Practice Free 300-710 Exam Online Questions
DRAG DROP
Refer to the exhibit.
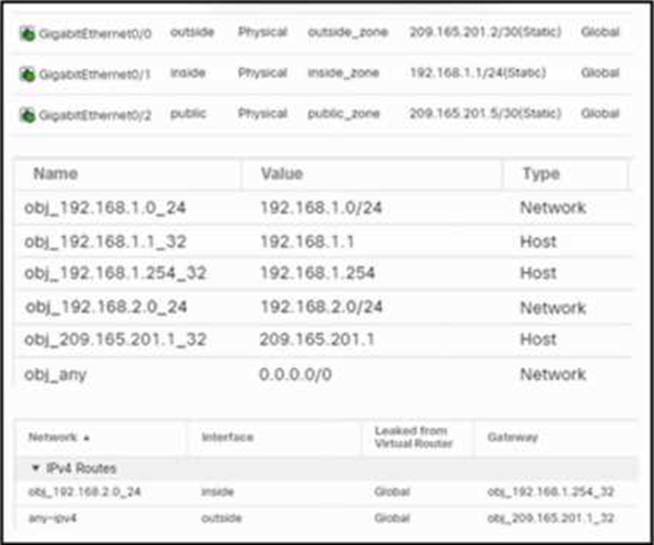
An engineer configures a NAT rule allowing clients to use the internet only if clients are located on the directly connected internal network. Dynamic auto PAT must be configured.
Drag and drop the NAT rules from the left onto the corresponding targets on the right. Not all options are used.

A network administrator is reviewing a weekly scheduled attacks risk report and notices a host that is flagged for an impact 2 attack.
Where should the administrator look within Cisco FMC to find out more relevant information about this host and attack?
- A . Analysis > Lookup > Whols
- B . Analysis > Correlation > Correlation Events
- C . Analysis > Hosts > Vulnerabilities
- D . Analysis > Hosts > Host Attributes
What are two application layer preprocessors? (Choose two.)
- A . CIFS
- B . IMAP
- C . SSL
- D . DNP3
- E . ICMP
Refer to the exhibit.
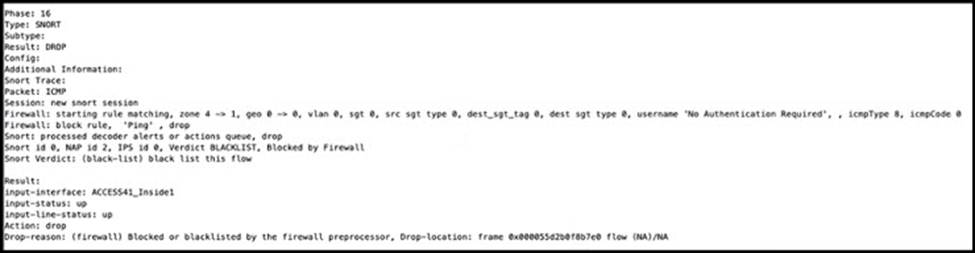
A systems administrator conducts a connectivity test to their SCCM server from a host machine and gets no response from the server.
Which action ensures that the ping packets reach the destination and that the host receives replies?
- A . Create an access control policy rule that allows ICMP traffic.
- B . Configure a custom Snort signature to allow ICMP traffic after Inspection.
- C . Modify the Snort rules to allow ICMP traffic.
- D . Create an ICMP allow list and add the ICMP destination to remove it from the implicit deny list.
Which command must be run to generate troubleshooting files on an FTD?
- A . system support view-files
- B . sudo sf_troubleshoot.pl
- C . system generate-troubleshoot all
- D . show tech-support
An engineer must configure email notifications on Cisco Secure Firewall Management Center. TLS encryption must be used to protect the messages from unauthorized access. The engineer adds the IP address of the mail relay host and must set the port number.
Which TCP port must the engineer use?
- A . 25
- B . 389
- C . 465
- D . 587
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation.
How will this issue be addresses globally in the quickest way possible and with the least amount of impact?
- A . by denying outbound web access
- B . Cisco Talos will automatically update the policies.
- C . by Isolating the endpoint
- D . by creating a URL object in the policy to block the website
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks.
What must be configured in order to maintain data privacy for both departments?
- A . Use a dedicated IPS inline set for each department to maintain traffic separation
- B . Use 802 1Q mime set Trunk interfaces with VLANs to maintain logical traffic separation
- C . Use passive IDS ports for both departments
- D . Use one pair of inline set in TAP mode for both departments
A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires that access control rule logs be collected for analysis. The security engineer is concerned that the Cisco FMC will not be able to process the volume of logging that will be generated.
Which configuration addresses this concern?
- A . Send Cisco FTD connection events and security events directly to SIEM system for storage and analysis.
- B . Send Cisco FTD connection events and security events to a cluster of Cisco FMC devices for storage and analysis.
- C . Send Cisco FTD connection events and security events to Cisco FMC and configure it to forward logs to SIEM for storage and analysis.
- D . Send Cisco FTD connection events directly to a SIEM system and forward security events from Cisco FMC to the SIEM system for storage and analysis.
An engineer is tasked with deploying an internal perimeter firewall that will support multiple DMZs
Each DMZ has a unique private IP subnet range.
How is this requirement satisfied?
- A . Deploy the firewall in transparent mode with access control policies.
- B . Deploy the firewall in routed mode with access control policies.
- C . Deploy the firewall in routed mode with NAT configured.
- D . Deploy the firewall in transparent mode with NAT configured.

