Practice Free D-PCR-DY-01 Exam Online Questions
What is the primary benefit of using Dell APEX Protection Storage All Flash for Cyber Recovery?
- A . Lower initial cost
- B . Increased storage capacity
- C . Compatibility with all hypervisors
- D . Faster read and restore times
D
Explanation:
Dell APEX Protection Storage All Flash provides faster read and restore times, which significantly enhances Cyber Recovery performance by reducing recovery time objectives (RTOs).
What is a pre-requisite for performing Automated Recovery of Dell PowerProtect Data Manager?
- A . vCenter hosting PowerProtect Data Manager is added to Dell PowerProtect Cyber Recovery.
- B . Manual Snapshot of PowerProtect Data Manager on vCenter.
- C . Create the DDBoost users on the PowerProtect Data Manager.
- D . Keep the same password on Vault PowerProtect Data Manager as production PowerProtect Data Manager.
A
Explanation:
vCenter hosting PowerProtect Data Manager must be added to Dell PowerProtect Cyber Recovery to enable automated recovery processes. This integration allows Cyber Recovery to manage and automate the recovery workflows directly through the virtual infrastructure.
A Dell PowerProtect Cyber Recovery administrator has noticed multiple file corruption events and suspects some potential harmful situations in their environment.
Which error log level can be used to analyze the situation?
- A . DEBUG
- B . INFO
- C . ERROR
- D . WARNING
A
Explanation:
The DEBUG log level provides the most detailed information, allowing the administrator to analyze and troubleshoot file corruption events and potential harmful situations thoroughly.
An IT manager needs to rerun a previously generated Dell PowerProtect Cyber Recovery report to verify the job activities for a specific period. They want to ensure that report includes the latest data.
What action should the IT manager take to rerun the report?
- A . Generate a new report using the Report Wizard
- B . Edit the report schedule
- C . Select ‘Run Now* in the Generated Reports pane
- D . Clone the report schedule
A
Explanation:
To ensure the report includes the latest data, the IT manager should generate a new report using the Report Wizard, which reruns the report query and produces an updated output.
Which common cyber-attack overwhelms the resources of the system with excessive requests that consume all the resources to bring it down?
- A . Ad ware
- B . Unauthorized Currency Mining
- C . Banking Trojan
- D . Ransomware
- E . Denial of Service
E
Explanation:
A Denial of Service (DoS) attack overwhelms system resources by flooding it with excessive requests, exhausting capacity and causing service disruption.
Which describes the best use of Dell PowerProtect Data Domain in an isolated clean room?
- A . Stand by for production Data Domain
- B . To extend recoverability of the immutable copies for up to 45 days
- C . long running analyze jobs from vault Data Domain
- D . Target for alternate recovery
D
Explanation:
Using Dell PowerProtect Data Domain in an isolated clean room serves as a secure target for alternate recovery, providing a protected environment to restore data if the primary vault is compromised.
Which three statements are true when performing a Dell Avamar Automated Recovery? (Choose three.)
- A . Run lockbox_restore.pl script to recover MCUser and GSAN accounts.
- B . Vault PowerProtect Data Domain Storage ID in Dell PowerProtect Cyber Recovery must be known to obtain the latest checkpoint.
- C . Avamar System ID must be known for Avamar checkpoint restore.
- D . Avamar version, build, and FQDN must match the production.
- E . DDBoost username, role, and password on Vault Data Domain must match the production.
Which two server configurations are valid for the CyberSense virtual appliance? (Choose two.)
- A . Small – 16 CPU, 128 GB Memory
- B . X-Large – 48 CPU, 512 GB Memory
- C . Large – 32 CPU, 384 GB Memory
- D . Medium – 20 CPU, 192 GB Memory
A C
Explanation:
The valid CyberSense virtual appliance configurations include the Small size with 16 CPUs and 128 GB memory, and the Large size with 32 CPUs and 384 GB memory, matching documented deployment specifications.
Which feature of the Dell PowerProtect Cyber Recovery in collaboration with VMware ESXi 8.0 environment offers the capacity of 220 TB?
- A . ESX hypervisor with customized settings
- B . Dell PowerEdge hardware with all-flash media on a supported Hyper-V
- C . KVM with hybrid media built on Dell hardware
- D . Dell PowerEdge hardware with all-flash media
D
Explanation:
Dell PowerEdge hardware with all-flash media offers the high-capacity storage option of 220 TB when deployed with Dell PowerProtect Cyber Recovery in a VMware ESXi 8.0 environment.
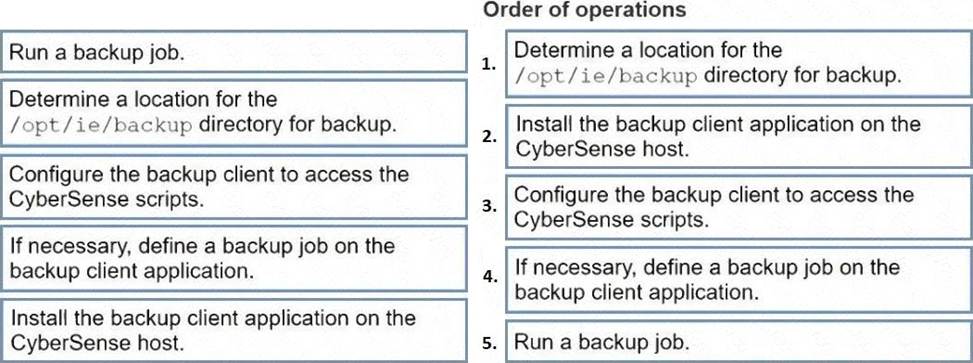
DRAG DROP
Put the following steps in the correct order to back up the Index Engines CyberSense configuration files: