Practice Free NSE8_812 Exam Online Questions
You are troubleshooting a FortiMail Cloud service integrated with Office 365 where outgoing emails are not reaching the recipients’ mail What are two possible reasons for this problem? (Choose two.)
- A . The FortiMail access control rule to relay from Office 365 servers FQDN is missing.
- B . The FortiMail DKIM key was not set using the Auto Generation option.
- C . The FortiMail access control rules to relay from Office 365 servers public IPs are missing.
- D . A Mail Flow connector from the Exchange Admin Center has not been set properly to the FortiMail Cloud FQDN.
AC
Explanation:
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG.
Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener.
In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
- A . disable on ICL trunks
- B . enable on ICL trunks
- C . disable on the ISL and FortiLink trunks
- D . enable on the ISL and FortiLink trunks
BC
Explanation:
https://docs.fortinet.com/document/fortiswitch/7.0.8/devices-managed-by-fortios/801194/deploying-mclag-topologies
Refer to the exhibits.
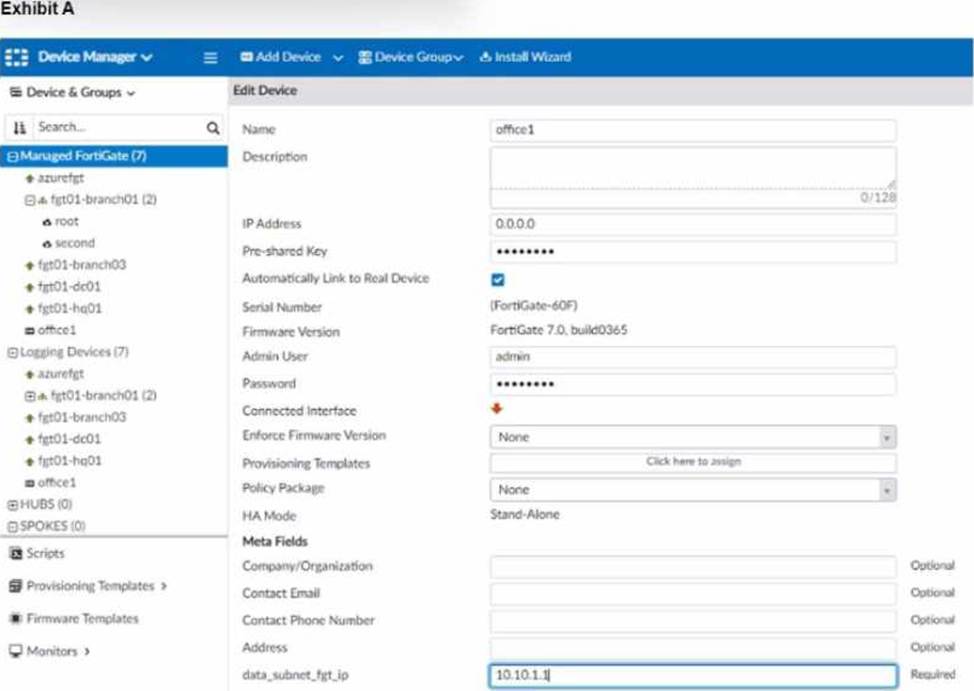
The exhibit shows a FortiGate model device that will be used for zero touch provisioning and a CLI Template.
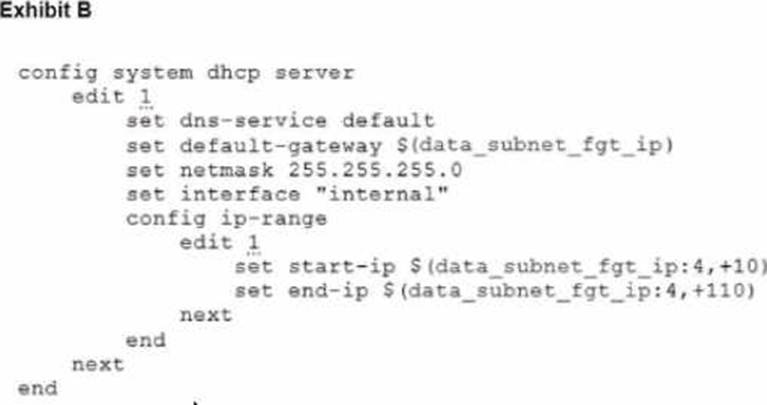
To facilitate a more efficient roll out of FortiGate devices, you are tasked with using meta fields with the CLI Template to configure the DHCP server on the "office1" FortiGate.
