Practice Free 220-1102 Exam Online Questions
A technician is troubleshooting a computer with a suspected short in the power supply.
Which of the following is the FIRST step the technician should take?
- A . Put on an ESD strap
- B . Disconnect the power before servicing the PC.
- C . Place the PC on a grounded workbench.
- D . Place components on an ESD mat.
B
Explanation:
The first step a technician should take when troubleshooting a computer with a suspected short in the power supply is B. Disconnect the power before servicing the PC. This is to prevent any electrical shock or damage to the components. A power supply can be dangerous even when unplugged, as capacitors can maintain a line voltage charge for a long time1. Therefore, it is important to disconnect the power cord and press the power button to discharge any residual power before opening the case2. The other steps are also important for safety and proper diagnosis, but they should be done after disconnecting the power.
A user receives a notification indicating the antivirus protection on a company laptop is out of date. A technician is able to ping the user’s laptop. The technician checks the antivirus parent servers and sees the latest signatures have been installed. The technician then checks the user’s laptop and finds the antivirus engine and definitions are current.
Which of the following has MOST likely occurred?
- A . Ransomware
- B . Failed OS updates
- C . Adware
- D . Missing system files
C
Explanation:
Which of the following should be documented to ensure that the change management plan is followed?
- A . Scope of the change
- B . Purpose of the change
- C . Change rollback plan
- D . Change risk analysis
A
Explanation:
The scope of the change is one of the elements that should be documented to ensure that the change management plan is followed. The scope of the change defines the boundaries and limitations of the change, such as what is included and excluded, what are the deliverables and outcomes, what are the assumptions and constraints, and what are the dependencies and risks. The scope of the change helps to clarify the expectations and objectives of the change, as well as to prevent scope creep or deviation from the original plan. The scope of the change also helps to measure the progress and success of the change, as well as to communicate the change to the stakeholders and the team
An organization implemented a method of wireless security that requires both a user and the user’s computer to be in specific managed groups on the server in order to connect to Wi-Fi.
Which of the following wireless security methods BEST describes what this organization implemented?
- A . TKIP
- B . RADIUS
- C . WPA2
- D . AES
B
Explanation:
RADIUS stands for Remote Authentication Dial-In User Service and it is a protocol that provides centralized authentication, authorization, and accounting for network access. RADIUS can be used to implement a method of wireless security that requires both a user and the user’s computer to be in specific managed groups on the server in order to connect to Wi-Fi. This is also known as 802.1X authentication or EAP-TLS authentication
A data center is required to destroy SSDs that contain sensitive information.
Which of the following is the BEST method to use for the physical destruction of SSDs?
- A . Wiping
- B . Low-level formatting
- C . Shredding
- D . Erasing
C
Explanation:
Shredding is the best method to use for the physical destruction of SSDs because it reduces them to small pieces that cannot be recovered or accessed. Wiping, low-level formatting, and erasing are not effective methods for destroying SSDs because they do not physically damage the flash memory chips that store data1.
Which of the following is also known as something you know, something you have, and something you are?
- A . ACL
- B . MFA
- C . SMS
- D . NFC
B
Explanation:
MFA stands for Multi-Factor Authentication, which is a method of verifying a user’s identity using two or more different factors of authentication. The three factors of authentication are something you know, something you have, and something you are. These factors correspond to different types of information or evidence that only the legitimate user should possess or provide. For example: Something you know: a password, a PIN, a security question, etc. Something you have: a smart card, a token, a mobile device, etc.
Something you are: a fingerprint, a face, an iris, etc.
MFA provides a higher level of security than single-factor authentication, which only uses one factor, such as a password. MFA reduces the risk of unauthorized access, identity theft, and data breaches, as an attacker would need to compromise more than one factor to impersonate a user. MFA is commonly used for online banking, email accounts, cloud services, and other sensitive applications
Which of the following techniques is used by a threat actor to obtain information through physical means?
- A . Denial of service
- B . Brute force
- C . Dumpster diving
- D . Evil twin
An executive has contacted you through the help-desk chat support about an issue with a mobile device.
Assist the executive to help resolve the issue.
