Practice Free 220-1102 Exam Online Questions
A workstation’s hard drive is making loud noises, applications are running slowly, and the workstation is rebooting unexpectedly.
Which of the following should the technician do first to begin troubleshooting the issue?
- A . Perform a System Restore.
- B . Open Disk Cleanup.
- C . Replace the hard drive.
- D . Run CHKDSK.
D
Explanation:
The correct answer is D. Run CHKDSK (Check Disk).
CHKDSK is a command-line utility that scans and repairs file system errors and bad sectors on a disk. Running this tool first can determine whether the hard drive is experiencing file system corruption or physical failure.
If CHKDSK reports bad sectors or extensive corruption, it indicates that the drive is failing, and data backup should be performed immediately before replacing the drive.
Syntax Example:
chkdsk /f /r
/f C Fixes file system errors.
/r C Locates bad sectors and recovers readable information.
Why Other Options Are Incorrect:
A technician needs to configure laptops so that only administrators can enable virtualization technology if needed.
Which of the following should the technician configure?
- A . BIOS password
- B . Guest account
- C . Screen lock
- D . AutoRun setting
A
Explanation:
Reference: CompTIA A+ Certification Core 2 220-1102, Objective 2.6 (System Security Controls).
A user lost a company tablet that was used for customer intake at a doctor’s office.
Which of the following actions would BEST protect against unauthorized access of the data?
- A . Changing the office’s Wi-Fi SSID and password
- B . Performing a remote wipe on the device
- C . Changing the user’s password
- D . Enabling remote drive encryption
B
Explanation:
The best action to protect against unauthorized access of the data on the lost company tablet is to perform a remote wipe on the device. A remote wipe is a feature that allows an administrator or a user to erase all the data and settings on a device remotely, usually through a web portal or an email command. A remote wipe can help prevent the data from being accessed or compromised by anyone who finds or steals the device. Changing the office’s Wi-Fi SSID and password may prevent the device from connecting to the office network but may not prevent the data from being accessed locally or through other networks. Changing the user’s password may prevent the device from logging in to the user’s account but may not prevent the data from being accessed by other means or accounts. Enabling remote drive encryption may protect the data from being read by unauthorized parties but may not be possible if the device is already lost or turned off. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 3.1
Employees want their Windows 10 laptops to wirelessly connect when they take them home.
Which of the following should the employees configure so the laptops can automatically connect wirelessly?
- A . Network and Internet settings
- B . Windows Firewall settings
- C . Devices and Printers
- D . Personalization settings
A
Explanation:
To ensure that Windows 10 laptops can automatically connect to Wi-Fi networks when employees take them home, the appropriate configuration is:
Network and Internet settings: These settings allow users to manage Wi-Fi connections, configure automatic connections to known networks, and manage network profiles. Go to Settings > Network & Internet > Wi-Fi.
Ensure the option to connect automatically to the home Wi-Fi network is enabled.
Windows Firewall settings: These are used to manage firewall rules and do not control Wi-Fi connectivity.
Devices and Printers: Used for managing connected devices and printers, not for network connections.
Personalization settings: These settings are for customizing the appearance of the Windows interface and do not affect network connections.
Reference: CompTIA A+ 220-1102 Exam Objectives, Section 1.6: Given a scenario configure Microsoft Windows networking features on a client/desktop.
Windows network configuration documentation.
A malicious user was able to export an entire website’s user database by entering specific commands into a field on the company’s website.
Which of the following did the malicious user most likely exploit to extract the data?
- A . Cross-site scripting
- B . SQL injection
- C . Brute-force attack
- D . DDoS attack
B
Explanation:
SQL injection is a type of attack that takes advantage of vulnerabilities in a web application’s database query software, allowing an attacker to send malicious SQL commands through the application to the database. These commands can manipulate the database and can lead to unauthorized data access or manipulation.
SQL injection: In the scenario described, the malicious user was able to export an entire website’s user database by entering specific commands into a field on the company’s website, which is a classic example of an SQL injection attack. This type of attack exploits vulnerabilities in the database layer of an application to execute unauthorized SQL commands.
Cross-site scripting (A) involves injecting malicious scripts into content from otherwise trusted websites. A brute-force attack (C) is an attempt to gain access to a system by systematically checking all possible keys or passwords until the correct one is found. A DDoS attack (D) is an attempt to make a machine or network resource unavailable to its intended users by overwhelming it with a flood of internet traffic.
