Practice Free 200-301 Exam Online Questions
A Cisco engineer must configure a single switch interface to meet these requirements
• accept untagged frames and place them in VLAN 20
• accept tagged frames in VLAN 30 when CDP detects a Cisco IP phone.
Which command set must the engineer apply?
- A . switchport mode dynamic desirable
switchport access vlan 20
switchport trunk allowed vlan 30
switchport voice vlan 30 - B . switchport mode dynamic auto
switchport trunk native vlan 20
switchport trunk allowed vlan 30
switchport voice vlan 30 - C . switchport mode access
switchport access vlan 20
switchport voice vlan 30 - D . switchport mode trunk
switchport access vlan 20
switchport voice vlan 30
What is the purpose of the ip address dhcp command?
- A . to configure an Interface as a DHCP server
- B . to configure an interface as a DHCP helper
- C . to configure an interface as a DHCP relay
- D . to configure an interface as a DHCP client
Refer to the exhibit.
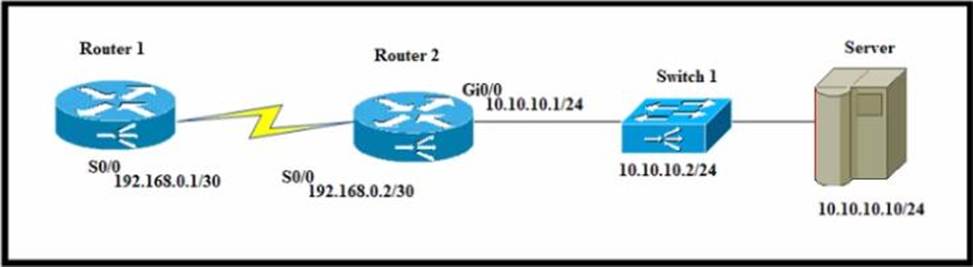
A network engineer must configure router R1 with a host route to the server.
Which command must the engineer configure?
- A . R1(config)#lp route 10.10.10.0 255.255.255.0 192.168.0.2
- B . R1(Config)#lp route 10.10.10.10 265.255.255.255 192 168.0.2
- C . R1(config)#ip route 192.168.0.2 255.255.255.255 10.10.10.10
- D . R1(config)3|p route 0.0.0.0 0.0 0.0 192 168.0.2
If a switch port receives a new frame while it is actively transmitting a previous frame, how does it process the frames?
- A . The new frame is delivered first, the previous frame is dropped, and a retransmission request is sent.
- B . The previous frame is delivered, the new frame is dropped, and a retransmission request is sent.
- C . The new frame is placed in a queue for transmission after the previous frame.
- D . The two frames are processed and delivered at the same time.
What is the definition of backdoor malware?
- A . malicious code that is installed onto a computer to allow access by an unauthorized user
- B . malicious code with the main purpose of downloading other malicious code
- C . malicious program that is used to launch other malicious programs
- D . malicious code that infects a user machine and then uses that machine to send spam
What is an advantage of Cisco DNA Center versus traditional campus device management?
- A . It supports numerous extensibility options including cross-domain adapters and third-party SDKs.
- B . It supports high availability for management functions when operating in cluster mode.
- C . It enables easy autodiscovery of network elements m a brownfield deployment.
- D . It is designed primarily to provide network assurance.
Which syslog severity level is considered the most severe and results in the system being considered unusable?
- A . Alert
- B . Error
- C . Emergency
- D . Critical
Refer to the exhibit.

What is the effect of this configuration?
- A . All ARP packets are dropped by the switch
- B . Egress traffic is passed only if the destination is a DHCP server.
- C . All ingress and egress traffic is dropped because the interface is untrusted
- D . The switch discard all ingress ARP traffic with invalid MAC-to-IP address bindings.
An engineer observes high usage on the 2.4GHz channels and lower usage on the 5GHz channels.
What must be configured to allow clients to preferentially use 5GH2 access points?
- A . Re- Anchor Roamed Clients
- B . 11ac MU-MIMO
- C . OEAP Split Tunnel
- D . Client Band Select