Practice Free 300-715 Exam Online Questions
A user changes the status of a device to stolen in the My Devices Portal of Cisco ISE. The device was originally onboarded in the BYOD wireless Portal without a certificate. The device is found later, but the user cannot re-onboard the device because Cisco ISE assigned the device to the Blocklist endpoint identity group.
What must the user do in the My Devices Portal to resolve this issue?
- A . Manually remove the device from the Blocklist endpoint identity group.
- B . Change the device state from Stolen to Not Registered.
- C . Change the BYOD registration attribute of the device to None.
- D . Delete the device, and then re-add the device.
The security team identified a rogue endpoint with MAC address 00:46:91:02:28:4A attached to the network.
Which action must security engineer take within Cisco ISE to effectively restrict network access for this endpoint?
- A . Configure access control list on network switches to block traffic.
- B . Create authentication policy to force reauthentication.
- C . Add MAC address to the endpoint quarantine list.
- D . Implement authentication policy to deny access.
C
Explanation:
Cisco ISE provides a feature called Adaptive Network Control (ANC) that allows administrators to apply policies to endpoints based on their behavior or status1. One of the ANC policies is Quarantine, which restricts network access for an endpoint by assigning it to a limited-access VLAN or applying an access control list (ACL) on the switch port2. To use the Quarantine policy, the administrator must add the MAC address of the rogue endpoint to the endpoint quarantine list in ISE2. This will trigger a change of authorization (CoA) for the endpoint and apply the Quarantine policy. The other options are not effective for restricting network access for a rogue endpoint, as they do not use the ANC feature of ISE.
A network engineer is configuring a Cisco Wireless LAN Controller in order to find out more information about the devices that are connecting. This information must be sent to Cisco ISE to be used in authorization policies.
Which profiling mechanism must be configured in the Cisco Wireless LAN Controller to accomplish this task?
- A . DNS
- B . CDP
- C . DHCP
- D . ICMP
MacOS users are complaining about having to read through wordy instructions when remediating their workstations to gam access to the network.
Which alternate method should be used to tell users how to remediate?
- A . URL link
- B . message text
- C . executable
- D . file distribution
A
Explanation:
https://www.sciencedirect.com/topics/computer-science/remediation-action
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their Workstation from the corporate network.
Which CoA configuration meets this requirement?
- A . Port Bounce
- B . Reauth
- C . NoCoA
- D . Disconnect
C
Explanation:
https://ciscocustomer.lookbookhq.com/iseguidedjourney/ISE-profiling-design
An administrator must provide wired network access to unidentified Cisco devices that fail 802.1X authentication. Cisco ISE profiling services must be configured to gather Cisco Discovery Protocol and LLDP endpoint information from a Cisco switch.
These configurations were performed:
• configured switches to accept SNMP queries from Cisco ISE
• enabled Cisco Discovery Protocol and LLDP on the switches
• added the switch as a NAD to Cisco ISE
What must be enabled to complete the configuration?
- A . SNMP traps on the switch
- B . SNMP MIBs in Cisco ISE
- C . SNMP Trap probe in Cisco ISE
- D . SNMP Query probe in Cisco ISE
Refer to the exhibit.
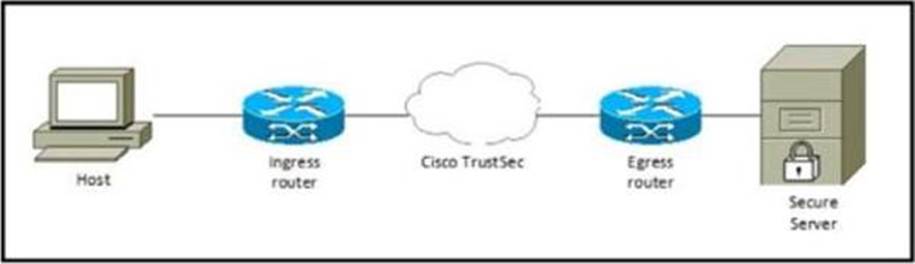
Which component must be configured to apply the SGACL?
- A . egress router
- B . host
- C . secure server
- D . ingress router
A
Explanation:
https://www.cisco.com/c/en/us/td/docs/switches/lan/trustsec/configuration/guide/trustsec/arch_over.html#52796
A network security engineer needs to configure 802.1X port authentication to allow a single host to be authenticated for data and another single host to be authenticated for voice.
Which command should the engineer run on the interface to accomplish this goal?
- A . authentication host-mode single-host
- B . authentication host-mode multi-auth
- C . authentication host-mode multi-host
- D . authentication host-mode multi-domain
An engineer must use Cisco ISE to provide network access to endpoints that cannot support 802.1X. The endpoint MAC addresses must be allowlisted by configuring an endpoint identity group.
These configurations were performed:
• configured an identity group named allowlist
• configured the endpoints to use the MAC address of incompatible 802.1X devices
• added the endpoints to the allowlist identity group
• configured an authentication policy for MAB users.
What must be configured?
- A . authorization profile that has the PermitAccess permission and matches the allowlist identity group
- B . logical profile that matches the allowlist identity group based on the configured policy
- C . authentication profile that has the PermitAccess permission and matches the allowlist identity group authorization policy that has the PermitAccess permission and matches the allowlist identity group
- D . authorization policy that has the PermitAccess permission and matches the allowtist identity group
A network engineer must enforce access control using special tags, without re-engineering the network design.
Which feature should be configured to achieve this in a scalable manner?
- A . SGT
- B . dACL
- C . VLAN
- D . RBAC