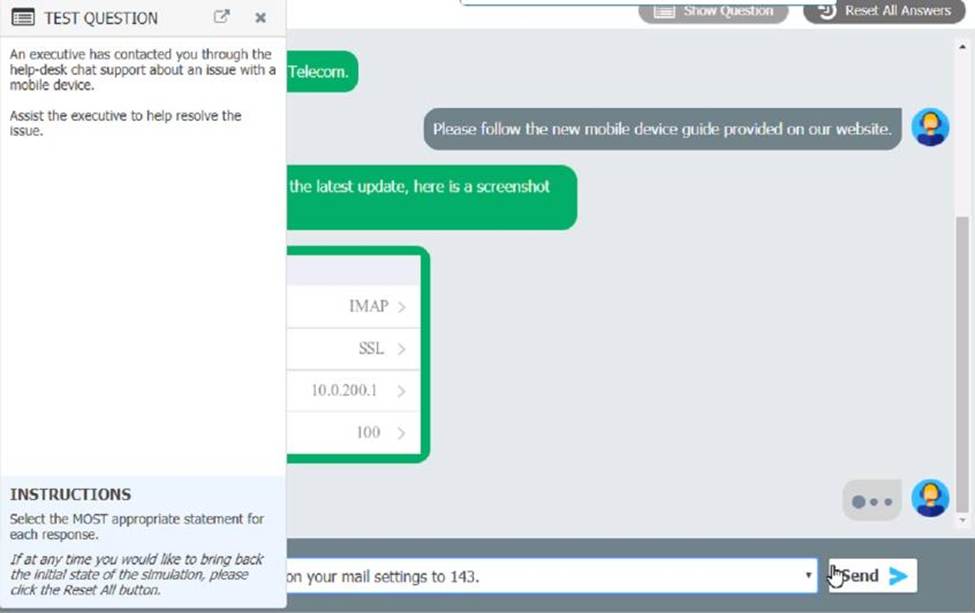
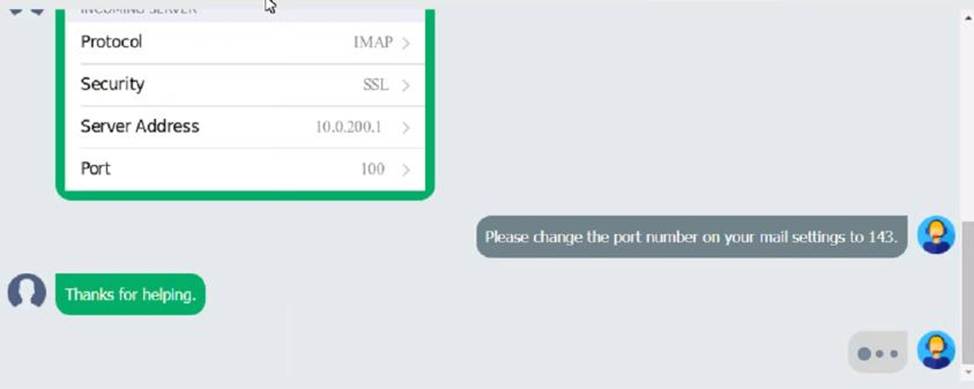
Which of the following should be done NEXT?
- A . Educate the user on the solution that was performed.
- B . Tell the user to take time to fix it themselves next time.
- C . Close the ticket out.
- D . Send an email to Telecom to inform them of the Issue and prevent reoccurrence.
A vendor provided installation software on a DVD-ROM. The software is not available to download on the vendor’s website. The technician needs to install the software on several laptops that do not have an optical disc drive. The laptops are connected to the corporate network but are physically located at remote sites.
Which of the following is the best installation method for the technician to use?
- A . Use a computer that has an optical disc drive to create an ISO file from the DVD-ROM, store the ISO file on the file server, connect remotely to each laptop, and install the software on each laptop using the ISO stored on the file server.
- B . Locate an external USB DVD-ROM optical disc drive, insert the DVD-ROM from the vendor into the drive, and install the software from the USB DVD-ROM optical disc drive.
- C . Use a computer that has an optical disc drive to create an ISO file from the DVD-ROM, copy the ISO file to a USB flash drive, and install the software from the USB flash drive.
- D . Locate an ISO file of the software from a website unrelated to the vendor, store the ISO file on the file server, connect remotely to each laptop, and install the software on each laptop using the ISO stored on the file server.
A
Explanation:
Comprehensive and Detailed In-Depth
The best method is to create an ISO file from the DVD and store it on a file server, allowing remote installations across multiple devices.
B. Use an external USB DVD-ROM C Not practical for remote installations.
C. Copy ISO to a USB flash drive C Requires physically transferring the USB to each laptop.
D. Download an ISO from an unrelated website C Unsafe and violates security best practices.
Reference: CompTIA A+ 220-1102, Objective 3.3 C Installation Methods
A department has the following technical requirements for a new application:

The company plans to upgrade from a 32-bit Windows OS to a 64-bit OS.
Which of the following will the company be able to fully take advantage of after the upgrade?
- A . CPU
- B . Hard drive
- C . RAM
- D . Touch screen
C
Explanation:
https://www.makeuseof.com/tag/difference-32-bit-64-bit-windows/
After upgrading from a 32-bit Windows OS to a 64-bit OS, the company will be able to fully take advantage of the RAM of the computer. This is because a 64-bit operating system is able to use larger amounts of RAM compared to a 32-bit operating system, which may benefit the system’s overall performance if it has more than 4GB of RAM installed