Given this scenario, what would be the output of the config ip-range section on the CLI Template?
A)
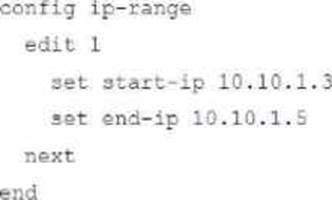
B)
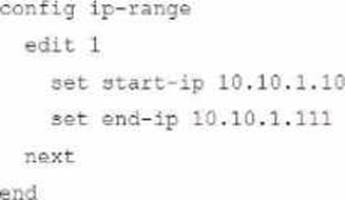
C)
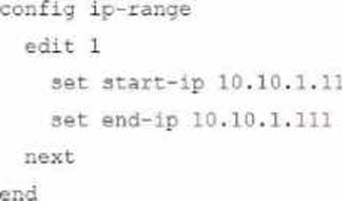
D)
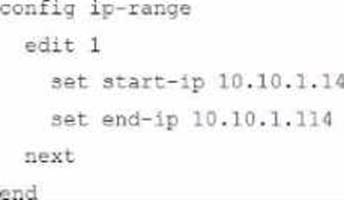
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Refer to the exhibit.

You have deployed a security fabric with three FortiGate devices as shown in the exhibit. FGT_2 has the following configuration:

FGT_1 and FGT_3 are configured with the default setting.
Which statement is true for the synchronization of fabric-objects?
- A . Objects from the FortiGate FGT_2 will be synchronized to the upstream FortiGate.
- B . Objects from the root FortiGate will only be synchronized to FGT__2.
- C . Objects from the root FortiGate will not be synchronized to any downstream FortiGate.
- D . Objects from the root FortiGate will only be synchronized to FGT_3.
D
Explanation:
https://docs.fortinet.com/document/fortigate/6.4.0/new-features/520820/improvements-to-synchronizing-objects-across-the-security-fabric-6-4-4
Refer to The exhibit showing a FortiEDR configuration.
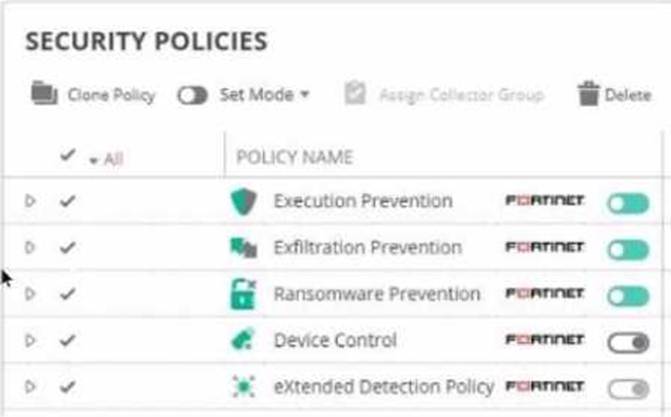
Based on the exhibit, which statement is correct?
- A . The presence of a cryptolocker malware at rest on the filesystem will be detected by the Ransomware Prevention security policy.
- B . FortiEDR Collector will not collect OS Metadata.
- C . If a malicious file is executed and attempts to establish a connection it will generate duplicate events.
- D . If an unresolved file rule is triggered, by default the file is logged but not blocked.
Refer to the exhibit, which shows a Branch1 configuration and routing table.
