Practice Free 300-710 Exam Online Questions
A security engineer must configure a Cisco FTD appliance to inspect traffic coming from the internet. The Internet traffic will be mirrored from the Cisco Catalyst 9300 Switch.
Which configuration accomplishes the task?
- A . Set interface configuration mode to none.
- B . Set the firewall mode to transparent.
- C . Set the firewall mode to routed.
- D . Set interface configuration mode to passive.
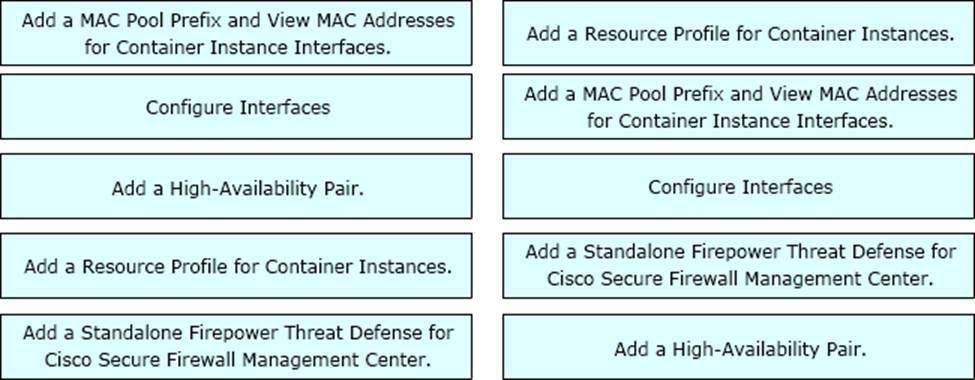
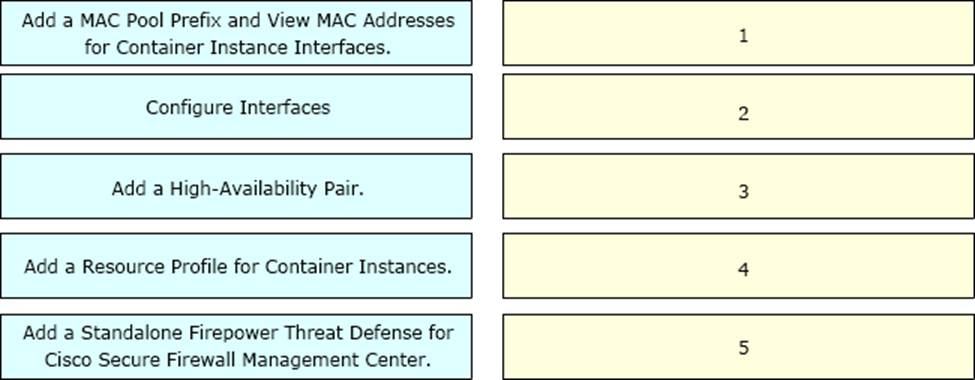
DRAG DROP
A network engineer is deploying a Cisco Firepower 4100 appliance and must configure a multi-instance environment for high availability.
Drag and drop me actions from the left into sequence on the right far this configuration.
An administrator configures the interfaces of a Cisco Secure Firewall Threat Defence device in an inline IPS deployment.
The administrator completes these actions:
* identifies the device and the interfaces
* sets the interface mode to inline
* enables the interlaces
Which configuration step must the administrator take next to complete the implementation?
- A . Enable spanning-tree PortFast on the interfaces.
- B . Configure an inline set
- C . Set the interface to Transparent mode.
- D . Set the interface to routed mode.
Which action must be taken to configure an isolated bridge group for IRB mode on a Cisco Secure Firewall device?
- A . Add the restricted segment to the ACL.
- B . Leave BVI interface name empty.
- C . Define the NAT pool for the blocked traffic.
- D . Remove the route from the routing table.
An engineer must replace a Cisco Secure Firewall high-availability device due to a failure. When the replacement device arrives, the engineer must separate the high-availability pair from Cisco Secure Firewall Management Center.
Which action must the engineer take first to restore high availability?
- A . Register the secondary device
- B . Force a break between the devices.
- C . Unregister the secondary device.
- D . Configure NTP time synchronization.
An engineer must configure the firewall to monitor traffic within a single subnet without increasing the hop count of that traffic.
How would the engineer achieve this?
- A . Configure Cisco Firepower as a transparent firewall
- B . Set up Cisco Firepower as managed by Cisco FDM
- C . Configure Cisco Firepower in FXOS monitor only mode.
- D . Set up Cisco Firepower in intrusion prevention mode
A network administrator is configuring a site-to-site IPsec VPN to a router sitting behind a Cisco FTD. The administrator has configured an access policy to allow traffic to this device on UDP 500, 4500, and ESP VPN traffic is not working.
Which action resolves this issue?
- A . Set the allow action in the access policy to trust.
- B . Enable IPsec inspection on the access policy.
- C . Modify the NAT policy to use the interface PAT.
- D . Change the access policy to allow all ports.
A network administrator reviews the file report for the last month and notices that all file types, except exe. show a disposition of unknown.
What is the cause of this issue?
- A . The malware license has not been applied to the Cisco FTD.
- B . The Cisco FMC cannot reach the Internet to analyze files.
- C . A file policy has not been applied to the access policy.
- D . Only Spero file analysis is enabled.
When a Cisco FTD device is configured in transparent firewall mode, on which two interface types can an IP address be configured? (Choose two.)
- A . Diagnostic
- B . EtherChannel
- C . BVI
- D . Physical
- E . Subinterface
What is a method used by Cisco Rapid Threat Containment to contain the threat in the network?
- A . change of authentication
- B . share context data
- C . TACACS+
- D . trustsec segmentation