Practice Free FCP_FGT_AD-7.6 Exam Online Questions
Which three pieces of information does FortiGate use to identify the hostname of the SSL server when SSL certificate inspection is enabled? (Choose three.)
- A . The subject field in the server certificate
- B . The serial number in the server certificate
- C . The server name indication (SNI) extension in the client hello message
- D . The subject alternative name (SAN) field in the server certificate
- E . The host field in the HTTP header
A,C,D
Explanation:
When SSL certificate inspection is enabled, FortiGate uses the following three pieces of information to identify the hostname of the SSL server:
An administrator has configured the following settings:
config system settings
set ses-denied-traffic enable
end
config system global
set block-session-timer 30
end
What are the two results of this configuration? (Choose two.)
- A . Device detection on all interfaces is enforced for 30 seconds.
- B . Denied users are blocked for 30 seconds.
- C . The number of logs generated by denied traffic is reduced.
- D . A session for denied traffic is created.
C,D
Explanation:
The timer config any way is by seconds.
ses-denied-traffic Enable/disable including denied session in the session table. block-session-timer
Duration in seconds for blocked sessions (1 – 300 sec (5 minutes), default = 30).
C. The number of logs generated by denied traffic is reduced.
D. A session for denied traffic is created.
During the session, if a security profile detects a violation, FortiGate records the attack log immediately. To reduce the number of log messages generated and improve performance, you can enable a session table entry of dropped traffic. This creates the denied session in the session table and, if the session is denied, all packets of that session are also denied. This ensures that FortiGate does not have to do a policy lookup for each new packet matching the denied session, which reduces CPU usage and log generation. This option is in the CLI, and is called ses-denied-traffic. You can also set the duration for block sessions. This determines how long a session will be kept in the session table by setting block-sessiontimer in the CLI. By default, it is set to 30 seconds.
Reference and download study guide:
https://community.fortinet.com/t5/FortiGate/Technical-Tip-How-to-enable-denied-session-to-be-added-into-the/ta-p/195478
Refer to the exhibit.
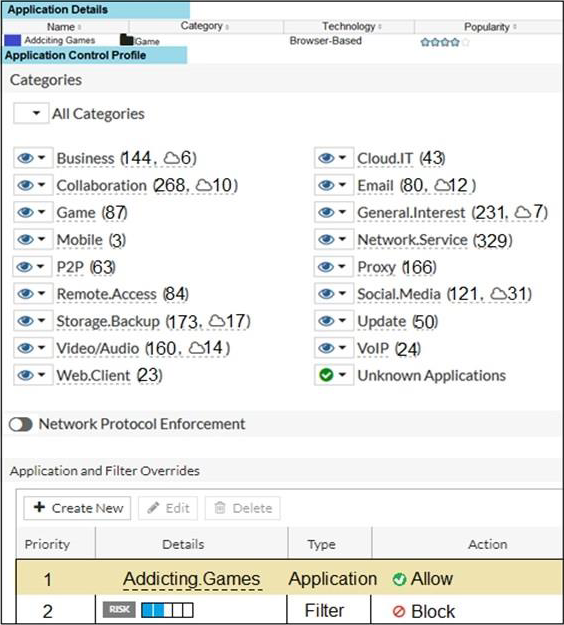
A user located behind the FortiGate device is trying to go to http://www.addictinggames.com (Addicting.Games). The exhibit shows the application detains and application control profile.
Based on this configuration, which statement is true?
- A . Addicting.Games will be blocked, based on the Filter Overrides configuration.
- B . Addicting.Games will be allowed only if the Filter Overrides action is set to Learn.
- C . Addicting.Games will be allowed, based on the Categories configuration.
- D . Addicting.Games will be allowed, based on the Application Overrides configuration.
D
Explanation:
Addicting.Games will be allowed, based on the Application Overrides configuration.
Based on the Scan order. Application and Filter overrides>>Category.
Application and Filter overrides follows the same rules as firewall policy. Application override will be considered first.
Refer to the exhibit.
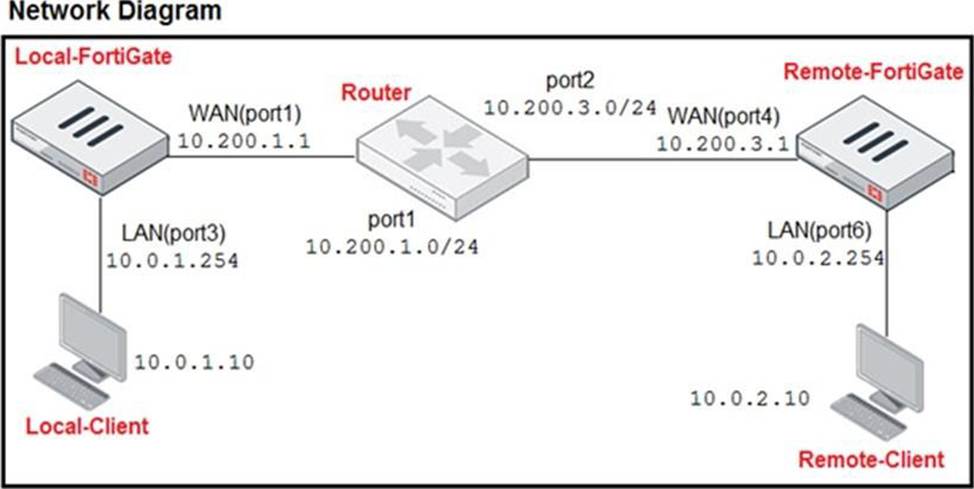
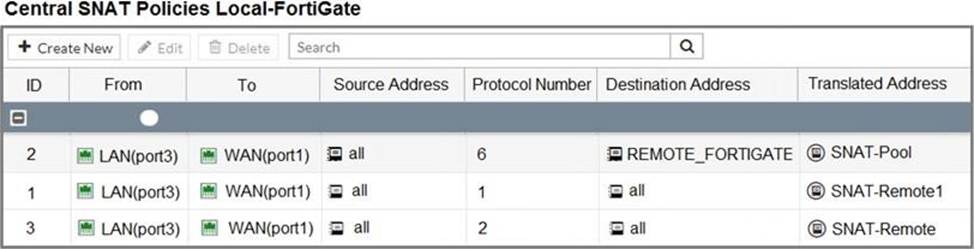
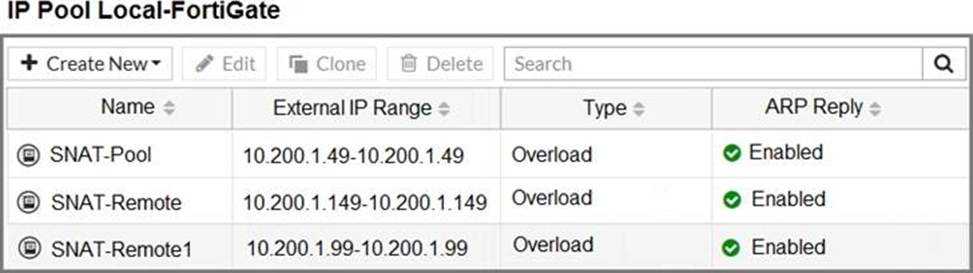
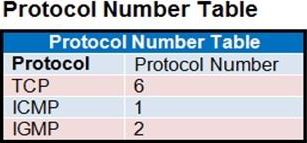
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
- A . 10.200.1.149
- B . 10.200.1.1
- C . 10.200.1.49
- D . 10.200.1.99
D
Explanation:
It’s D because of the protocol number.
Ping is ICMP protocol – protocol number = 1
=> SNAT policy ID 1 is policy that used.
=> Translated address is "SNAT-Remote1" that 10.200.1.99
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
- A . VLAN interface
- B . Software Switch interface
- C . Aggregate interface
- D . Redundant interface
C
Explanation:
Link aggregation (IEEE 802.3ad) enables you to bind two or more physical interfaces together to form an aggregated (combined) link. This new link has the bandwidth of all the links combined. If a link in the group fails, traffic is transferred automatically to the remaining interfaces with the only noticeable effect being a reduced bandwidth.
