Practice Free 200-301 Exam Online Questions
Refer to the exhibit.
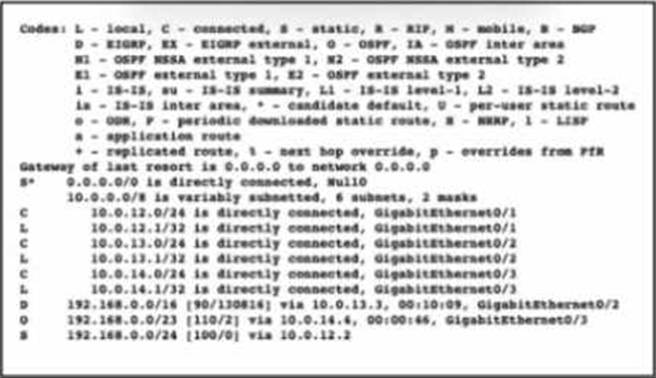
Which interface is chosen to forward traffic to the host at 192.168.0.55?
- A . GigabitEthernet0
- B . GigabitEthernet0/1
- C . Null0
- D . GigabitEthernet0/3
Which two minimum parameters must be configured on an active interface to enable OSPFv2 to operate? (Choose two)
- A . OSPF area
- B . OSPF MD5 authentication key
- C . iPv6 address
- D . OSPf process ID
- E . OSPf stub flag
Refer to the exhibit.
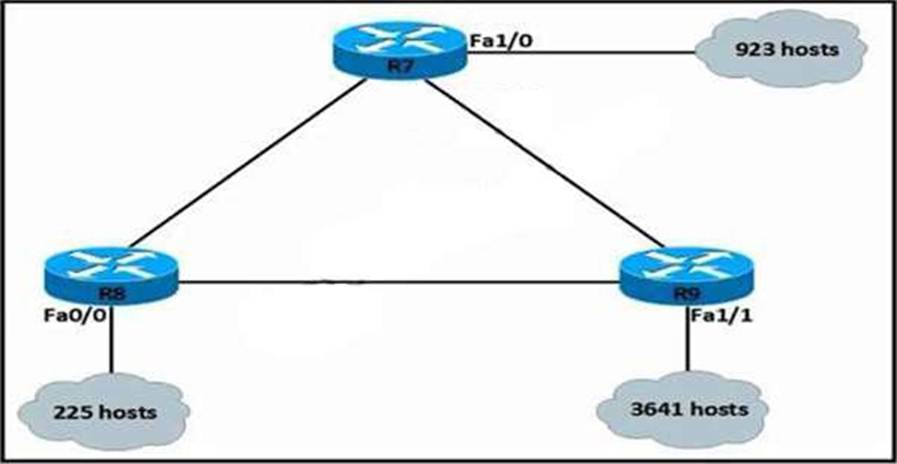
An IP subnet must be configured on each router that provides enough addresses for the number of assigned hosts and anticipates no more than 10% growth for now hosts.
Which configuration script must be used?
- A . R7#
configure terminal
interface Fa 1/0
ip address 10.1.56.1 255.255.252.0
no shutdown
R8#
configure terminal
interface Fa0/0
ip address 10.9.32.1 255.255.255.0
no shutdown
R9#
configure terminal
interface Fa 1/1
ip address 10.23.96.1 255.255.240.0
no shutdown - B . R7#
configure terminal
interface Fa1/0
ip address 10.1.56.1 255.255.248.0
no shutdown
R8#
configure terminal
interface Fa0/0
ip address 10.9.32.1 255.255.254.0
no shutdown
R9#
configure terminal
interface Fa1/1
ip address 10.23.96.1 255.255.248.0
no shutdown - C . R7#
configure terminal
interface Fa1/0
ip address 10.1.56.1 255.255.240.0
no shutdown
R8#
configure terminal
interface Fa0/0
ip address 10.9.32.1 255.255.224.0
no shutdown
R9#
configure terminal
interface Fa1/1
ip address 10.23.96.1 255.255.192.0
no shutdown - D . R7# configure terminal
interface Fa1/0
ip address 10.1.56.1 255.255.192.0
no shutdown
R8#
configure terminal
interface Fa0/0
ip address 10.9.32.1 255.255.224.0
no shutdown
R9#
configure terminal
interface Fa 1/1
ip address 10.23.96.1 255.255.128.0
no shutdown
Refer to the exhibit.
