Practice Free 220-1102 Exam Online Questions
HOTSPOT
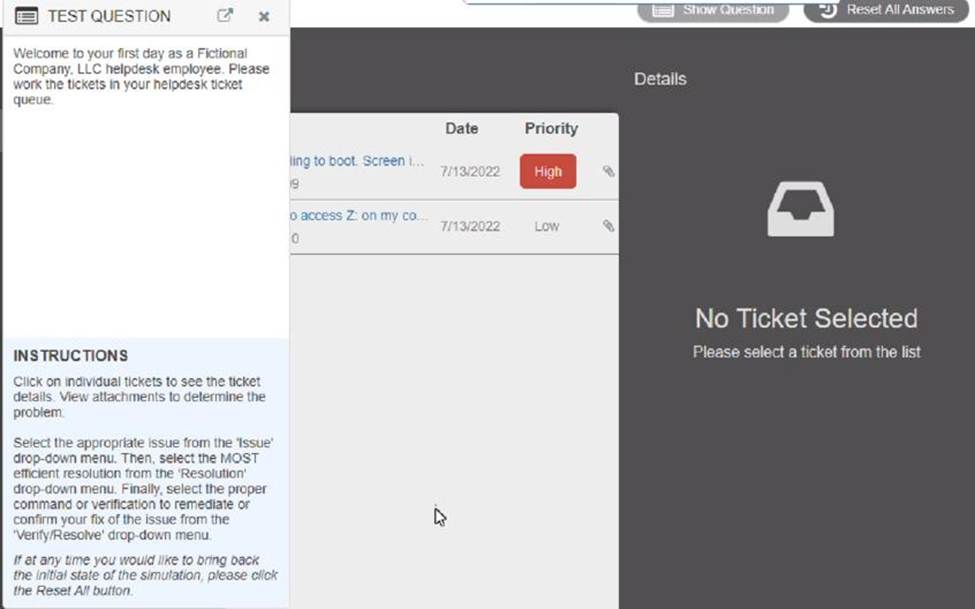
Welcome to your first day as a Fictional Company. LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
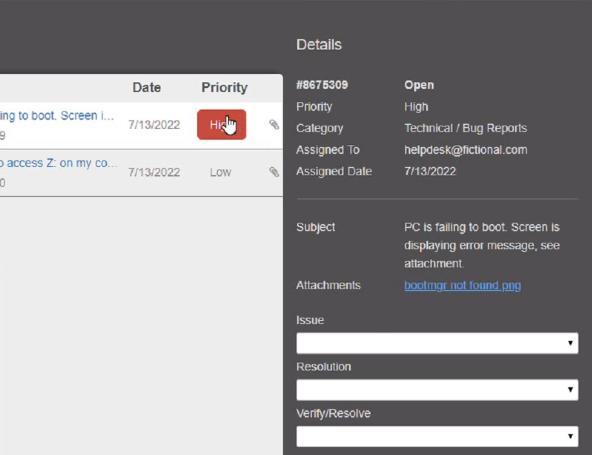
Click on individual tickers to see the ticket details. View attachments to determine the problem.
