Practice Free FCSS_SDW_AR-7.4 Exam Online Questions
Refer to the exhibits.
Exhibit A

Exhibit B
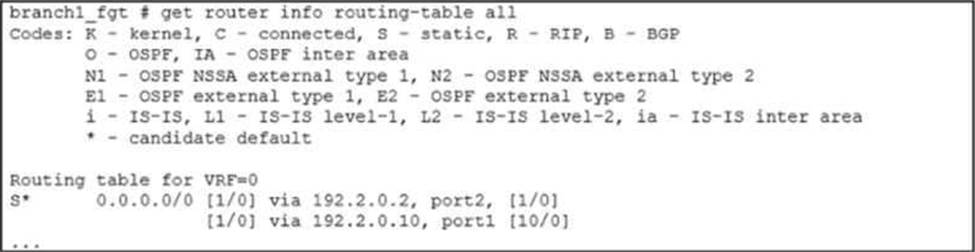
Exhibit A shows the source NAT (SNAT) global setting and exhibit B shows the routing table on FortiGate.
Based on the exhibits, which two actions does FortiGate perform on existing sessions established over port2, if the administrator increases the static route priority on port2 to 20? (Choose two.)
- A . FortiGate flags the sessions as dirty.
- B . FortiGate continues routing the sessions with no SNAT, over port2.
- C . FortiGate performs a route lookup for the original traffic only.
- D . FortiGate updates the gateway information of the sessions with SNAT so that they use port1 instead of port2.
Which action fortigate performs on the traffic that is subject to a per-IP traffic shaper of 10 Mbps?
- A . FortiGate applies traffic shaping to the original traffic direction only.
- B . FortiGate shares 10 Mbps of bandwidth equally among all source IP addresses.
- C . Fortigate limits each source ip address to a maximum bandwidth of 10 Mbps.
- D . FortiGate guarantees a minimum of 10 Mbps of bandwidth to each source IP address.
In the default SD-WAN minimum configuration, which two statements are correct when traffic matches the default implicit SD-WAN rule? (Choose two )
- A . Traffic has matched none of the FortiGate policy routes.
- B . Matched traffic failed RPF and was caught by the rule.
- C . The FIB lookup resolved interface was the SD-WAN interface.
- D . An absolute SD-WAN rule was defined and matched traffic.
Which components make up the secure SD-WAN solution?
- A . Application, antivirus, and URL, and SSL inspection
- B . Datacenter, branch offices, and public cloud
- C . FortiGate, FortiManager, FortiAnalyzer, and FortiDeploy
- D . Telephone, ISDN, and telecom network.
Refer to the exhibit.
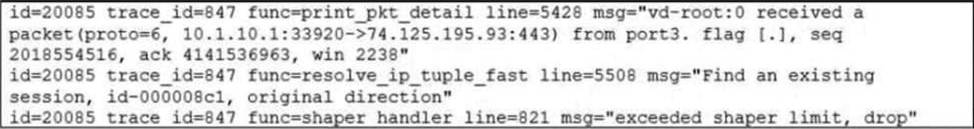
Which conclusion about the packet debug flow output is correct?
- A . The original traffic exceeded the maximum packets per second of the outgoing interface, and the packet was dropped.
- B . The reply traffic exceeded the maximum bandwidth configured in the traffic shaper, and the packet was dropped.
- C . The original traffic exceeded the maximum bandwidth of the outgoing interface, and the packet was dropped.
- D . The original traffic exceeded the maximum bandwidth configured in the traffic shaper, and the packet was dropped.
