Practice Free 300-710 Exam Online Questions
What is the RTC workflow when the infected endpoint is identified?
- A . Cisco ISE instructs Cisco AMP to contain the infected endpoint.
- B . Cisco ISE instructs Cisco FMC to contain the infected endpoint.
- C . Cisco AMP instructs Cisco FMC to contain the infected endpoint.
- D . Cisco FMC instructs Cisco ISE to contain the infected endpoint.
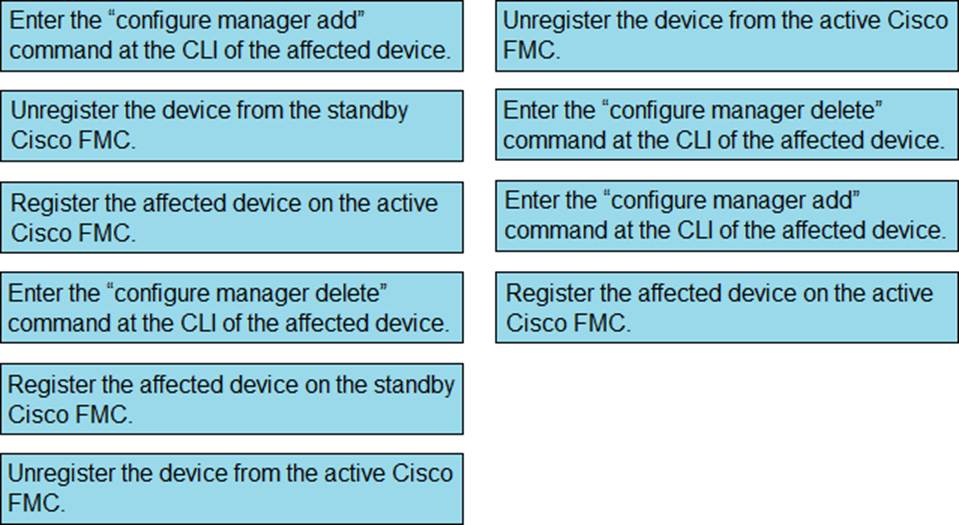
DRAG DROP
Drag and drop the steps to restore an automatic device registration failure on the standby Cisco FMC from the left into the correct order on the right. Not all options are used.
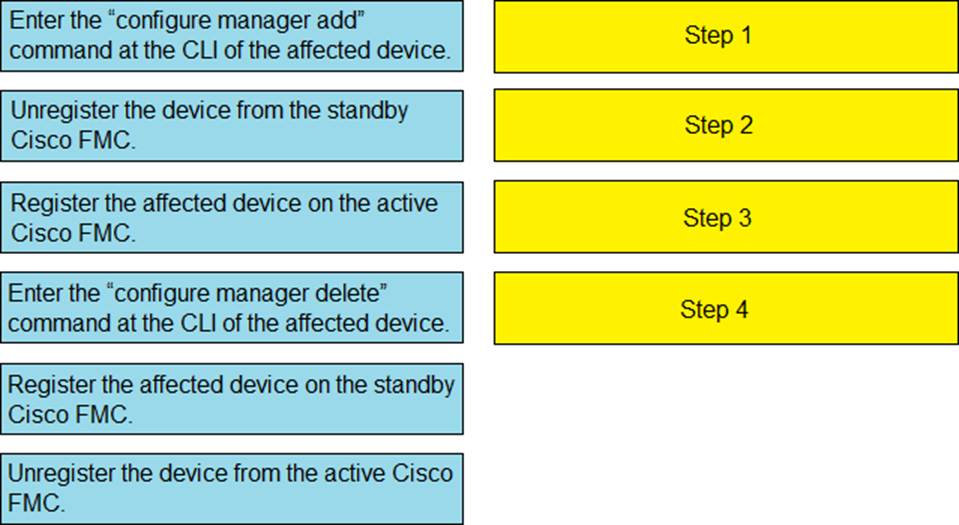
DRAG DROP
An engineer must configure high availability on two Cisco Secure Firewall Threat Defense appliances.
Drag and drop the configuration steps from the left into the sequence on the right.
Which two dynamic routing protocols are supported in Firepower Threat Defense without using FlexConfig? (Choose two.)
- A . EIGRP
- B . OSPF
- C . static routing
- D . IS-IS
- E . BGP
A network engineer sets up a secondary Cisco FMC that is integrated with Cisco Security Packet Analyzer.
What occurs when the secondary Cisco FMC synchronizes with the primary Cisco FMC?
- A . The existing integration configuration is replicated to the primary Cisco FMC
- B . The existing configuration for integration of the secondary Cisco FMC the Cisco Security Packet Analyzer is overwritten.
- C . The synchronization between the primary and secondary Cisco FMC fails
- D . The secondary Cisco FMC must be reintegrated with the Cisco Security Packet Analyzer after the synchronization
A security engineer needs to configure a network discovery policy on a Cisco FMC appliance and prevent excessive network discovery events from overloading the FMC database?
Which action must be taken to accomplish this task?
- A . Change the network discovery method to TCP/SYN.
- B . Configure NetFlow exporters for monitored networks.
- C . Monitor only the default IPv4 and IPv6 network ranges.
- D . Exclude load balancers and NAT devices in the policy.
Encrypted Visibility Engine (EVE) is enabled under which lab on an access control policy in Cisco Secure Firewall Management Centre?
- A . Network Analysis Policy
- B . Advanced
- C . Security Intelligence
- D . SSL
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two.)
- A . dynamic null route configured
- B . DHCP pool disablement
- C . quarantine
- D . port shutdown
- E . host shutdown
An engineer is configuring a new dashboard within Cisco Secure Firewall Management Center and is having trouble implementing a custom widget.
When a custom analysis widget is configured which option is mandatory for the system to display the information?
- A . table
- B . filter
- C . title
- D . results
An administrator configures a Cisco Secure Firewall Threat Defense device in transparent mode.
To configure the BVI (Bridge Virtual Interface), the administrator must:
Add a bridge-group interface
Configure a bridge-group ID
Configure the bridge-group interface description
Add bridge-group member interfaces
How must the engineer perform these actions?
- A . Configure a name for the bridge-group interface
- B . Set a security zone for the bridge-group interface
- C . Set the bridge-group interface mode to transparent
- D . Configure an IP address for the bridge-group interface