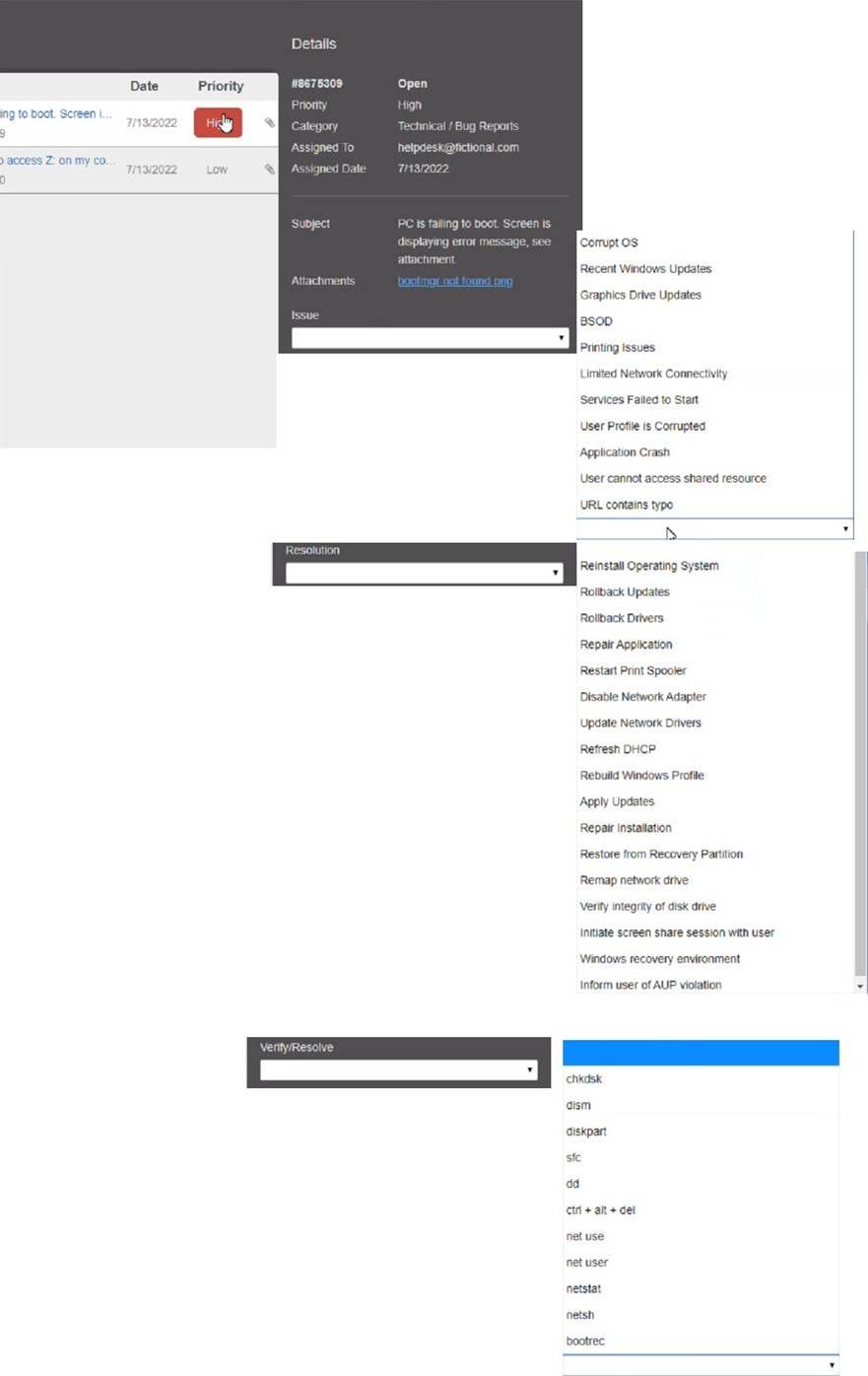
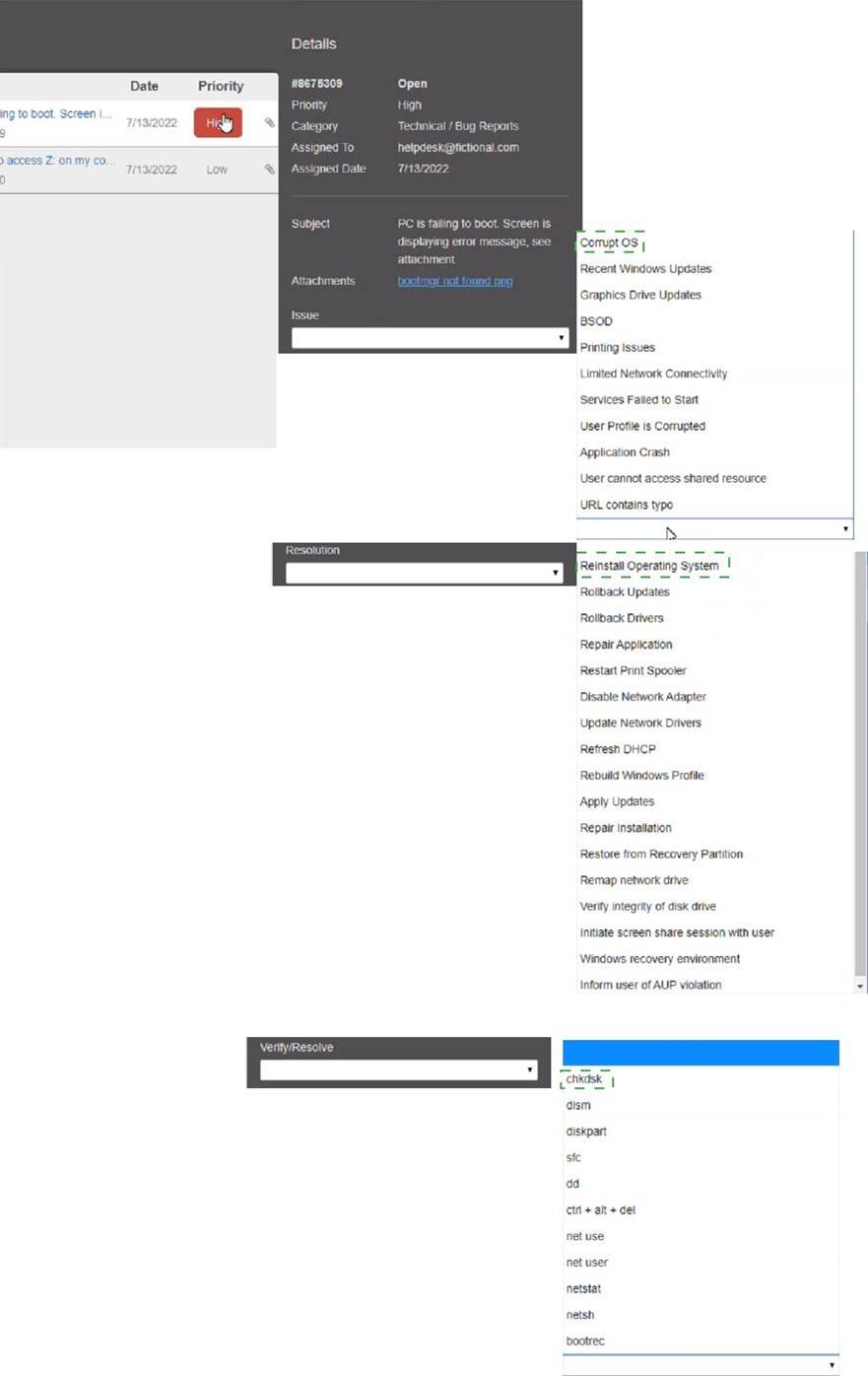
Select the appropriate issue from the ‘issue’ drop-down menu. Then, select the MOST efficient resolution from the ‘Resolution’ drop-down menu. Finally, select the proper command or verification to remediate or confirm your fix of the issue from the Verify Resolve drop-down menu.
Explanation:
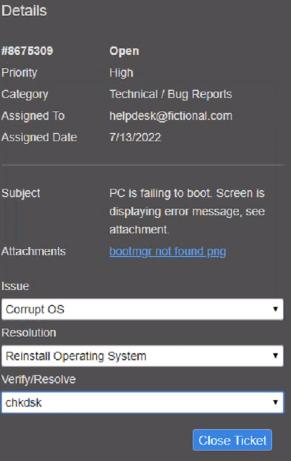
Graphical user interface, text, application
Description automatically generated
A user is unable to access the company’s network. A technician learns the user’s account became inaccessible after multiple unsuccessful login attempts. The user also changed their password before the issue started.