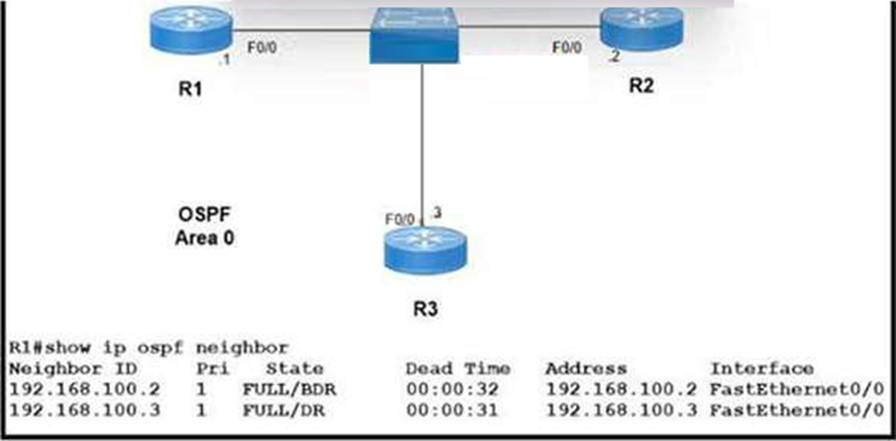
Which two configurations must the engineer apply on this network so that R1 becomes the DR? (Choose two.)
- A . R1(config)#router ospf 1
R1(config-router)#router-id 192.168.100.1 - B . R1(config)#interface fastethernet 0/0
R1(config-if)#ip ospf priority 200 - C . R3(config)#interface fastethernet 0/0
R3(config-if)#ip ospf priority 0 - D . R1(config)#interface fastethernet 0/0
R1(config-if)#ip ospf priority 0 - E . R3(config)#interface fastethernet 0/0
R3(config-if)#ip ospf priority 200
Refer to the exhibit.

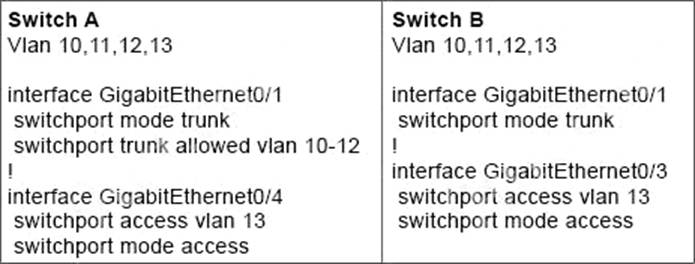
A network engineer must configured communication between PC A and the File Server.
To prevent interruption for any other communications, which command must be configured?
- A . Switch trunk allowed vlan 12
- B . Switchport trunk allowed vlan none
- C . Switchport trunk allowed vlan add 13
- D . Switchport trunk allowed vlan remove 10-11
Refer to the exhibit.


A network engineer must configured communication between PC A and the File Server.
To prevent interruption for any other communications, which command must be configured?
- A . Switch trunk allowed vlan 12
- B . Switchport trunk allowed vlan none
- C . Switchport trunk allowed vlan add 13
- D . Switchport trunk allowed vlan remove 10-11
What happens when a switch receives a frame with a destination MAC address that recently aged out?
- A . The switch references the MAC address aging table for historical addresses on the port that received the frame.
- B . The switch floods the frame to all ports in all VLANs except the port that received the frame
- C . The switch drops the frame and learns the destination MAC address again from the port that received the frame
- D . The switch floods the frame to all ports in the VLAN except the port that received the frame.
It work security team noticed that an increasing number of employees are becoming victims of phishing attacks.
Which security program should be implemented to mitigate the problem?
- A . email system patches
- B . physical access control
- C . software firewall enabled on all PCs
- D . user awareness training
It work security team noticed that an increasing number of employees are becoming victims of phishing attacks.
Which security program should be implemented to mitigate the problem?
- A . email system patches
- B . physical access control
- C . software firewall enabled on all PCs
- D . user awareness training
It work security team noticed that an increasing number of employees are becoming victims of phishing attacks.
Which security program should be implemented to mitigate the problem?
- A . email system patches
- B . physical access control
- C . software firewall enabled on all PCs
- D . user awareness training