To increase network bandwidth and provide redundancy, an administrator can use an Aggregate Interface (also known as Link Aggregation or Port Channel). This interface type allows multiple physical interfaces to be combined into a single logical interface, providing increased bandwidth and fault tolerance. This logical interface appears as a single interface to the rest of the network, and it distributes traffic across the member interfaces.
When configuring firewall policies which of the following is true regarding the policy ID?
- A . It is mandatory to provide a policy ID while creating a firewall policy regardless of GUI or CLI.
- B . A firewall policy ID identifies the order of policy execution in firewall policies.
- C . You can create a policy in CLI with policy ID 0.
- D . A policy ID cannot be edited once a policy is created.
D
Explanation:
Once a firewall policy is created, its policy ID is fixed and cannot be changed; this ID uniquely identifies the policy within the FortiGate configuration.
Which statement about video filtering on FortiGate is true?
- A . Full SSL Inspection is not required.
- B . It is available only on a proxy-based firewall policy.
- C . It inspects video files hosted on file sharing services.
- D . Video filtering FortiGuard categories are based on web filter FortiGuard categories.
B
Explanation:
B. It is available only on a proxy-based firewall policy.
Video filtering on FortiGate is available only on a proxy-based firewall policy. This means that in order to filter video content, the traffic must be routed through a proxy-based firewall policy where the FortiGate can inspect and filter the video content based on its policies.
To apply the video filter profile, proxy-based firewall polices currently allow you to enable the video filter profile. You must enable full SSL inspection on the firewall policy.
An administrator wanted to configure an IPS sensor to block traffic that triggers a signature set number of times during a specific time period.
How can the administrator achieve the objective?
- A . Use IPS group signatures, set rate-mode 60.
- B . Use IPS packet logging option with periodical filter option.
- C . Use IPS filter, rate-mode periodical option.
- D . Use IPS filter, rate-mode periodical option.
C
Explanation:
The IPS filter with the rate-mode set to "periodical" allows the administrator to block traffic that triggers a signature a specified number of times within a defined time period, meeting the requirement.
Which two statements are true about the Security Fabric rating? (Choose two.)
- A . The Security Fabric rating is a free service that comes bundled with all FortiGate devices.
- B . Many of the security issues can be fixed immediately by clicking Apply where available.
- C . The Security Fabric rating must be run on the root FortiGate device in the Security Fabric.
- D . It provides executive summaries of the four largest areas of security focus.
B,C
Explanation:
B. Many of the security issues can be fixed immediately by clicking Apply where available: This statement is true. The Security Fabric rating often identifies security issues that can be resolved immediately by clicking "Apply" where available, making it a valuable tool for quickly addressing security concerns.
C. The Security Fabric rating must be run on the root FortiGate device in the Security Fabric: This statement is also true. The Security Fabric rating must be run on the root FortiGate device in the Security Fabric to provide an overall security rating and analysis of the Security Fabric.
On checks that support Easy Apply, you can run the remediation on all the associated VDOMs.
To view the complete network, you must access the topology views on the root FortiGate in the Security
Fabric.
Incorrect:
An administrator is configuring an IPsec VPN between site A and site B. The Remote Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
- A . 192.168.2.0/24
- B . 192.168.0.0/8
- C . 192.168.1.0/24
- D . 192.168.3.0/24
A
Explanation:
