Practice Free 300-710 Exam Online Questions
In Cisco FTD, which condition must be met to passively receive traffic that passes through the appliance using a TAP mode?
- A . The interface must be configured as inline tap.
- B . The device must be in routed mode.
- C . The interface must be set to passive mode.
- D . The interface must be set to transparent mode.
Refer to the exhibit.
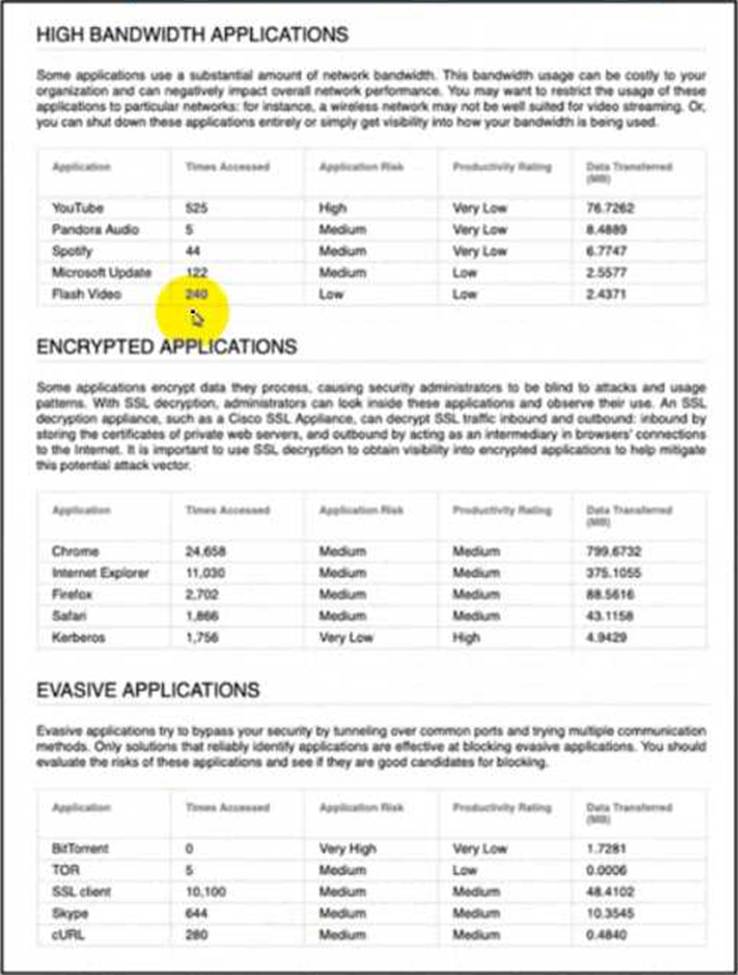
An engineer is analyzing a Network Risk Report from Cisco FMC.
Which application must the engineer take immediate action against to prevent unauthorized network use?
- A . Kerberos
- B . YouTube
- C . Chrome
- D . TOR
An administrator is configuring a transparent Cisco FTD device to receive ERSPAN traffic from multiple switches on a passive port but the FTD is not processing the traffic.
What is the problem?
- A . The switches do not have Layer 3 connectivity to the FTD device for GRE traffic transmission.
- B . The FTD must be configured with an ERSPAN port, not a passive port.
- C . The FTD must &e in routed mode to process ERSPAN traffic.
- D . The switches were not set up with a monitor session ID (hat matches the flow ID defined on the FTD
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access controls. A network administrator is analyzing the Cisco FTD events and notices that unknown user traffic is being allowed through the firewall.
How should this be addressed to block the traffic while allowing legitimate user traffic?
- A . Modify the Cisco ISE authorization policy to deny this access to the user.
- B . Modify Cisco ISE to send only legitimate usernames to the Cisco FTD.
- C . Add the unknown user in the Access Control Policy in Cisco FTD.
- D . Add the unknown user in the Malware & File Policy in Cisco FTD.
A network engineer must monitor threat events from the console of Cisco Secure Firewall Management Center. The engineer integrates the Cisco Secure Firewall Malware Defense in Secure Firewall Management Center.
Which action must the engineer take next?