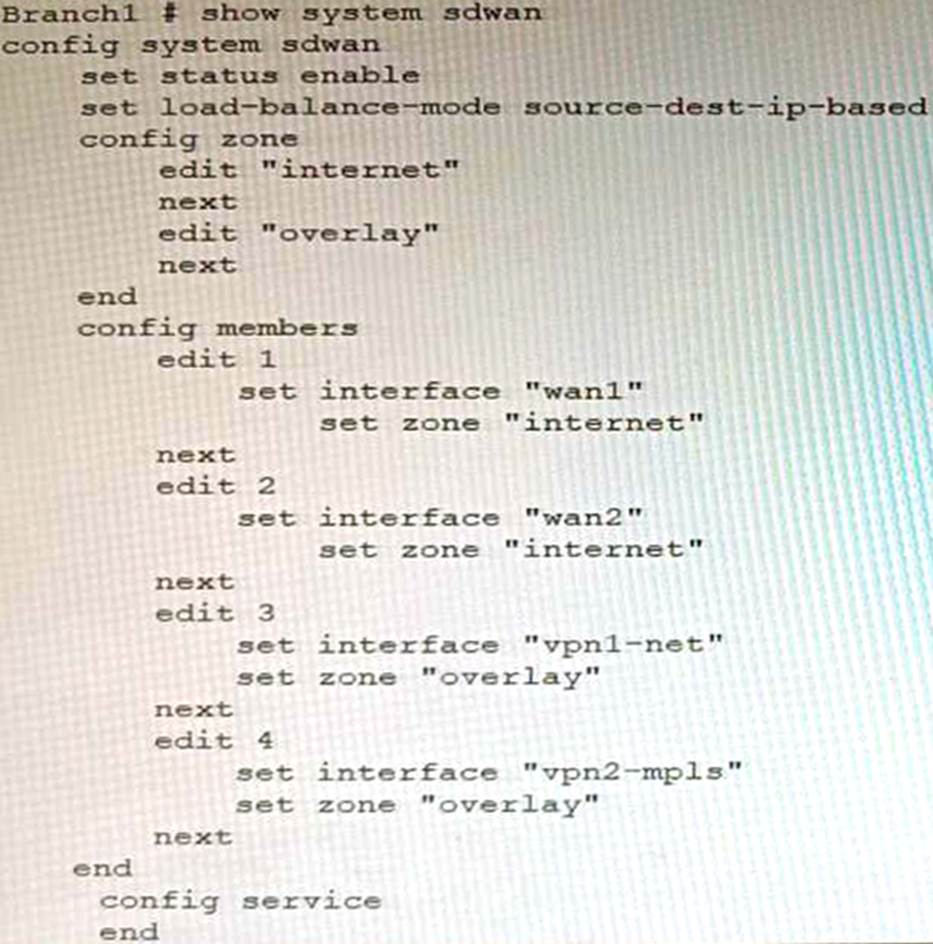
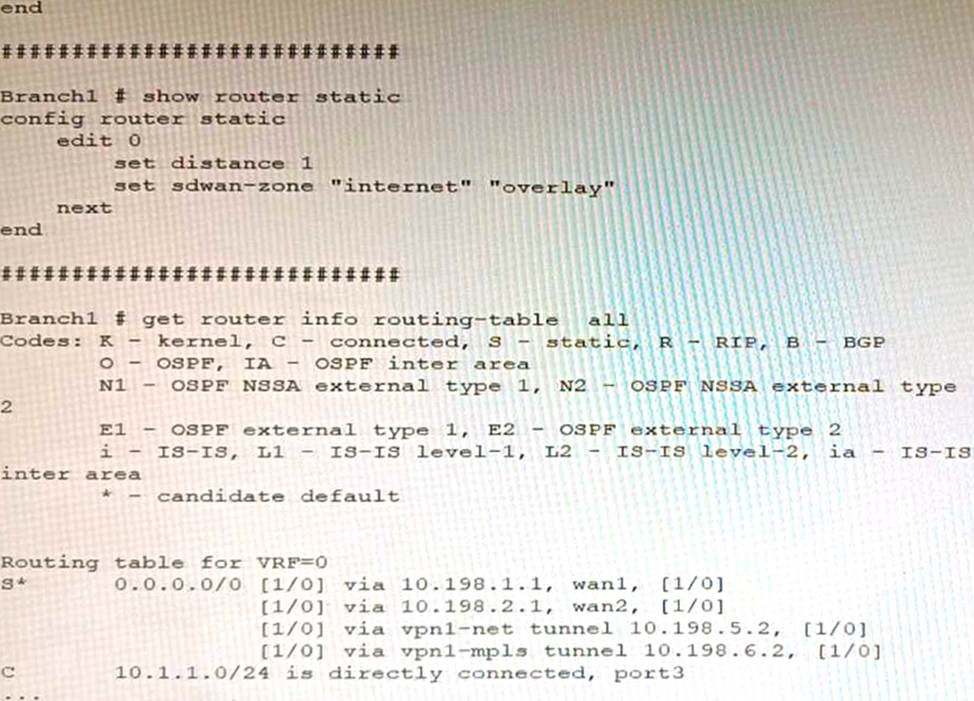
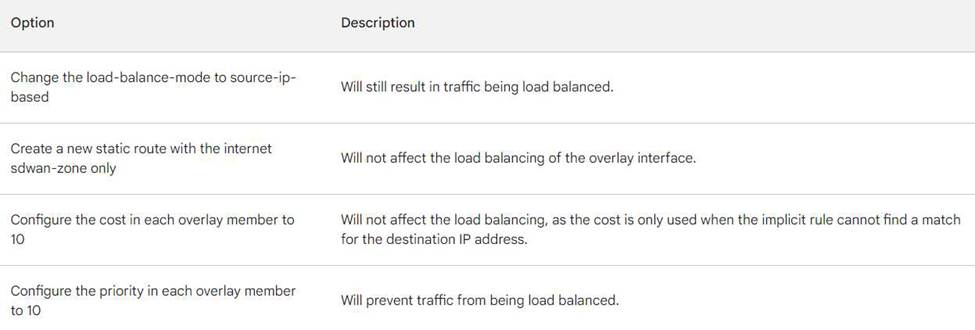
In the SD-WAN implicit rule, you do not want the traffic load balance for the overlay interface when all members are available.
In this scenario, which configuration change will meet this requirement?
- A . Change the load-balance-mode to source-ip-based.
- B . Create a new static route with the internet sdwan-zone only
- C . Configure the cost in each overlay member to 10.
- D . Configure the priority in each overlay member to 10.
D
Explanation:
The default load balancing mode for the SD-WAN implicit rule is source IP based. This means that traffic will be load balanced evenly between the overlay members, regardless of the member’s priority.
To prevent traffic from being load balanced, you can configure the priority of each overlay member to 10. This will make the member ineligible for load balancing.
