab on managed devices.
- D . Disable the account on the Users tab and reset the password from the Active Directory.
In the context of network protocol blocking, which of the following statements is true?
- A . Blocking protocols like FTP can prevent unauthorized data transfers
- B . Protocol blocking is an outdated practice that reduces network efficiency
- C . Blocking protocols like BitTorrent can limit the spread of malware
- D . All network protocols should be allowed to ensure maximum compatibility
Security policies for remote users using VPN or application-based access should focus on:
- A . Ensuring all data is encrypted during transit
- B . Providing unrestricted access to internal resources
- C . Verifying user identity and device security before access
- D . Using public Wi-Fi networks without any security measures
Microsegmentation as a security policy is effective for:
- A . Isolating workloads from each other to reduce the attack surface
- B . Decreasing the overall security posture
- C . Simplifying access controls
- D . Centralizing all workloads
Which method is used by a Cisco XDR solution to prioritize actions?
- A . Updating antivirus signatures
- B . Monitoring endpoint activity
- C . Leveraging AI and machine learning
- D . Analyzing network traffic patterns