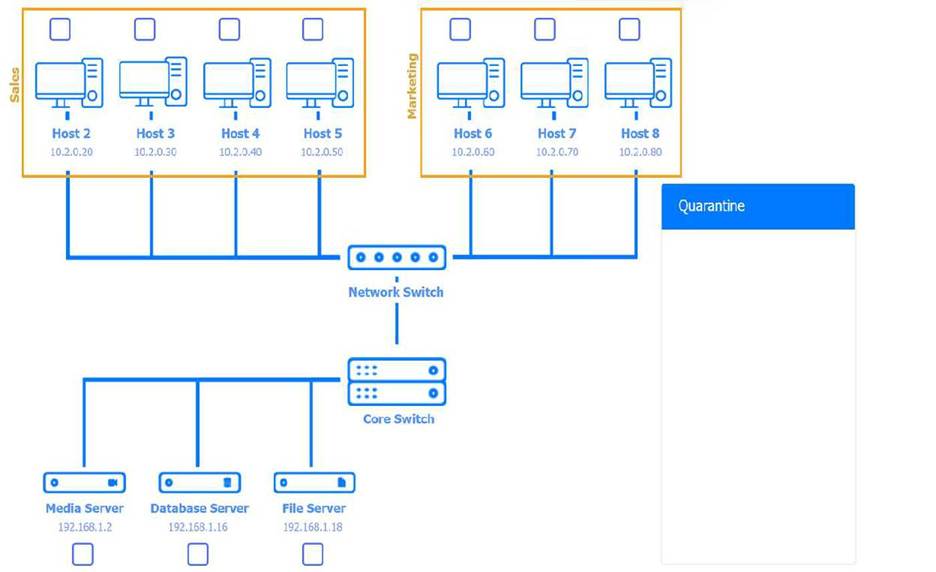
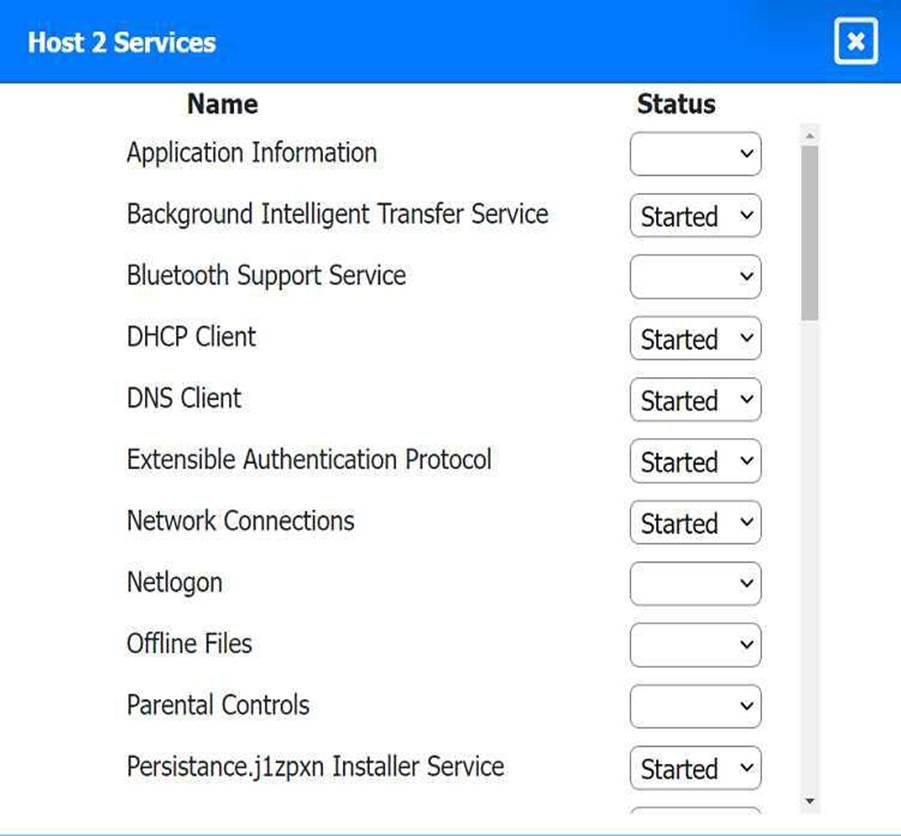
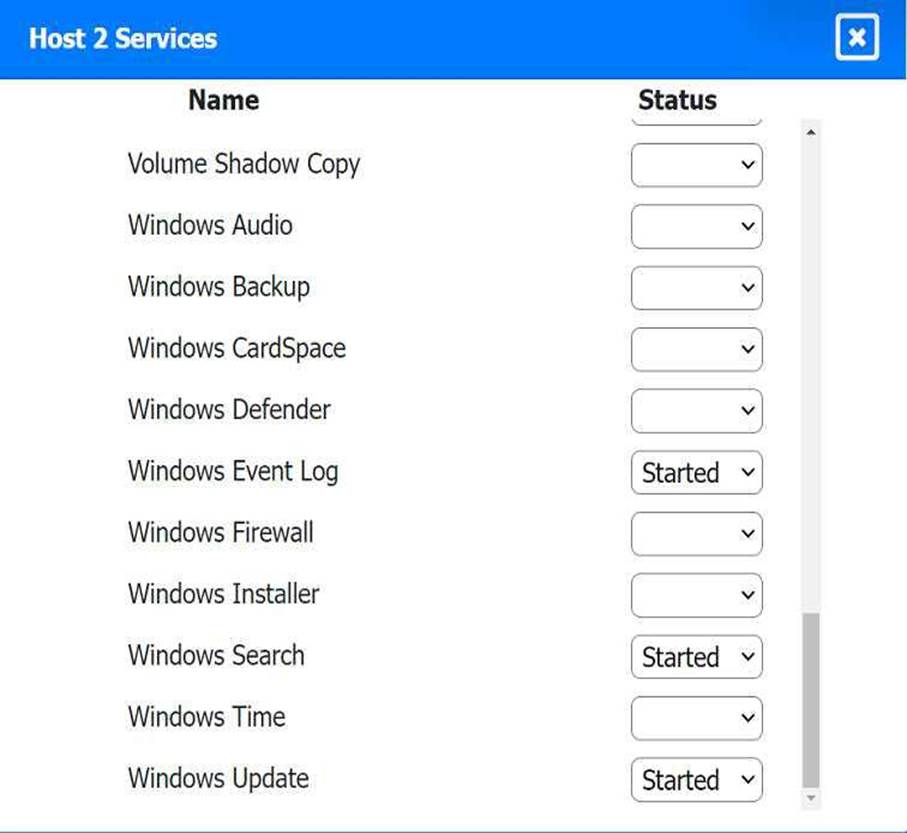
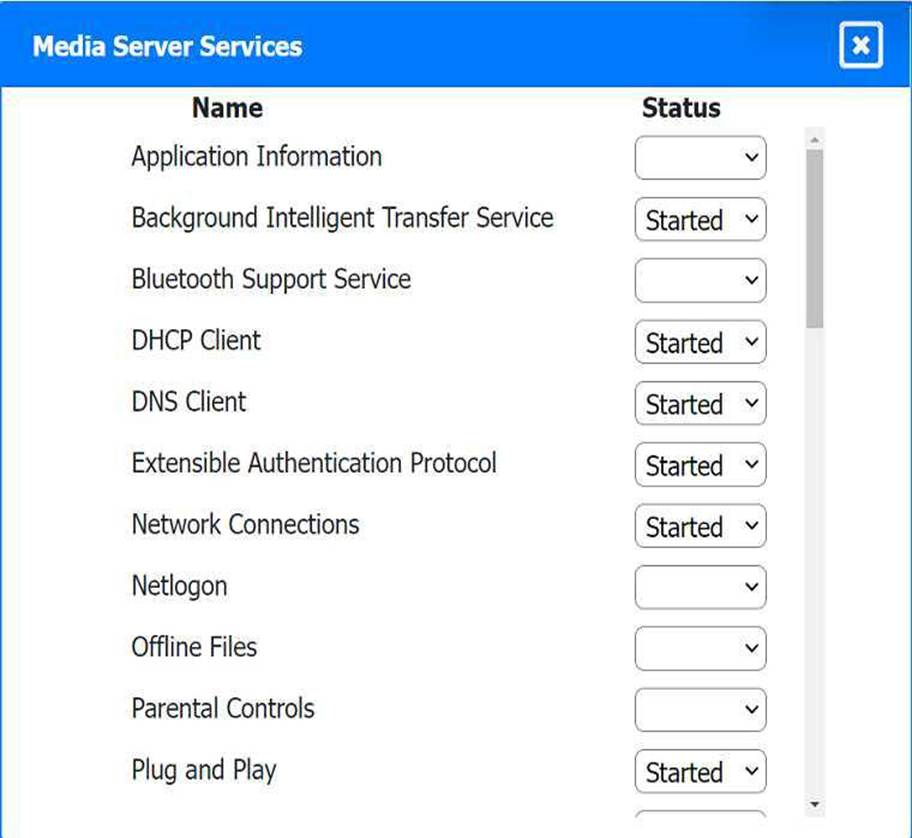