The other options are not correct. Changing the load balancing mode to source-IP based will still result in traffic being load balanced. Creating a new static route with the internet sdwan-zone only will not affect the load balancing of the overlay interface. Configuring the cost in each overlay member to 10 will also not affect the load balancing, as the cost is only used when the implicit rule cannot find a match for the destination IP address.
https://docs.fortinet.com/document/fortigate/6.4.0/sd-wan-deployment-for-mssps/775385/defining-interface-members
Refer to the exhibit.
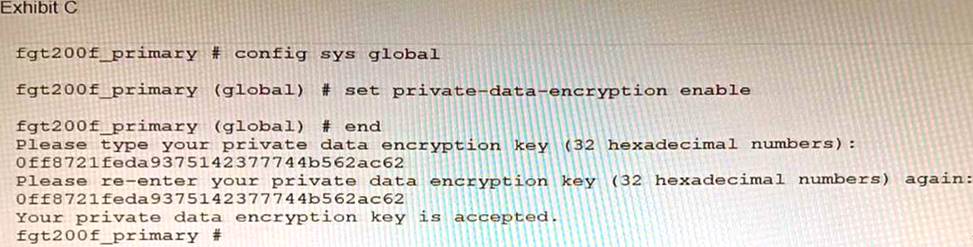
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM. Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
- A . The private-data-encryption key entered on the primary did not match the value that the TPM expected.
- B . Configuration for TPM is not synchronized between FortiGate HA cluster members.
- C . The FortiGate has not finished the auto-update process to synchronize the new configuration to FortiManager yet.
- D . TPM functionality is not yet compatible with FortiGate HA.
- E . The administrator needs to manually enter the hex private data encryption key in FortiManager.
BE
Explanation:
https://docs.fortinet.com/document/fortimanager/7.4.2/administration-guide/30332/verifying-devices-with-private-data-encryption-enabled
Refer to the exhibit.
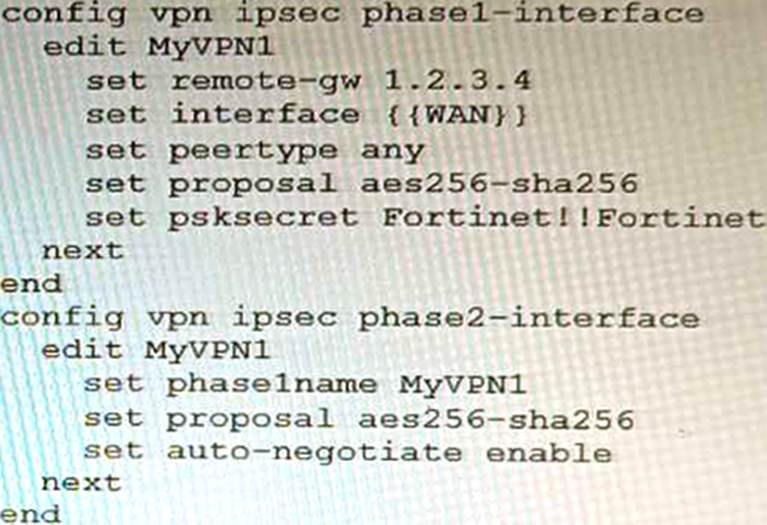
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
- A . The Jinja template will automatically map the interface with "WAN" role on the managed FortiGate.
- B . The template will work if you change the variable format to $(WAN).
- C . The template will work if you change the variable format to {{ WAN }}.
- D . The administrator must first manually map the interface for each device with a meta field.
- E . The template will fail because this configuration can only be applied with a CLI or TCL script.
DE
Explanation:
D. The administrator must first manually map the interface for each device with a meta field. The Jinja template in the exhibit is expecting a meta field called WAN to be set on the managed FortiGate. This meta field will specify which interface on the FortiGate should be assigned the "WAN" role. If the meta field is not set, then the template will fail.
E. The template will fail because this configuration can only be applied with a CLI or TCL script. The Jinja template in the exhibit is trying to configure the interface role on the managed FortiGate. This type of configuration can only be applied with a CLI or TCL script. The Jinja template will fail because it is not a valid CLI or TCL script.
Refer to the exhibits.
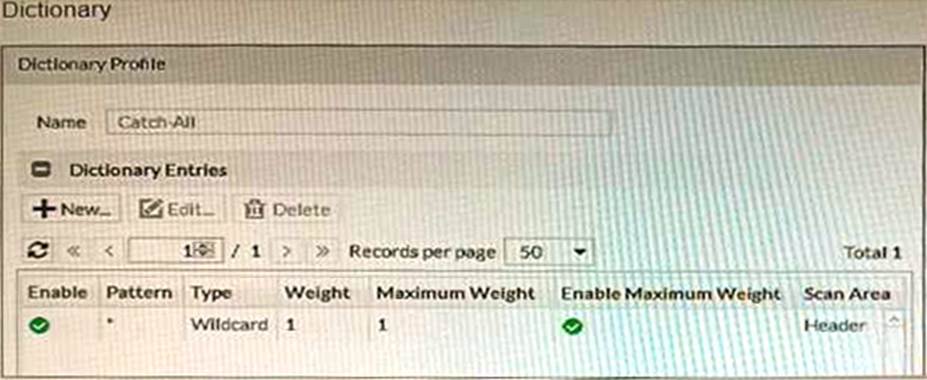
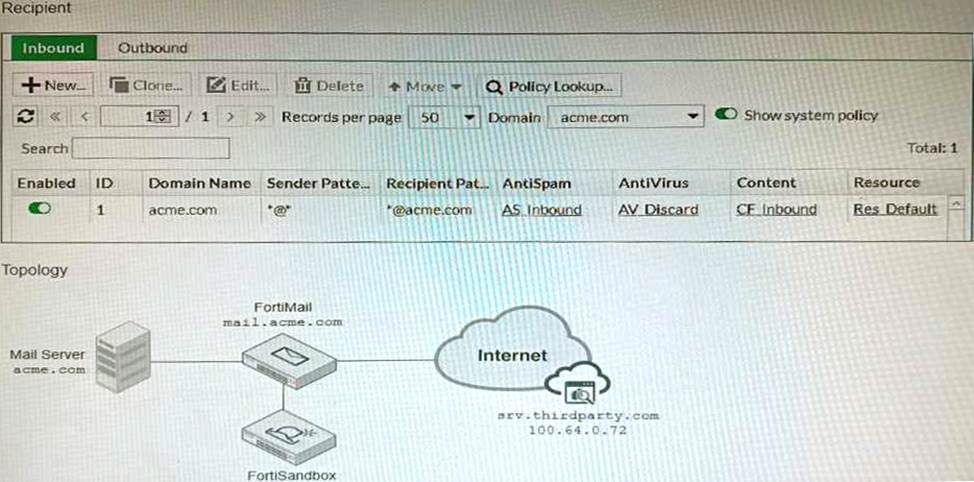
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party’s host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
- A . Change the scan order in FML-GW to antispam-sandbox-content.
- B . Apply the Catch-Ail profile to the CFInbound profile and configure a content action profile to deliver to the srv. thirdparty. com FQDN
- C . Create an access receive rule with a Sender value of srv. thirdparcy.com, Recipient value of *@acme.com, and action value of Safe
