Practice Free 300-715 Exam Online Questions
DRAG DROP
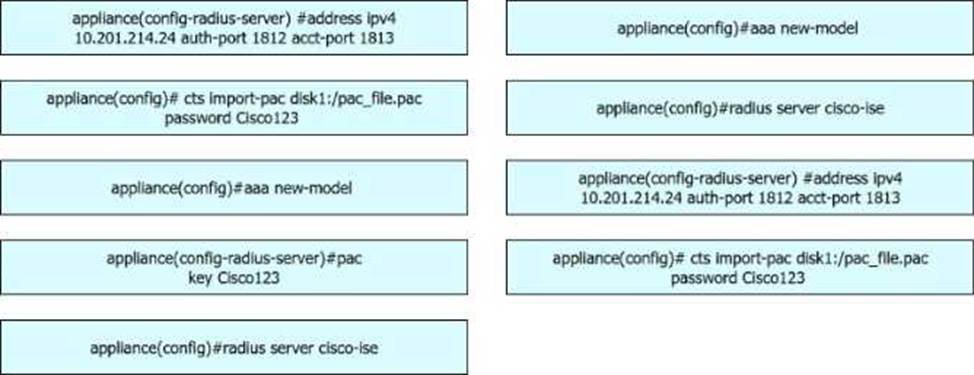
A security engineer configures a Cisco Catalyst switch to use Cisco TrustSec. The engineer must define the PAC key to authenticate the switch to Cisco IISE.
Drag and drop the commands from the left into sequence on the right. Not all options are used.

An employee must access the internet through the corporate network from a new mobile device that does not support native supplicant provisioning provided by Cisco ISE.
Which portal must the employee use to provision to the device?
- A . BYOD
- B . Personal Device
- C . My Devices
- D . Client Provisioning
An administrator needs to allow guest devices to connect to a private network without requiring usernames and passwords.
Which two features must be configured to allow for this? (Choose two.)
- A . hotspot guest portal
- B . device registration WebAuth
- C . central WebAuth
- D . local WebAuth
- E . self-registered guest portal
Which two fields are available when creating an endpoint on the context visibility page of Cisco IS? (Choose two)
- A . Policy Assignment
- B . Endpoint Family
- C . Identity Group Assignment
- D . Security Group Tag
- E . IP Address
There are several devices on a network that are considered critical and need to be placed into the ISE database and a policy used for them. The organization does not want to use profiling.
What must be done to accomplish this goal?
- A . Enter the MAC address in the correct Endpoint Identity Group.
- B . Enter the MAC address in the correct Logical Profile.
- C . Enter the IP address in the correct Logical Profile.
- D . Enter the IP address in the correct Endpoint Identity Group.
What service can be enabled on the Cisco ISE node to identity the types of devices connecting to a network?
- A . MAB
- B . profiling
- C . posture
- D . central web authentication
A network administrator changed a Cisco ISE deployment from pilot to production and noticed that the JVM memory utilization increased significantly. The administrator suspects this is due to replication between the nodes.
What must be configured to minimize performance degradation?
- A . Review the profiling policies for any misconfiguration
- B . Enable the endpoint attribute filter
- C . Change the reauthenticate interval.
- D . Ensure that Cisco ISE is updated with the latest profiler feed update
B
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-3/admin_guide/b_ise_admin_guide_23/b_ise_admin_guide_23_chapter_010111.html
What is the role of the Inline Posture Node (IPN. in Cisco ISE?
- A . It provides advanced threat protection.
- B . It serves as a gateway for guest access.
- C . It enforces compliance on non-compliant endpoints.
- D . It aggregates logs from multiple sources.
A Cisco ISE administrator must authenticate users against Microsoft Active Directory.
The solution must meet these requirements:
Users and computers must be authenticated.
User groups must be retrieved during authentication.
Which protocol must be added to the allowed protocols on the policy to authenticate the users?
- A . EAP-GTC
- B . EAP-TLS
- C . LEAP
- D . MS-CHAPv2
An engineer is configuring a virtual Cisco ISE deployment and needs each persona to be on a different node.
Which persona should be configured with the largest amount of storage in this environment?
- A . policy Services
- B . Primary Administration
- C . Monitoring and Troubleshooting
- D . Platform Exchange Grid