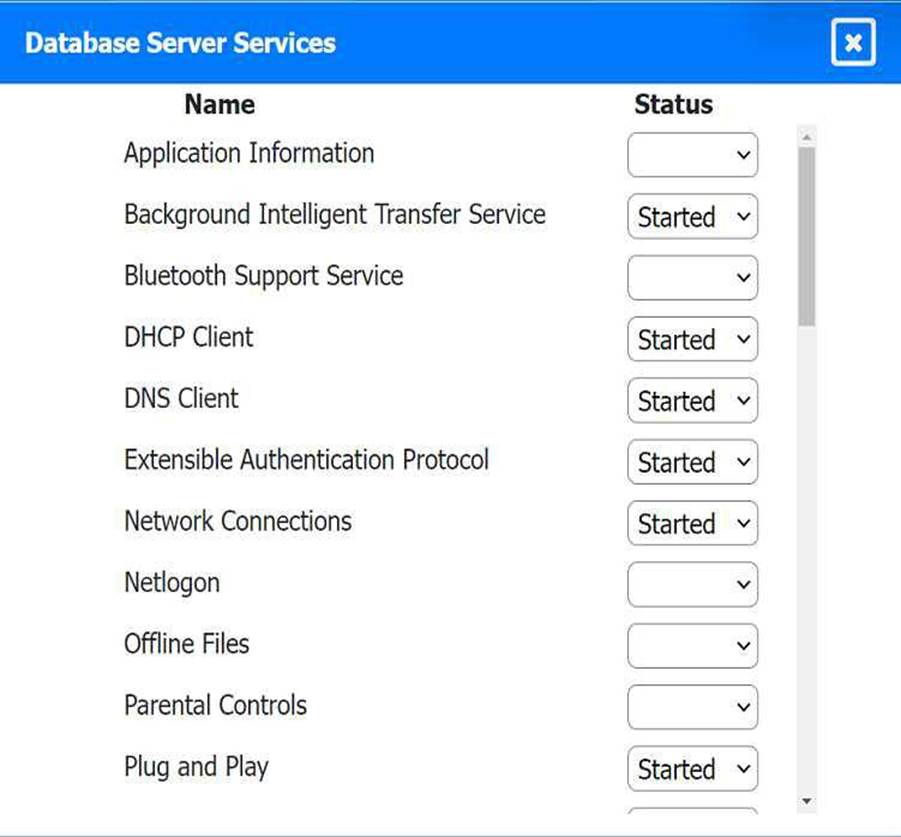
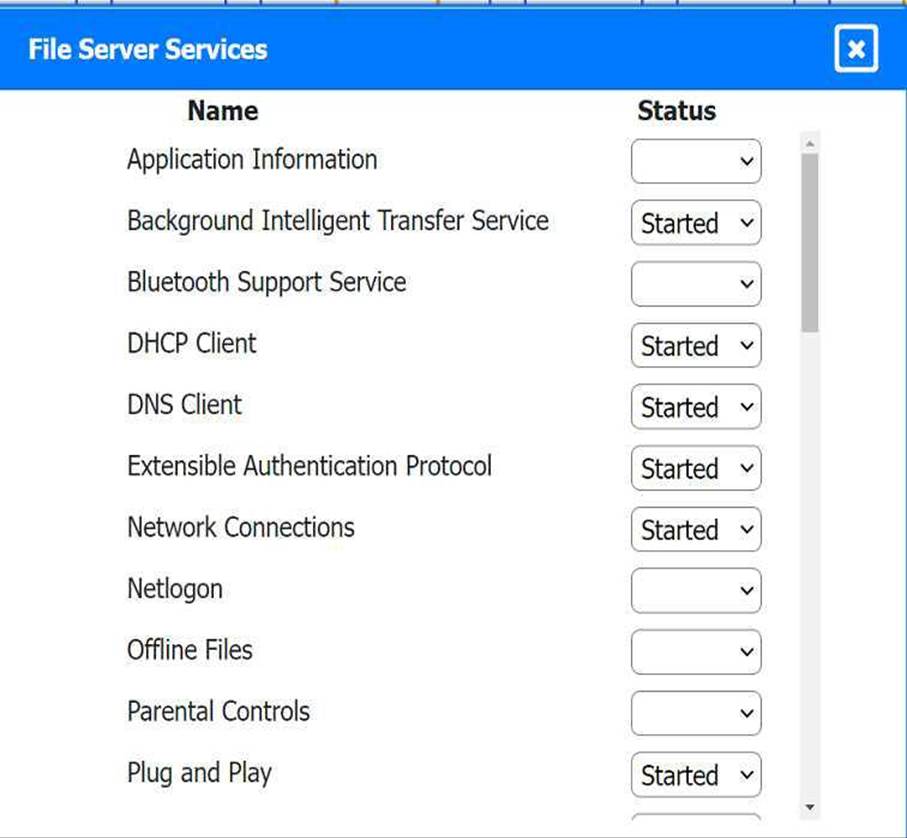
Multiple users are reporting audio issues as well as performance issues after downloading
unauthorized software. You have been dispatched to identify and resolve any issues on the network using best practice procedures.