Refer to the Exhibits:
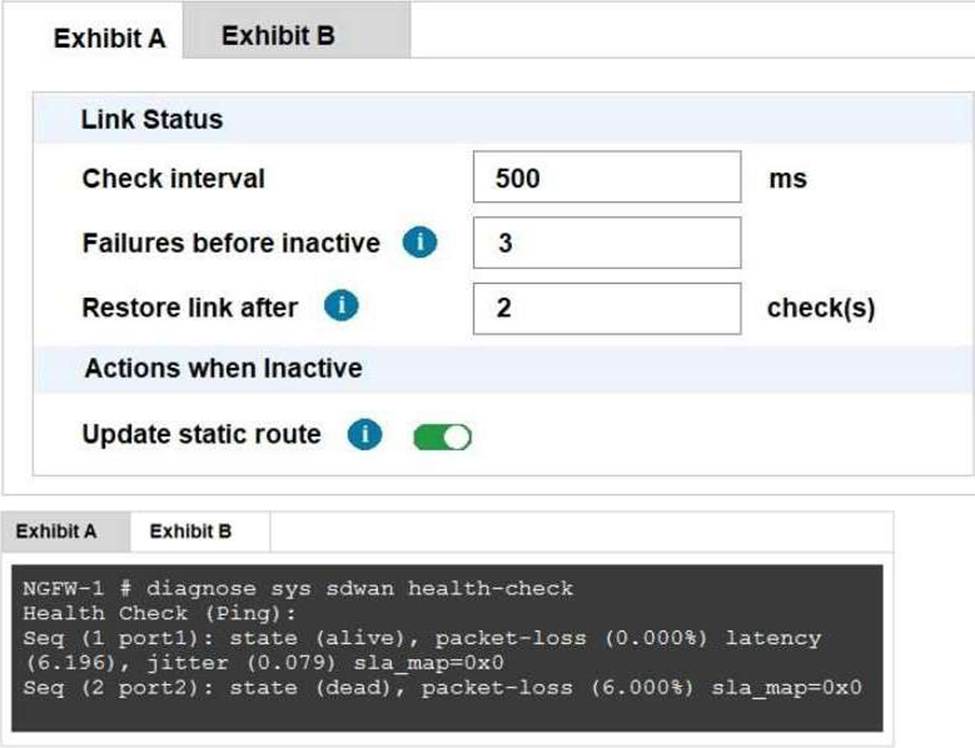
Exhibit A, which shows the SD-WAN performance SLA and exhibit B shows the health of the participating SD-WAN members.
Based on the exhibits, which statement is correct?
- A . The dead member interface stays unavailable until an administrator manually brings the interface back.
- B . Port2 needs to wait 500 milliseconds to change the status from alive to dead.
- C . Static routes using port2 are active in the routing table.
- D . FortiGate has not received three consecutive requests from the SLA server configured for port2.
The administrator uses the FortiManager SD-WAN overlay template to prepare an SD-WAN deployment. With information provided through the SD-WAN overlay template wizard, FortiManager creates templates ready to install on spoke and hub devices.
Select three templates created by the SD-WAN overlay template for a spoke device. (Choose three.)
- A . System template
- B . BGP template
- C . IPsec tunnel template
- D . CLI template
- E . Overlay template
BCD
Explanation:
https://docs.fortinet.com/document/fortimanager/7.4.2/administration-guide/28292/objects-and-templates-created-by-the-sd-wan-overlay-template
Which two statements describe how IPsec phase 1 main mode id different from aggressive mode when performing IKE negotiation? (Choose two.)
- A . A peer ID is included in the first packet from the initiator, along with suggested security policies.
- B . XAuth is enabled as an additional level of authentication, which requires a username and password.
- C . Three packets are exchanged between an initiator and a responder instead of six packets.
- D . The use of Diffie Hellman keys is limited by the responder and needs initiator acceptance.
What does enabling the exchange-interface-ip setting enable FortiGate devices to exchange?
- A . The gateway address of their IPsec interfaces
- B . The tunnel ID of their IPsec interfaces
- C . The IP address of their IPsec interfaces
- D . The name of their IPsec interfaces
What are two benefits of using forward error correction (FEC) in IPsec VPNs? (Choose two.)
- A . FEC supports hardware ofloading.
- B . FEC improves reliability of noisy links.
- C . FEC transmits parity packets that can be used to reconstruct packet loss.
- D . FEC can leverage multiple IPsec tunnels for parity packets transmission.
