Practice Free FCSS_SASE_AD-25 Exam Online Questions
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
- A . It provides end-to-end network visibility from all the FortiSASE security PoPs to a specific SaaS application.
- B . It gathers all the vulnerability information from all the FortiClient endpoints.
- C . It is used for performing device compliance checks on endpoints.
- D . It monitors the FortiSASE POP health based on ping probes.
A
Explanation:
The Digital Experience Monitor (DEM) in FortiSASE measures and monitors network performance from the FortiSASE Points of Presence (PoPs) to specific SaaS or cloud applications, helping identify and troubleshoot performance issues across the service path.
Which information does FortiSASE use to bring network lockdown into effect on an endpoint?
- A . Zero-day malware detection on endpoint
- B . The number of critical vulnerabilities detected on the endpoint
- C . The security posture of the endpoint based on ZTNA tags
- D . The connection status of the tunnel to FortiSASE
C
Explanation:
FortiSASE uses ZTNA tags to assess the endpoint’s security posture. If the posture is non-compliant based on predefined rules, FortiSASE enforces network lockdown to restrict access accordingly.
What are two benefits of deploying FortiSASE with FortiGate ZTNA access proxy? (Choose two.)
- A . It offers data center redundancy.
- B . The on-premises FortiGate performs a device posture check.
- C . It is ideal for latency-sensitive applications.
- D . It supports both agentless ZTNA and agent-based ZTNA.
C,D
Explanation:
Deploying FortiSASE with FortiGate ZTNA access proxy enables efficient access to private applications with reduced latency and supports both agentless and agent-based ZTNA methods for flexible access control.
Which secure internet access (SIA) use case minimizes individual endpoint configuration?
- A . Agentless remote user internet access
- B . Site-based remote user internet access
- C . SIA using ZTNA
- D . SIA for FortiClient agent remote users
B
Explanation:
Site-based remote user internet access minimizes individual endpoint configuration by routing user traffic through a centralized FortiSASE connection point (such as a FortiAP or FortiGate), rather than requiring each device to be individually configured with the FortiClient agent.