- D . Apply the Catch-AII profile to the ASinbound profile and configure an access delivery rule to deliver to the 100.64.0.72 host.
- E . Create an IP policy with a Source value of 100. 64 .0.72/32, enable precedence, and place the policy at the top of the list.
ABE
Explanation:
A is correct because the scan order must be changed to antispam-sandbox-content in order for FortiMail to scan the email for spam and viruses before forwarding it to the third-party service. B is correct because the Catch-All profile must be applied to the CFInbound profile in order for FortiMail to forward clean emails to the third-party service.
E is correct because an IP policy must be created with a Source value of 100.64.0.72/32 in order to allow emails from the third-party service to be delivered to FortiMail.
The other options are not necessary to meet the requirements.
Option C is not necessary because the access receive rule will already allow emails from the third-party service to be received by FortiMail.
Option D is not necessary because the Catch-All profile already allows emails to be delivered to any destination.
Here are some additional details about integrating a third-party service into the FortiMail email processing path:
The third-party service must be able to receive emails from FortiMail and send them back to FortiMail.
The third-party service must be able to communicate with FortiMail using the SMTP protocol.
The third-party service must be able to authenticate with FortiMail using the SMTP AUTH protocol. Once the third-party service is integrated into the FortiMail email processing path, all inbound emails will be processed by FortiMail as usual. If the email is clean, FortiMail will forward it to the third-party service. The third-party service will then send the email back to FortiMail for final delivery. FortiMail will not scan the email again.
Refer to the exhibit.
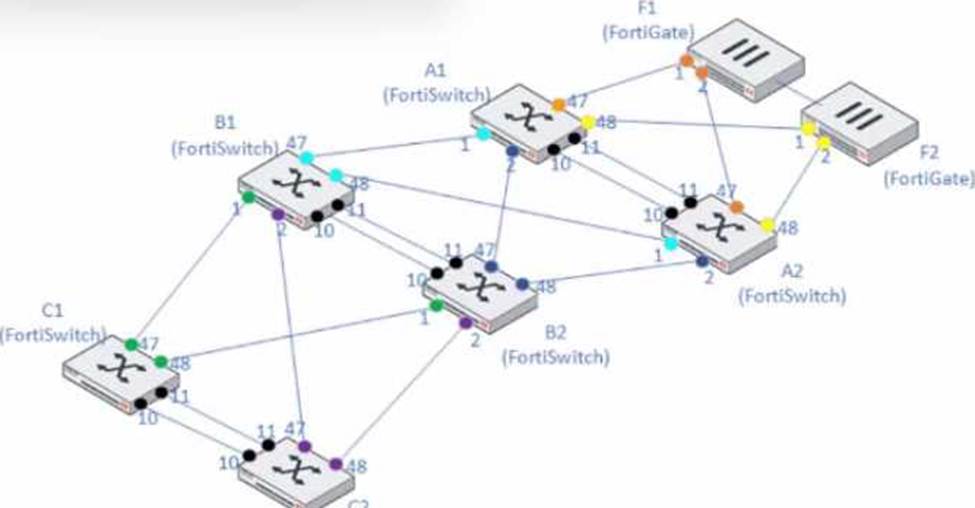
A customer needs to create a multi-tier MCLAG set up with the topology as shown in the exhibit.