- A . Log in to Cisco Secure Endpoint, click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection, and add a Secure Firewall Malware Defense cloud connection to Secure FMC.
- B . Log in to Secure Endpoint, click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection, add a Secure Firewall Malware Defense cloud connection to Secure FMC, and select the Secure Firewall Malware Defense cloud for Secure Endpoint.
- C . Add a Secure Firewall Malware Defense cloud connection in Secure FMC, log in to Secure Endpoint, and click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection.
- D . Add a Secure Firewall Malware Defense cloud connection in Secure FMC, select the Secure Firewall Malware Defense cloud for Secure Endpoint, log in to Secure Endpoint, and click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection.
Which feature sets up multiple interfaces on a Cisco Secure Firewall Threat Defense to be on the same subnet?
- A . EtherChannel
- B . SVI
- C . BVI
- D . security levels
A network engineer must configure an existing firewall to have a NAT configuration. The now configuration must support more than two interlaces per context. The firewall has previously boon operating transparent mode. The Cisco Secure Firewall Throat Defense (FTD) device has been deregistered from Cisco Secure Firewall Management Center (FMC).
Which set of configuration actions must the network engineer take next to meet the requirements?
- A . Run the configure manager add routed command from the Secure FTD device CL1, and reregister with Secure FMC.
- B . Run the configure firewall routed command from the Secure FTD device CD, and reregister with Secure FMC.
- C . Run the configure manager add routed command from the Secure FMC CLI. and reregister with Secure FMC.
- D . Run the configure firewall routed command from the Secure FMC CLI. and reregister with Secure FMC.
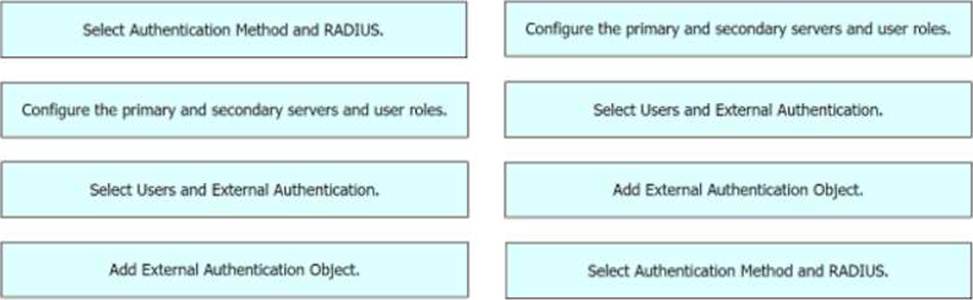
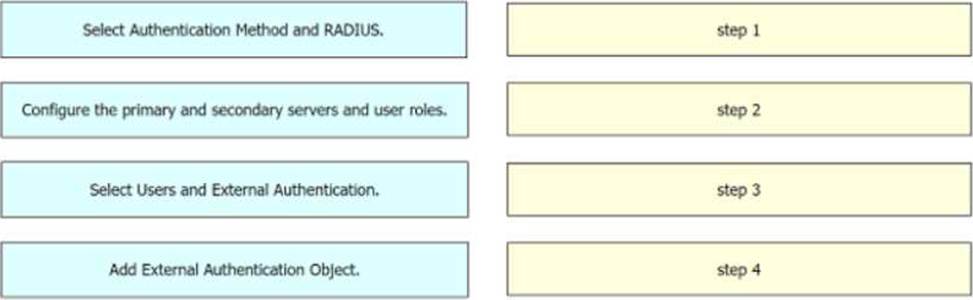
DRAG DROP
Drag and drop the configuration steps from the left into the sequence on the right to enable external authentication on Cisco FMC to a RADIUS server.
What is required to deploy a managed device inline in terms of network interfaces?
- A . Inline interfaces, security zones, MTU, and mode
- B . Inline interfaces, MTU, and mode
- C . Passive interface, MTU, and mode
- D . Passive interface, security zone, MTU, and mode
Which two routing options are valid with Cisco FTD? (Choose Two)
- A . BGPv6
- B . ECMP with up to three equal cost paths across multiple interfaces
- C . ECMP with up to three equal cost paths across a single interface
- D . BGPv4 in transparent firewall mode
- E . BGPv4 with nonstop forwarding