Which authentication method overrides any other previously configured user authentication on FortiSASE?
- A . MFA
- B . Local
- C . RADIUS
- D . SSO
D
Explanation:
Single Sign-On (SSO) overrides any other previously configured user authentication method on FortiSASE, taking precedence for user authentication.
Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
- A . For user access control to FortiSASE
- B . For allocation and assignment of unique IP addresses to remote users
- C . For regulatory compliance
- D . For isolation and identification
Your FortiSASE customer has a small branch office in which ten users will be using their personal laptops and mobile devices to access the internet.
Which deployment should they use to secure their internet access with minimal configuration?
- A . Deploy FortiGate as a LAN extension to secure internet access.
- B . Deploy FortiAP to secure internet access.
- C . Deploy FortiClient endpoint agent to secure internet access.
- D . Deploy SD-WAN on-ramp to secure internet access.
B
Explanation:
Deploying FortiAP enables secure internet access for unmanaged personal devices in small branch offices with minimal configuration by automatically directing traffic through FortiSASE, eliminating the need for endpoint installation or complex setup.
Refer to the exhibit.
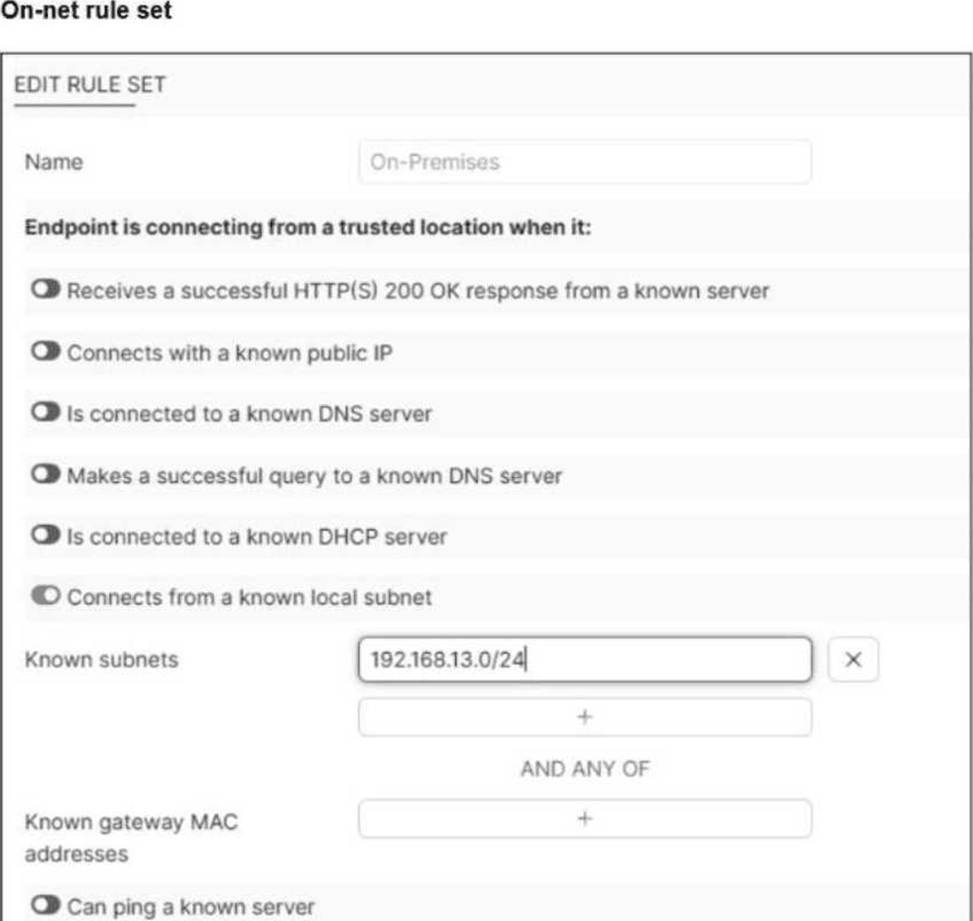
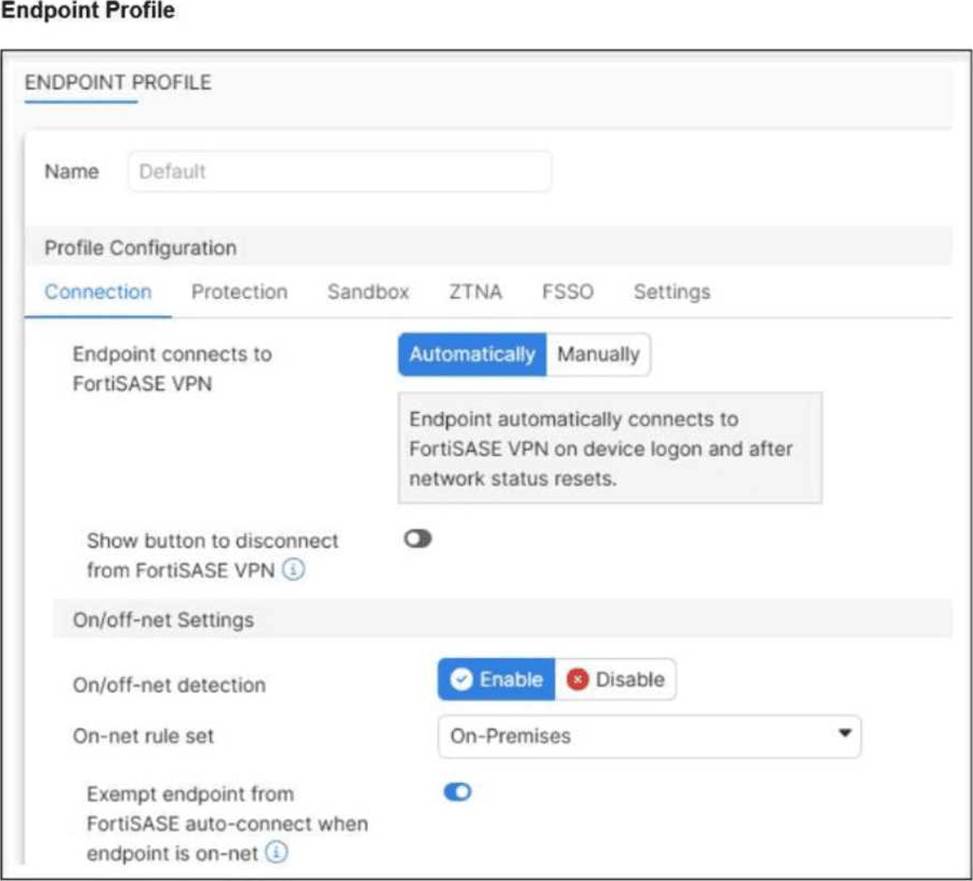
An endpoint is assigned an IP address of 192.168.13.101/24.
Which action will be run on the endpoint?
- A . The endpoint will be exempted from auto-connect to the FortiSASE tunnel.
- B . The endpoint will automatically connect to the FortiSASE tunnel.
- C . The endpoint will be detected as off-net.
- D . The endpoint will be able to bypass the on-net rule because it is connecting from a known subnet.
A
Explanation:
The FortiClient Administration Guide states that on-net rules determine when an endpoint is in a trusted location. If the endpoint matches the configured subnet, the client is considered on-net, and therefore bypasses auto-connect.
“Device registration and on-net status information for a device that is running FortiClient appears only on the FortiGate that applies the FortiClient profile to that device.”
Since 192.168.13.101 falls inside the trusted subnet 192.168.13.0/24, the endpoint is treated as on-net → it will be exempted from auto-connect.
Refer to the exhibits.