A1/A2
B1/B2
C1/C2
Which command snippet should be applied to it, to allow active/active links in this topology?
A)
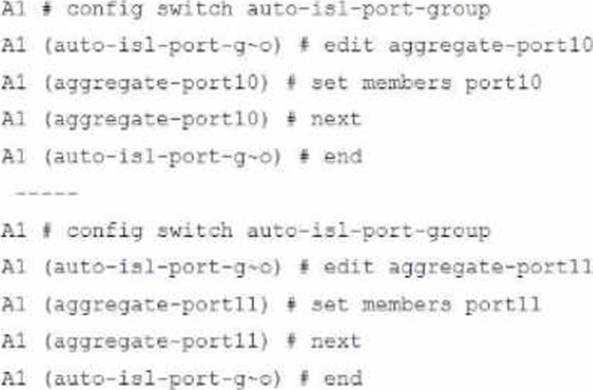
B)
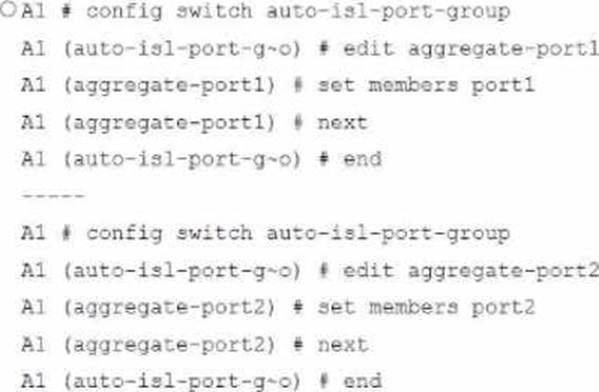
C)
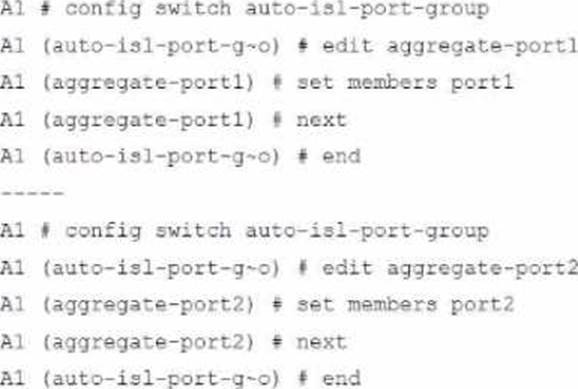
D)
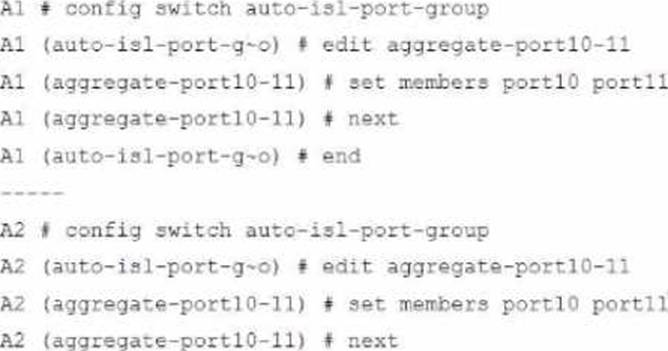
- A . Option A
- B . Option B
- C . Option C
- D . Option D