Which of the following steps should the technician take to resolve the issue?
- A . Escalate the user’s issue to the network team.
- B . Reset the user’s password.
- C . Unlock the user’s account.
- D . Verify the user’s login and password.
C
Explanation:
Detailed Explanation with Core 2
Reference: If multiple unsuccessful attempts led to the account being locked, the technician should unlock the account. Core 2 covers user account management practices, including unlocking accounts and managing failed login attempts (Core 2 Objective 2.5).
An administrator has submitted a change request for an upcoming server deployment.
Which of the following must be completed before the change can be approved?
- A . Risk analysis
- B . Sandbox testing
- C . End user acceptance
- D . Lessons learned
A
Explanation:
A risk analysis must be completed before a change request for an upcoming server deployment can be approved 1 Risk analysis is an important step in the change management process because it helps identify and mitigate potential risks before changes are implemented. Once the risks have been analyzed and the appropriate measures have been taken to minimize them, the change can be approved and implemented.
A user is unable to access a remote server from a corporate desktop computer using the appropriate terminal emulation program. The user contacts the help desk to report the issue.
Which of the following clarifying questions would be most effective for the help desk technician to ask the user in order to understand the issue?
- A . What is the error message?
- B . Does the program work on another computer?
- C . Did the program ever work?
- D . Is anyone else having this issue?
A
Explanation:
The most effective clarifying question for the help desk technician to ask the user in order to understand the issue is A) What is the error message? This question will help the technician to identify the possible cause and solution of the problem, as the error message will provide specific information about the nature and location of the error, such as the server name, the port number, the protocol, the authentication method, or the network status. The error message will also help the technician to troubleshoot the issue by following the suggested steps or searching for the error code online .
This question is more effective than the other choices because:
B) Does the program work on another computer? is not a very helpful question, as it will not reveal the source of the error or how to fix it. The program may work on another computer for various reasons, such as different network settings, firewall rules, permissions, or software versions. However, this question will not tell the technician what is wrong with the user’s computer or the remote server, or what needs to be changed or updated to make the program work.
C) Did the program ever work? is not a very relevant question, as it will not address the current issue or how to resolve it. The program may have worked in the past, but it may have stopped working due to changes in the network configuration, the server status, the software updates, or the user credentials. However, this question will not tell the technician what has changed or how to restore the program functionality.
D) Is anyone else having this issue? is not a very useful question, as it will not explain the reason or the solution for the error. The issue may affect only the user, or multiple users, depending on the scope and the impact of the error. However, this question will not tell the technician what is causing the error or how to fix it for the user or the others.
Reference: : How to Troubleshoot Terminal Emulation Problems – Techwalla : How to Read and Understand Windows Error Messages – Lifewire : How to Troubleshoot Network Connectivity Problems – How-To Geek : How to Troubleshoot Software Problems – dummies : How to Troubleshoot Common PC Issues For Users – MakeUseOf
Which of the following types of malicious software is most likely to demand payments in cryptocurrency?
- A . Ransomware
- B . Keylogger
- C . Cryptomining
- D . Rootkit
A
Explanation:
Comprehensive and Detailed In-Depth
Ransomware is a type of malware that encrypts files and demands payment (usually in cryptocurrency) to decrypt them.
B. Keylogger C Tracks keystrokes but does not demand payment.
C. Cryptomining C Uses system resources to mine cryptocurrency without the user’s consent.
D. Rootkit C Hides malicious software but does not demand payment.
Reference: CompTIA A+ 220-1102, Objective 2.5 C Common Security Threats
A desktop support technician is tasked with migrating several PCs from Windows 7 Pro to Windows 10 Pro, The technician must ensure files and user preferences are retained, must perform the operation locally, and should migrate one station at a time.
Which of the following methods would be MOST efficient?