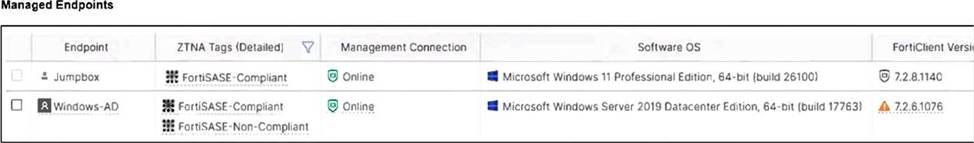
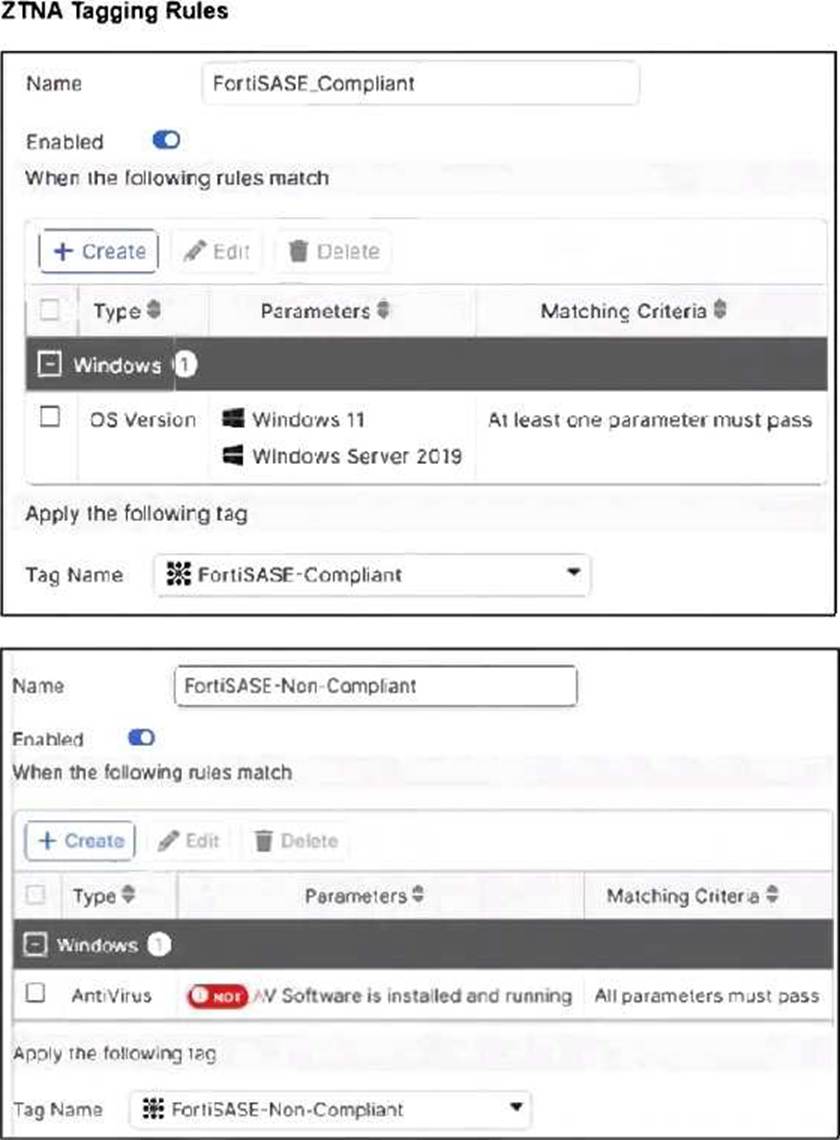
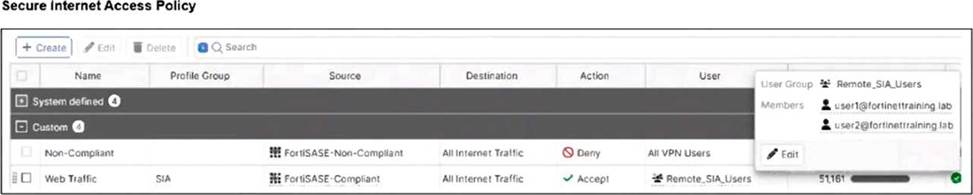
Jumpbox and Windows-AD are endpoints from the same remote location. Jumpbox can access the internet through FortiSASE, while Windows-AD can no longer access the internet.
Based on the information in the exhibits, which reason explains the outage on Windows-AD?
- A . Windows-AD is excluded from FortiSASE management.
- B . The FortiClient version installed on Windows AD does not match the expected version on FortiSASE.
- C . The device posture for Windows-AD has changed.
- D . The remote VPN user on Windows-AD no longer matches any VPN policy.
C
Explanation:
The Windows-AD endpoint now has both "FortiSASE-Compliant" and "FortiSASE-Non-Compliant" tags due to failing the antivirus software check. As a result, the Secure Internet Access Policy matches the "Non-Compliant" rule, which is set to Deny, causing the device to lose internet access.
A company must provide access to a web server through FortiSASE secure private access for contractors.
What is the recommended method to provide access?
- A . Configure a TCP access proxy forwarding rule and push it to the contractor FortiClient endpoint.
- B . Update the DNS records on the endpoint to access private applications.
- C . Publish the web server URL on a bookmark portal and share it with contractors.
- D . Update the PAC file with the web server URL and share it with contractors.
C
Explanation:
The bookmark portal is the recommended method for providing contractors access to private web applications through FortiSASE Secure Private Access, as it offers a user-friendly, secure, and controlled access mechanism without requiring full network connectivity.