INSTRUCTIONS
Quarantine and configure the appropriate device(s) so that the users’ audio issues are
resolved using best practice procedures.
Multiple devices may be selected for quarantine.
Click on a host or server to configure services.
A customer is configuring on an old desktop an inexpensive file server to share photos and videos
and wants to avoid complicated licensing.
Which of the following operating systems should the technician most likely recommend?
- A . Chrome OS
- B . Linux
- C . macOS
- D . Windows
B
Explanation:
For an inexpensive file server to share photos and videos while avoiding complicated licensing, the technician should recommend:
Linux: Linux is a free and open-source operating system that is ideal for setting up a file server. It offers robust file-sharing capabilities with minimal licensing complications.
Chrome OS: Designed primarily for lightweight, web-based tasks and not ideal for a file server.
macOS: Requires Apple hardware and involves more complex licensing compared to Linux.
Windows: While capable of being a file server, Windows may involve licensing fees, particularly for server editions.
Reference: CompTIA A+ 220-1102 Exam Objectives, Section 1.8: Explain common OS types and their purposes.
Linux documentation and its use in setting up file servers.
A company is experiencing a ODDS attack. Several internal workstations are the source of the traffic.
Which of the following types of infections are the workstations most likely experiencing? (Select two)
- A . Zombies
- B . Keylogger
- C . Adware
- D . Botnet
- E . Ransomvvare
- F . Spyware
AD
Explanation:
The correct answers are A and D) Zombies and botnets are types of infections that allow malicious actors to remotely control infected computers and use them to launch distributed denial-of-service (DDoS) attacks against a target. A DDoS attack is a type of cyberattack that aims to overwhelm a server or a network with a large volume of traffic from multiple sources, causing it to slow down or crash.
A keylogger is a type of malware that records the keystrokes of a user and sends them to a remote server, often for the purpose of stealing passwords, credit card numbers, or other sensitive information.
Adware is a type of software that displays unwanted advertisements on a user’s computer, often in the form of pop-ups, banners, or redirects. Adware can also collect user data and compromise the security and performance of the system.
Ransomware is a type of malware that encrypts the files or locks the screen of a user’s computer and demands a ransom for their restoration. Ransomware can also threaten to delete or expose the user’s data if the ransom is not paid.
Spyware is a type of software that covertly monitors and collects information about a user’s online activities, such as browsing history, search queries, or personal data. Spyware can also alter the settings or functionality of the user’s system without their consent.
Which of the following commands should a technician use to change user permissions?
- A . sudo
- B . chmod
- C . mv
- D . pwd
B
Explanation:
The chmod command in Unix/Linux systems changes file and directory permissions, allowing a technician to control read, write, and execute rights for users and groups. sudo allows running commands with elevated privileges but doesn’t directly change permissions. mv moves or renames files, and pwd prints the current working directory. Core 2 exam content covers basic Linux command-line utilities where chmod is essential for managing permissions to secure files and directories.
A company acquired a local office, and a technician is attempting to join the machines at the office to the local domain. The technician notes that the domain join option appears to be missing.
Which of the following editions of Windows is MOST likely installed on the machines?
- A . Windows Professional
- B . Windows Education
- C . Windows Enterprise
- D . Windows Home
D
Explanation:
Windows Home is the most likely edition of Windows installed on the machines that do not have the domain join option. Windows Home is a consumer-oriented edition that does not support joining a domain or using Group Policy. Only Windows Professional, Education, and Enterprise editions can join a domain