- A . Golden image
- B . Remote network install
- C . In-place upgrade
- D . Clean install
C
Explanation:
An in-place upgrade is the most efficient method for migrating from Windows 7 Pro to Windows 10 Pro, as it will retain all user files and preferences, can be done locally, and can be done one station at a time. An in-place upgrade involves installing the new version of Windows over the existing version, and can be done quickly and easily.
A user is being directed by the help desk to look up a Windows PC’s network name so the help desk can use a remote administration tool to assist the user.
Which of the following commands would allow the user to give the technician the correct information? (Select TWO).
- A . ipconfig /all
- B . hostname
- C . netstat /?
- D . nslookup localhost
- E . arp ―a
- F . ping :: 1
A,B
Explanation:
The user can use the following commands to give the technician the correct information: ipconfig /all and hostname 1. The ipconfig /all command displays the IP address, subnet mask, and default gateway for all adapters on the computer 1. The hostname command displays the name of the computer 1.
A user needs assistance changing the desktop wallpaper on a Windows 10 computer.
Which of the following methods will enable the user to change the wallpaper using a Windows 10 Settings tool?
- A . Open Settings, select Accounts, select Your info, click Browse, and then locate and open the image the user wants to use as the wallpaper.
- B . Open Settings, select Personalization, click Browse, and then locate and open the image the user wants to use as the wallpaper.
- C . Open Settings, select System, select Display, click Browse, and then locate and open the image the user wants to use as the wallpaper.
- D . Open Settings, select Apps, select Apps & features, click Browse, and then locate and open the image the user wants to use as the wallpaper.
B
Explanation:
The user can change the wallpaper using a Windows 10 Settings tool by following these steps12:
✑ Open Settings by pressing the Windows key and typing Settings, or by clicking the gear icon in the Start menu.
✑ Select Personalization from the left navigation menu.
✑ On the right side of the window, click Background.
✑ In the Background settings, click the drop-down menu and select Picture as the background type.
✑ Click Browse and then locate and open the image the user wants to use as the wallpaper.
The other options are incorrect because they do not lead to the Background settings or they do not allow the user to browse for an image. Accounts, System, and Apps are not related to personalization settings. Your info, Display, and Apps & features are not related to wallpaper settings.
References: 1: https://support.microsoft.com/en-us/windows/change-your-desktop-background-image-175618be-4cf1-c159-2785-ec2238b433a8 2: https://www.computerhope.com/issues/ch000592.htm
A user is experiencing frequent malware symptoms on a Windows workstation. The user has tried several times to roll back the state but the malware persists.
Which of the following would MOST likely resolve the issue?
- A . Quarantining system files
- B . Reimaging the workstation
- C . Encrypting the hard drive
- D . Disabling TLS 1.0 support
B
Explanation:
A user reports that text on the screen is too small. The user would like to make the text larger and easier to see.
Which of the following is the BEST way for the user to increase the size of text, applications, and other items using the Windows 10 Settings tool?
- A . Open Settings select Devices, select Display, and change the display resolution to a lower resolution option
- B . Open Settings, select System, select Display, and change the display resolution to a lower resolution option.
- C . Open Settings Select System, select Display, and change the Scale and layout setting to a higher percentage.
- D . Open Settings select Personalization, select Display and change the Scale and layout setting to a higher percentage
C
Explanation:
Open Settings, select System, select Display, and change the Scale and layout setting to a higher percentage123
Reference: 4.
How to Increase the Text Size on Your Computer. Retrieved from https://www.laptopmag.com/articles/increase-text-size-computer 5.
How to Change the Size of Text in Windows 10. Retrieved from https://www.howtogeek.com/370055/how-to-change-the-size-of-text-in-windows-10/ 6. Change the size of text in Windows. Retrieved from https://support.microsoft.com/en-us/windows/change-the-size-of-text-in-windows-1d5830c3-eee3-8eaa-836b-abcc37d99b9a
